نمونه سوالات آزمون CCNA Routing & Switching 200-120
Topic 3, IP addressing (IPv4 / IPv6)
QUESTION NO: 121
The network administrator is asked to configure 113 point-to-point links. Which IP addressing scheme defines the address range and subnet mask that meet the requirement and waste the fewest subnet and host addresses?
A. 10.10.0.0/16 subnetted with mask 255.255.255.252
B. 10.10.0.0/18 subnetted with mask 255.255.255.252
C. 10.10.1.0/24 subnetted with mask 255.255.255.252
D. 10.10.0.0/23 subnetted with mask 255.255.255.252
E. 10.10.1.0/25 subnetted with mask 255.255.255.252
Answer: D
Explanation:
We need 113 point-to-point links which equal to 113 sub-networks < 128 so we need to borrow 7 bits (because 2^7 = 128).
The network used for point-to-point connection should be /30.
So our initial network should be 30 – 7 = 23.
So 10.10.0.0/23 is the correct answer.
You can understand it more clearly when writing it in binary form:
/23 = 1111 1111.1111 1110.0000 0000
/30 = 1111 1111.1111 1111.1111 1100 (borrow 7 bits)
Topic 4, IP Routing Technologies
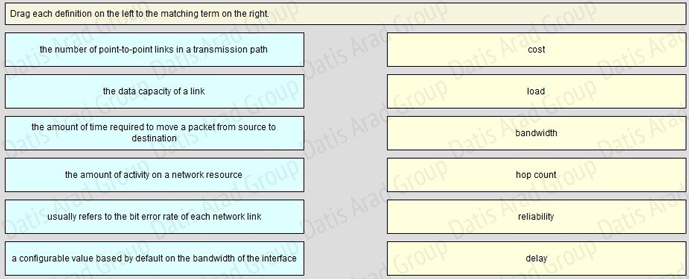
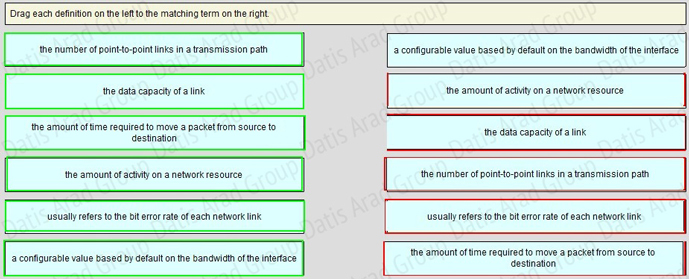
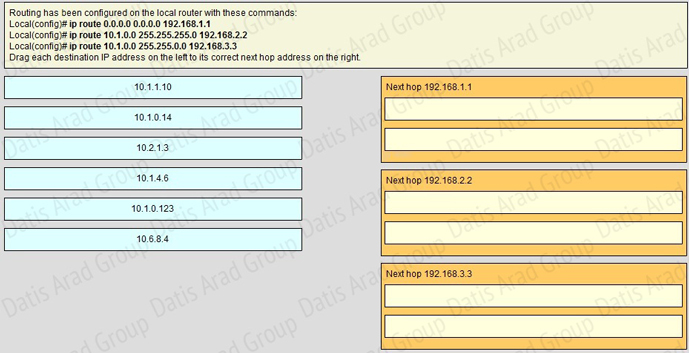
QUESTION NO: 122 Drag and Drop
Answer:
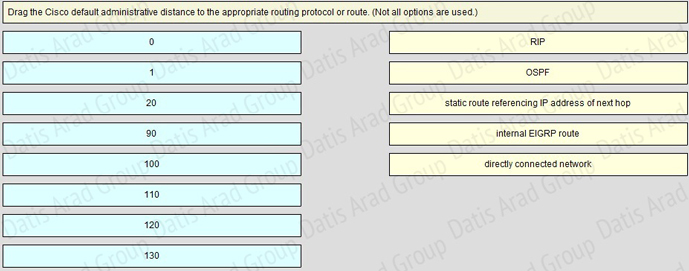
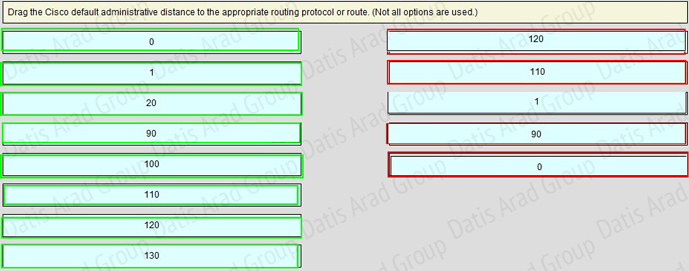
QUESTION NO: 123 Drag and Drop
Answer:
QUESTION NO: 124 Drag and Drop
Answer:
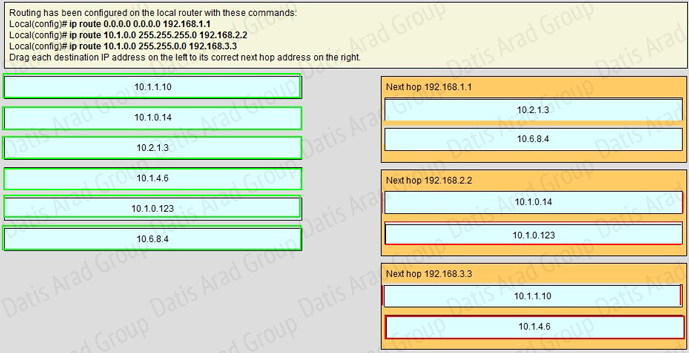
Explanation:
If we have many entries matching for next hop ip address then the router will choose the one with most specific path to send the packet. This is called the “longest match” rule, the route with the most bits in the mask set to “1 will be chosen to route packet.
QUESTION NO: 125
Which parameter or parameters are used to calculate OSPF cost in Cisco routers?
A. Bandwidth
B. Bandwidth and Delay
C. Bandwidth, Delay, and MTU
D. Bandwidth, MTU, Reliability, Delay, and Load
Answer: A
Explanation:
The well-known formula to calculate OSPF cost is
Cost = 108 / Bandwidth
QUESTION NO: 126
Why do large OSPF networks use a hierarchical design? (Choose three.)
A. to decrease latency by increasing bandwidth
B. to reduce routing overhead
C. to speed up convergence
D. to confine network instability to single areas of the network
E. to reduce the complexity of router configuration
F. to lower costs by replacing routers with distribution layer switches
Answer: B,C,D
Explanation:
FTP belongs to Application layer and it is also the highest layer of the OSI model.
QUESTION NO: 127
Which command encrypts all plaintext passwords?
A. Router# service password-encryption
B. Router(config)# password-encryption
C. Router(config)# service password-encryption
D. Router# password-encryption
Answer: C
Explanation:
The “service password-encryption” command allows you to encrypt all passwords on your router so they can not be easily guessed from your running-config. This command uses a very weak encryption because the router has to be very quickly decode the passwords for its operation. It is meant to prevent someone from looking over your shoulder and seeing the password, that is all. This is configured in global configuration mode.
QUESTION NO: 128
Which two are advantages of static routing when compared to dynamic routing? (Choose two.)
A. Configuration complexity decreases as network size increases.
B. Security increases because only the network administrator may change the routing table.
C. Route summarization is computed automatically by the router.
D. Routing tables adapt automatically to topology changes.
E. An efficient algorithm is used to build routing tables, using automatic updates.
F. Routing updates are automatically sent to neighbors.
G. Routing traffic load is reduced when used in stub network links.
Answer: B,G
Explanation:
Since static routing is a manual process, it can be argued that it is more secure (and more prone to human errors) since the network administrator will need to make changes to the routing table directly. Also, in stub networks where there is only a single uplink connection, the load is reduced as stub routers just need a single static default route, instead of many routes that all have the same next hop IP address.
QUESTION NO: 129
A network administrator needs to allow only one Telnet connection to a router. For anyone viewing the configuration and issuing the show run command, the password for Telnet access should be encrypted. Which set of commands will accomplish this task?
A. service password-encryption
access-list 1 permit 192.168.1.0 0.0.0.255
line vty 0 4
login
password cisco
access-class 1
B. enable password secret
line vty 0
login
password cisco
C. service password-encryption
line vty 1
login
password cisco
D. service password-encryption
line vty 0 4
login
password cisco
Answer: C
Explanation:
Only one VTY connection is allowed which is exactly what's requested.
Incorrect answer: command line vty0 4 would enable all 5 vty connections.
QUESTION NO: 130
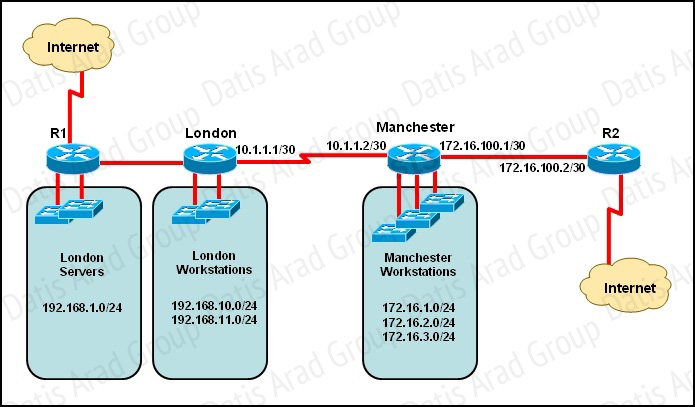
Refer to the exhibit.
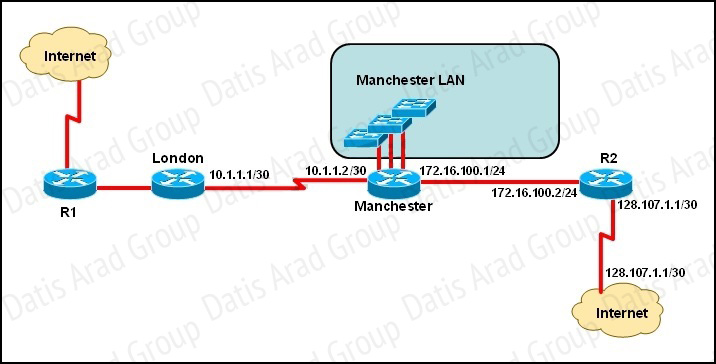
The speed of all serial links is E1 and the speed of all Ethernet links is 100 Mb/s. A static route will be established on the Manchester router to direct traffic toward the Internet over the most direct path available. What configuration on the Manchester router will establish a route toward the Internet for traffic that originates from workstations on the Manchester LAN?
A. ip route 0.0.0.0 255.255.255.0 172.16.100.2
B. ip route 0.0.0.0 0.0.0.0 128.107.1.1
C. ip route 0.0.0.0 255.255.255.252 128.107.1.1
D. ip route 0.0.0.0 0.0.0.0 172.16.100.1
E. ip route 0.0.0.0 0.0.0.0 172.16.100.2
F. ip route 0.0.0.0 255.255.255.255 172.16.100.2
Answer: E
Explanation:
We use default routing to send packets with a remote destination network not in the routing table to the next-hop router. You should generally only use default routing on stub networks—those with only one exit path out of the network. According to exhibit, all traffic towards Internet that originates from workstations should forward to Router R1.
Syntax for default route is:
ip route <Remote_Network> <Netmask> <Next_Hop_Address>.
QUESTION NO: 131
Refer to the exhibit:
The network administrator must establish a route by which London workstations can forward traffic to the Manchester workstations. What is the simplest way to accomplish this?
A. Configure a dynamic routing protocol on London to advertise all routes to Manchester.
B. Configure a dynamic routing protocol on London to advertise summarized routes to Manchester.
C. Configure a dynamic routing protocol on Manchester to advertise a default route to the London router.
D. Configure a static default route on London with a next hop of 10.1.1.1.
E. Configure a static route on London to direct all traffic destined for 172.16.0.0/22 to 10.1.1.2.
F. Configure Manchester to advertise a static default route to London.
Answer: E
Explanation:
This static route will allow for communication to the Manchester workstations and it is better to use this more specific route than a default route as traffic destined to the Internet will then not go out the London Internet connection.
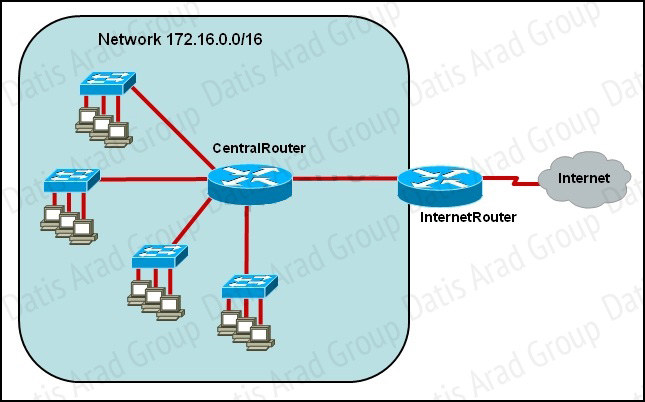
QUESTION NO: 132
Refer to the exhibit.
The network administrator requires easy configuration options and minimal routing protocol traffic. What two options provide adequate routing table information for traffic that passes between the two routers and satisfy the requests of the network administrator? (Choose two.)
A. a dynamic routing protocol on InternetRouter to advertise all routes to CentralRouter.
B. a dynamic routing protocol on InternetRouter to advertise summarized routes to CentralRouter.
C. a static route on InternetRouter to direct traffic that is destined for 172.16.0.0/16 to CentralRouter.
D. a dynamic routing protocol on CentralRouter to advertise all routes to InternetRouter.
E. a dynamic routing protocol on CentralRouter to advertise summarized routes to InternetRouter.
F. a static, default route on CentralRouter that directs traffic to InternetRouter.
Answer: C,F
Explanation:
The use of static routes will provide the necessary information for connectivity while producing no routing traffic overhead.
QUESTION NO: 133
What is the effect of using the service password-encryption command?
A. Only the enable password will be encrypted.
B. Only the enable secret password will be encrypted.
C. Only passwords configured after the command has been entered will be encrypted.
D. It will encrypt the secret password and remove the enable secret password from the configuration.
E. It will encrypt all current and future passwords.
Answer: E
Explanation:
Enable vty, console, AUX passwords are configured on the Cisco device. Use the show run command to show most passwords in clear text. If the service password-encryption is used, all the passwords are encrypted. As a result, the security of device access is improved.
QUESTION NO: 134
Refer to the exhibit.
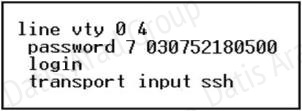
What is the effect of the configuration that is shown?
A. It configures SSH globally for all logins.
B. It tells the router or switch to try to establish an SSh connection first and if that fails to use Telnet.
C. It configures the virtual terminal lines with the password 030752180500.
D. It configures a Cisco network device to use the SSH protocol on incoming communications via the virtual terminal ports.
E. It allows seven failed login attempts before the VTY lines are temporarily shutdown.
Answer: D
Explanation:
Secure Shell (SSH) is a protocol which provides a secure remote access connection to network devices. Communication between the client and server is encrypted in both SSH version 1 and SSH version 2. If you want to prevent non-SSH connections, add the “transport input ssh” command under the lines to limit the router to SSH connections only. Straight (non-SSH) Telnets are refused.
QUESTION NO: 135
Refer to the exhibit.

What is the reason that the interface status is "administratively down, line protocol down"?
A. There is no encapsulation type configured.
B. There is a mismatch in encapsulation types.
C. The interface is not receiving any keepalives.
D. The interface has been configured with the shutdown command.
E. The interface needs to be configured as a DTE device.
F. The wrong type of cable is connected to the interface.
Answer: D
Explanation:
Interfaces can be enabled or disabled with shutdown/no shutdown command. If you interface is down, it will display administratively down status. You can bring up an interface having administratively down interface using no shutdown command.
QUESTION NO: 136
Refer to the exhibit.
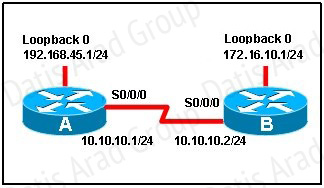
When running OSPF, what would cause router A not to form an adjacency with router B?
A. The loopback addresses are on different subnets.
B. The values of the dead timers on the routers are different.
C. Route summarization is enabled on both routers.
D. The process identifier on router A is different than the process identifier on router B.
Answer: B
Explanation:
To form an adjacency (become neighbor), router A & B must have the same Hello interval, Dead interval and AREA numbers
QUESTION NO: 137
A router has learned three possible routes that could be used to reach a destination network. One route is from EIGRP and has a composite metric of 20514560. Another route is from OSPF with a metric of 782. The last is from RIPv2 and has a metric of 4. Which route or routes will the router install in the routing table?
A. the OSPF route
B. the EIGRP route
C. the RIPv2 route
D. all three routes
E. the OSPF and RIPv2 routes
Answer: B
Explanation:
When one route is advertised by more than one routing protocol, the router will choose to use the routing protocol which has lowest Administrative Distance. The Administrative Distances of popular routing protocols are listed below:
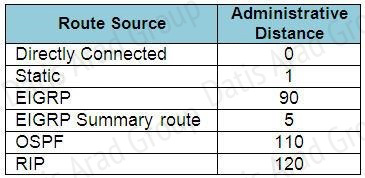
QUESTION NO: 138
Refer to the exhibit.
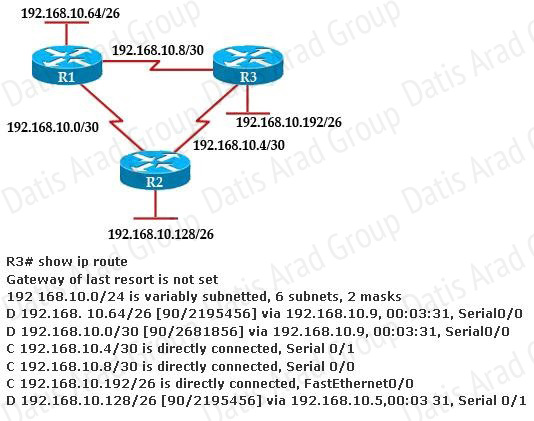
The company uses EIGRP as the routing protocol. What path will packets take from a host on the 192.168.10.192/26 network to a host on the LAN attached to router R1?
A. The path of the packets will be R3 to R2 to R1.
B. The path of the packets will be R3 to R1 to R2.
C. The path of the packets will be both R3 to R2 to R1 AND R3 to R1.
D. The path of the packets will be R3 to R1.
Answer: D
Explanation:
Host on the LAN attached to router R1 belongs to 192.168.10.64/26 subnet. From the output of the routing table of R3 we learn this network can be reach via 192.168.10.9, which is an IP address in 192.168.10.8/30 network (the network between R1 & R3) -> packets destined for 192.168.10.64 will be routed from R3 -> R1 -> LAN on R1.
QUESTION NO: 139
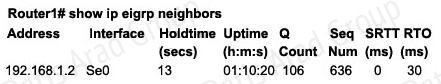
A network administrator is troubleshooting an EIGRP problem on a router and needs to confirm the IP addresses of the devices with which the router has established adjacency. The retransmit interval and the queue counts for the adjacent routers also need to be checked. What command will display the required information?
A. Router# show ip eigrp adjacency
B. Router# show ip eigrp topology
C. Router# show ip eigrp interfaces
D. Router# show ip eigrp neighbors
Answer: D
Explanation:
Below is an example of the show ip eigrp neighbors command. The retransmit interval (Smooth Round Trip Timer – SRTT) and the queue counts (Q count, which shows the number of queued EIGRP packets) for the adjacent routers are listed:
QUESTION NO: 140
Refer to the graphic.
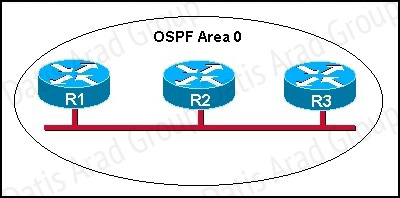
R1 is unable to establish an OSPF neighbor relationship with R3. What are possible reasons for this problem? (Choose two.)
A. All of the routers need to be configured for backbone Area 1.
B. R1 and R2 are the DR and BDR, so OSPF will not establish neighbor adjacency with R3.
C. A static route has been configured from R1 to R3 and prevents the neighbor adjacency from being established.
D. The hello and dead interval timers are not set to the same values on R1 and R3.
E. EIGRP is also configured on these routers with a lower administrative distance.
F. R1 and R3 are configured in different areas.
Answer: D,F
Explanation:
This question is to examine the conditions for OSPF to create neighborhood. So as to make the two routers become neighbors, each router must be matched with the following items:
1. The area ID and its types;
2. Hello and failure time interval timer;
3. OSPF Password (Optional);