نمونه سوالات آزمون CCNA Routing & Switching 200-120
Topic 9, Mix Questions Set
QUESTION NO: 341
What are the alert messages generated by SNMP agents called?
A. TRAP
B. INFORM
C. GET
D. SET
Answer: A,B
Explanation:
A TRAP is a SNMP message sent from one application to another (which is typically on a remote host). Their purpose is merely to notify the other application that something has happened, has been noticed, etc. The big problem with TRAPs is that they’re unacknowledged so you don’t actually know if the remote application received your oh-so-important message to it. SNMPv2 PDUs fixed this by introducing the notion of an INFORM, which is nothing more than an acknowledged TRAP.
QUESTION NO: 342
What are the benefits of using Netflow? (Choose three.)
A. Network,Application & User Monitoring
B. Network Planning
C. Security Analysis
D. Accounting/Billing
Answer: A,C,D
Explanation:
NetFlow traditionally enables several key customer applications including:
+ Network Monitoring – NetFlow data enables extensive near real time network monitoring capabilities. Flow-based analysis techniques may be utilized to visualize traffic patterns associated with individual routers and switches as well as on a network-wide basis (providing aggregate traffic or application based views) to provide proactive problem detection, efficient troubleshooting, and rapid problem resolution.
+ Application Monitoring and Profiling – NetFlow data enables network managers to gain a detailed, time-based, view of application usage over the network. This information is used to plan, understand new services, and allocate network and application resources (e.g. Web server sizing and VoIP deployment) to responsively meet customer demands.
+ User Monitoring and Profiling – NetFlow data enables network engineers to gain detailed understanding of customer/user utilization of network and application resources. This information may then be utilized to efficiently plan and allocate access, backbone and application resources as well as to detect and resolve potential security and policy violations.
+ Network Planning – NetFlow can be used to capture data over a long period of time producing the opportunity to track and anticipate network growth and plan upgrades to increase the number of routing devices, ports, or higher- bandwidth interfaces. NetFlow services data optimizes network planning including peering, backbone upgrade planning, and routing policy planning. NetFlow helps to minimize the total cost of network operations while maximizing network performance, capacity, and reliability. NetFlow detects unwanted WAN traffic, validates bandwidth and Quality of Service (QOS) and allows the analysis of new network applications. NetFlow will give you valuable information to reduce the cost of operating your network.
+ Security Analysis – NetFlow identifies and classifies DDOS attacks, viruses and worms in realtime. Changes in network behavior indicate anomalies that are clearly demonstrated in NetFlow data. The data is also a valuable forensic tool to understand and replay the history of security incidents.
+ Accounting/Billing – NetFlow data provides fine-grained metering (e.g. flow data includes details such as IP addresses, packet and byte counts, timestamps, type-of-service and application ports, etc.) for highly flexible and detailed resource utilization accounting. Service providers may utilize the information for billing based on time-of-day, bandwidth usage, application usage, quality of service, etc. Enterprise customers may utilize the information for departmental charge-back or cost allocation for resource utilization.
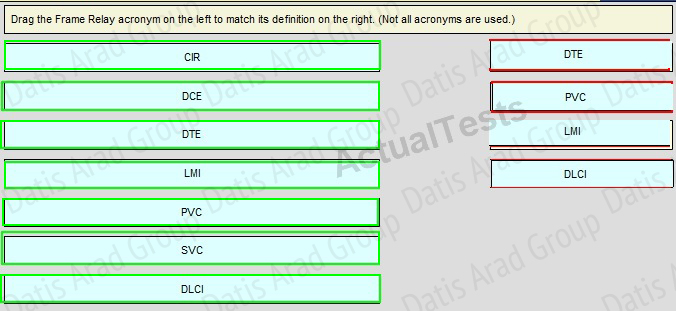
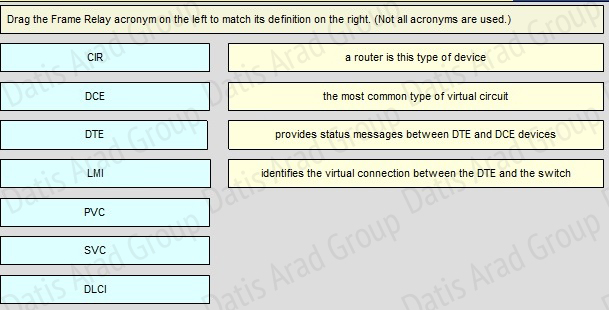
QUESTION NO: 343 Drag and Drop
Drag the Frame Relay acronym on the left to match its definition on the right. (Not all acronyms are used.)
Answer:
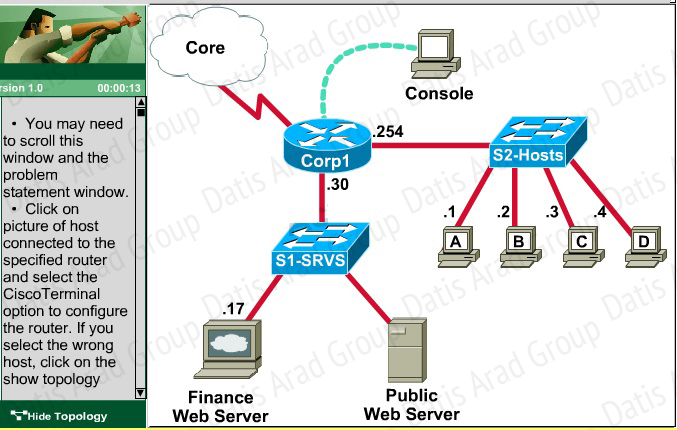
QUESTION NO 344: Scenario
A corporation wants to add security to its network. The requirements are:
Host B should be able to use a web browser (HTTP) to access the Finance Web Server.
Other types of access from host B to theFinance Web Server should be blocked.
All access from hosts in the Core or local LAN to the Finance Web Server should be blocked.
All hosts in the Core and on local LAN should be able to access the Public Web Server.
You have been tasked to create and apply a numbered access list to a single outbound interface. This access list can contain no more than three statements that meet these requirements.
Access to the router CLI can be gained by clicking on the appropriate host.
All passwords have been temporarily set to “cisco”.
The Core connection uses an IP address of 198.18.132.65.
The computers in the Hosts LAN have been assigned addresses of 192.168.201.1 – 192.168.201.254.
host A 192.168.201.1
host B 192.168.201.2
host C 192.168.201.3
host D 192.168.201.4
The Finance Web Server has been assigned an address of 172.22.237.17.
The Public Web Server in the Server LAN has been assigned an addressof 172.22.237.18.
Answer:
Explanation:
We should create an access-list andapply it to the interface thatis connected to the Server LAN because it canfilter out traffic from both S2 and Core networks.To see which interface this is, use the “show ip interface brief” command:
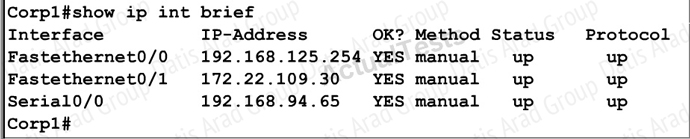
From this, we know that the servers are located on the fa0/1 interface, so we will place our numbered access list here in the outbound direction.
Corp1#configure terminal
Our access-list needs to allow host B – 192.168125.2to theFinance Web Server 172.22.109.17 via HTTP(port 80), so our first line is this:
Corp1(config)#access-list 100 permit tcp host 192.168.125.2 host 172.22.109.17eq 80
Then, our next two instructions are these:
This can be accomplished with one command (which we need to do as our ACL needs to be no more than 3 lines long), blocking all other access to the finance web server:
Corp1(config)#access-list 100 deny ip any host 172.22.109.17
Our last instruction is to allow allhosts in the Core and onthe local LANaccesstothe PublicWeb Server (172.22.109.18)
Corp1(config)#access-list 100 permit ip host 172.22.109.18 any
Finally, apply this access-list to Fa0/1 interface (outbound direction)
Corp1(config)#interface fa0/1
Corp1(config-if)#ip access-group 100 out
Notice: We have to apply the access-list to Fa0/1 interface (not Fa0/0 interface) so that the access-list can filter traffic coming from both theLAN and the Core networks. To verify, just click on host Bto open its web browser. In the address box type http://172.22.109.17 to check if you are allowed to access Finance Web Server or not. If your configuration is correct then you can access it.
Click on other hosts (A, Cand D) and check to make sure you can’t access Finance Web Server from these hosts. Then, repeat to make sure they can reach the public server at 172.22.109.18. Finally, save the configuration
Corp1(config-if)#end
Corp1#copy running-config startup-config
QUESTION NO: 345
If a router has four interfaces and each interface is connected to four switches, how many broadcast domains are present on the router?
A. 1
B. 2
C. 4
D. 8
Answer: C
QUESTION NO: 346
Which command can you use to set the hostname on a switch?
A. switch-mdf-c1(config)#hostname switch-mdf1
B. switch-mdf-c1>hostname switch-mdf1
C. switch-mdf-c1#hostname switch-mdf1
D. switch-mdf-c1(config-if)#hostname switch-mdf1
Answer: A
QUESTION NO: 347
If the primary root bridge experiences a power loss, which switch takes over?
A. switch 0004.9A1A.C182
B. switch 00E0.F90B.6BE3
C. switch 00E0.F726.3DC6
D. switch 0040.0BC0.90C5
Answer: A
QUESTION NO: 348
Which IPv6 header field is equivalent to the TTL?
A. Hop Limit
B. Flow Label
C. TTD
D. Hop Count
E. Scan Timer
Answer: A
QUESTION NO: 349
Which two statements about the tunnel mode ipv6ip command are true? (Choose two.)
A. It enables the transmission of IPv6 packets within the configured tunnel.
B. It specifies IPv4 as the encapsulation protocol.
C. It specifies IPv6 as the encapsulation protocol.
D. It specifies IPv6 as the transport protocol.
E. It specifies that the tunnel is a Teredo tunnel.
Answer: A,B
QUESTION NO: 350
What is the correct routing match to reach 172.16.1.5/32?
A. 172.16.1.0/26
B. 172.16.1.0/25
C. 172.16.1.0/24
D. the default route
Answer: A
QUESTION NO: 351
Which step in the router boot process searches for an IOS image to load into the router?
A. bootstrap
B. POST
C. mini-IOS
D. ROMMON mode
Answer: A
QUESTION NO: 352
Which command can you enter to route all traffic that is destined for 192.168.0.0/20 to a specific interface?
A. router(config)#ip route 192.168.0.0 255.255.240.0 GigabitEthernet0/1
B. router(config)#ip route 0.0.0.0 255.255.255.0 GigabitEthernet0/1
C. router(config)#ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/1
D. router(config)#ip route 192.168.0.0 255.255.255.0 GigabitEthernet0/1
Answer: A
QUESTION NO: 353
Which technology allows a large number of private IP addresses to be represented by a smaller number of public IP addresses?
A. NAT
B. NTP
C. RFC 1631
D. RFC 1918
Answer: A
QUESTION NO: 354
What is the effect of the overload keyword in a static NAT translation configuration?
A. It enables port address translation.
B. It enables the use of a secondary pool of IP addresses when the first pool is depleted.
C. It enables the inside interface to receive traffic.
D. It enables the outside interface to forward traffic.
Answer: A
QUESTION NO: 35 5
Which protocol advertises a virtual IP address to facilitate transparent failover of a Cisco routing device?
A. FHRP
B. DHCP
C. RSMLT
D. ESRP
Answer: A
QUESTION NO: 356
What are three broadband wireless technologies? (Choose three.)
A. WiMax
B. satellite Internet
C. municipal Wi-Fi
D. site-to-site VPN
E. DSLAM
F. CMTS
Answer: A,B,C
QUESTION NO: 357
Which condition indicates that service password-encryption is enabled?
A. The local username password is encrypted in the configuration.
B. The enable secret is encrypted in the configuration.
C. The local username password is in clear text in the configuration.
D. The enable secret is in clear text in the configuration.
Answer: A
QUESTION NO: 358
Which two spanning-tree port states does RSTP combine to allow faster convergence? (Choose two.)
A. blocking
B. listening
C. learning
D. forwarding
E. discarding
Answer: A,B
QUESTION NO: 359
Which technology can enable multiple VLANs to communicate with one another?
A. inter-VLAN routing using a Layer 3 switch
B. inter-VLAN routing using a Layer 2 switch
C. intra-VLAN routing using router on a stick
D. intra-VLAN routing using a Layer 3 switch
Answer: A
QUESTION NO: 360
In which three ways is an IPv6 header simpler than an IPv4 header? (Choose three.)
A. Unlike IPv4 headers, IPv6 headers have a fixed length.
B. IPv6 uses an extension header instead of the IPv4 Fragmentation field.
C. IPv6 headers eliminate the IPv4 Checksum field.
D. IPv6 headers use the Fragment Offset field in place of the IPv4 Fragmentation field.
E. IPv6 headers use a smaller Option field size than IPv4 headers.
F. IPv6 headers use a 4-bit TTL field, and IPv4 headers use an 8-bit TTL field.