نمونه سوالات آزمون CCNA Routing & Switching 200-120
Topic 9, Mix Questions Set
QUESTION NO: 301
Syslog was configured with a level 3 trap. Which 3 types of logs would be generated (choose four)
A. Emergencies
B. Alerts
C. Critical
D. Errors
E. Warnings
Answer: A,B,C,D
Explanation:
The Message Logging is divided into 8 levels as listed below:
Level Keyword Description
0 emergencies System is unusable
1 alerts Immediate action is needed
2 critical Critical conditions exist
3 errors Error conditions exist
4 warnings Warning conditions exist
5 notification Normal, but significant, conditions exist
6 informational Informational messages
7 debugging Debugging messages
The highest level is level 0 (emergencies). The lowest level is level 7. If you specify a level with the “logging console level” command, that level and all the higher levels will be displayed. For example, by using the “logging console warnings” command, all the logging of emergencies, alerts, critical, errors, warnings will be displayed.
QUESTION NO: 302
What are the benefit of using Netflow? (Choose three.)
A. Network, Application & User Monitoring
B. Network Planning
C. Security Analysis
D. Accounting/Billing
Answer: A,C,D
Explanation:
NetFlow traditionally enables several key customer applications including:
Network Monitoring – NetFlow data enables extensive near real time network monitoring capabilities. Flow-based analysis techniques may be utilized to visualize traffic patterns associated with individual routers and switches as well as on a network-wide basis (providing aggregate traffic or application based views) to provide proactive problem detection, efficient troubleshooting, and rapid problem resolution.
Application Monitoring and Profiling – NetFlow data enables network managers to gain a detailed, time-based, view of application usage over the network. This information is used to plan, understand new services, and allocate network and application resources (e.g. Web server sizing and VoIP deployment) to responsively meet customer demands.
User Monitoring and Profiling – NetFlow data enables network engineers to gain detailed understanding of customer/user utilization of network and application resources. This information may then be utilized to efficiently plan and allocate access, backbone and application resources as well as to detect and resolve potential security and policy violations.
Network Planning – NetFlow can be used to capture data over a long period of time producing the opportunity to track and anticipate network growth and plan upgrades to increase the number of routing devices, ports, or higher- bandwidth interfaces. NetFlow services data optimizes network planning including peering, backbone upgrade planning, and routing policy planning. NetFlow helps to minimize the total cost of network operations while maximizing network performance, capacity, and reliability. NetFlow detects unwanted WAN traffic, validates bandwidth and Quality of Service (QOS) and allows the analysis of new network applications. NetFlow will give you valuable information to reduce the cost of operating your network.
Security Analysis – NetFlow identifies and classifies DDOS attacks, viruses and worms in realtime. Changes in network behavior indicate anomalies that are clearly demonstrated in NetFlow data. The data is also a valuable forensic tool to understand and replay the history of security incidents.
Accounting/Billing – NetFlow data provides fine-grained metering (e.g. flow data includes details such as IP addresses, packet and byte counts, timestamps, type-of-service and application ports, etc.) for highly flexible and detailed resource utilization accounting. Service providers may utilize the information for billing based on time-of-day, bandwidth usage, application usage, quality of service, etc. Enterprise customers may utilize the information for departmental charge-back or cost allocation for resource utilization.
QUESTION NO: 303
Which protocol can cause overload on a CPU of a managed device?
A. Netflow
B. WCCP
C. IP SLA
D. SNMP
Answer: D
Explanation:
Sometimes, messages like this might appear in the router console:
%SNMP-3-CPUHOG: Processing [chars] of [chars]
They mean that the SNMP agent on the device has taken too much time to process a request. You can determine the cause of high CPU use in a router by using the output of the show process cpu command.
Note: A managed device is a part of the network that requires some form of monitoring and management (routers, switches, servers, workstations, printers…).
QUESTION NO: 304
What are the three things that the Netflow uses to consider the traffic to be in a same flow? (Choose three)
A. IP address
B. Interface name
C. Port numbers
D. L3 protocol type
E. MAC address
Answer: A,C,D
Explanation:
What is an IP Flow?
Each packet that is forwarded within a router or switch is examined for a set of IP packet attributes. These attributes are the IP packet identity or fingerprint of the packet and determine if the packet is unique or similar to other packets. Traditionally, an IP Flow is based on a set of 5 and up to 7 IP packet attributes. IP Packet attributes used by NetFlow:
+ IP source address
+ IP destination address
+ Source port
+ Destination port
+ Layer 3 protocol type
+ Class of Service
+ Router or switch interface
QUESTION NO: 305
What is the alert message generated by SNMP agents called ?
A. TRAP
B. INFORM
C. GET
D. SET
Answer: A,B
Explanation:
A TRAP is a SNMP message sent from one application to another (which is typically on a remote host). Their purpose is merely to notify the other application that something has happened, has been noticed, etc. The big problem with TRAPs is that they’re unacknowledged so you don’t actually know if the remote application received your oh-so-important message to it. SNMPv2 PDUs fixed this by introducing the notion of an INFORM, which is nothing more than an acknowledged TRAP.
QUESTION NO: 306
Which three features are added in SNMPv3 over SNMPv2?
A. Message Integrity
B. Compression
C. Authentication
D. Encryption
E. Error Detection
Answer: A,C,D
Explanation:
Cisco IOS software supports the following versions of SNMP:
SNMPv1 – The Simple Network Management Protocol: A Full Internet Standard, defined in RFC 1157. (RFC 1157 replaces the earlier versions that were published as RFC 1067 and RFC 1098.) Security is based on community strings.
SNMPv2c – The community-string based Administrative Framework for SNMPv2. SNMPv2c (the “c” stands for “community”) is an Experimental Internet Protocol defined in RFC 1901, RFC 1905, and RFC 1906. SNMPv2c is an update of the protocol operations and data types of SNMPv2p (SNMPv2 Classic), and uses the community-based security model of SNMPv1.
SNMPv3 – Version 3 of SNMP. SNMPv3 is an interoperable standards-based protocol defined in RFCs 2273 to 2275. SNMPv3 provides secure access to devices by a combination of authenticating and encrypting packets over the network. The security features provided in SNMPv3 are as follows:
– Message integrity: Ensuring that a packet has not been tampered with in transit.
– Authentication: Determining that the message is from a valid source.
– Encryption: Scrambling the contents of a packet prevent it from being learned by an unauthorized source.
QUESTION NO: 307
In a GLBP network, who is responsible for the arp request?
A. AVF
B. AVG
C. Active Router
D. Standby Router
Answer: B
Explanation:
Members of a GLBP group elect one gateway to be the active virtual gateway (AVG) for that group. Other group members provide backup for the AVG in the event that the AVG becomes unavailable. The AVG assigns a virtual MAC address to each member of the GLBP group. Each gateway assumes responsibility for forwarding packets sent to the virtual MAC address assigned to it by the AVG. These gateways are known as active virtual forwarders (AVFs) for their virtual MAC address.
The AVG is responsible for answering Address Resolution Protocol (ARP) requests for the virtual IP address. Load sharing is achieved by the AVG replying to the ARP requests with different virtual MAC addresses.
QUESTION NO: 308
What levels will be trapped if the administrator executes the command
router(config)# logging trap 4 (Choose four)
A. Emergency
B. Notice
C. Alert
D. Error
E. Warning
Answer: A,C,D,E
Explanation:
The Message Logging is divided into 8 levels as listed below:
Level Keyword Description
0 emergencies System is unusable
1 alerts Immediate action is needed
2 critical Critical conditions exist
3 errors Error conditions exist
4 warnings Warning conditions exist
5 notification Normal, but significant, conditions exist
6 informational Informational messages
7 debugging Debugging messages
If you specify a level with the “logging trap level” command, that level and all the higher levels will be logged. For example, by using the “logging trap 4 command, all the logging of emergencies, alerts, critical, errors, warnings will be logged.
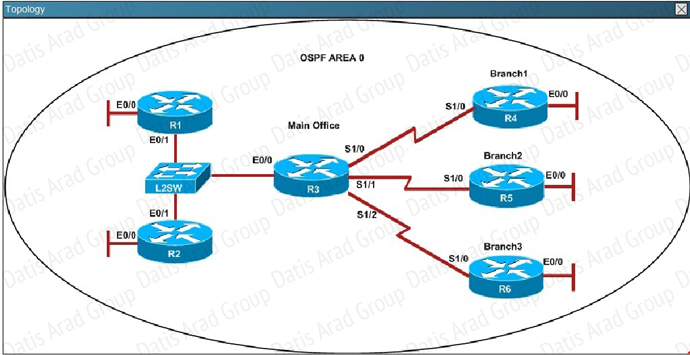
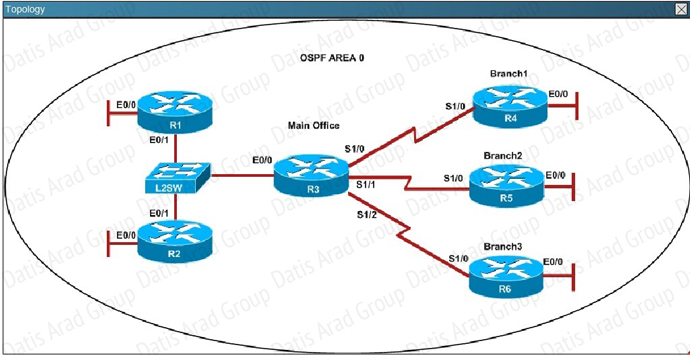
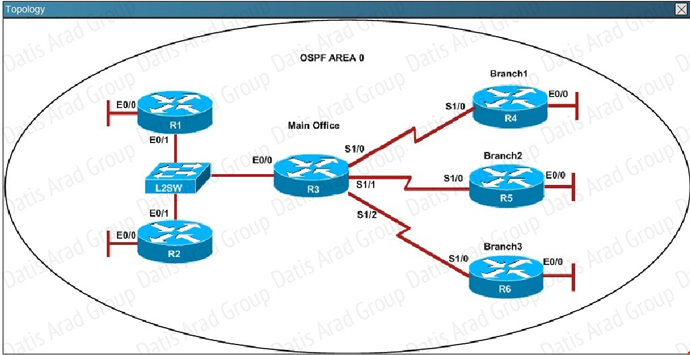
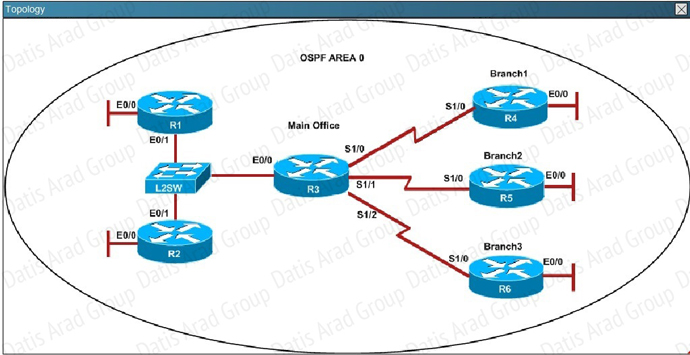
QUESTION NO: 309 Scenario
Refer to the topology. Your company has decided to connect the main office with three other
remote branch offices using point-to-point serial links.
You are required to troubleshoot and resolve OSPF neighbor adjacency issues between the main
office and the routers located in the remote branch offices.
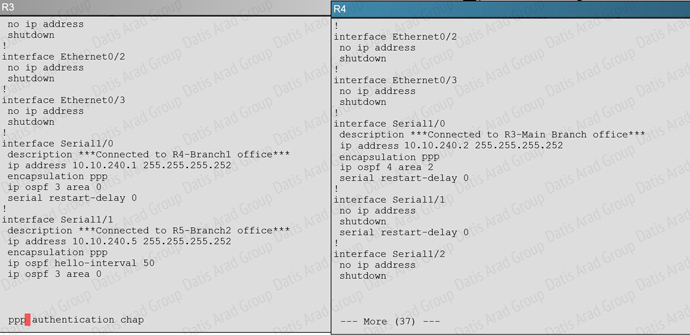
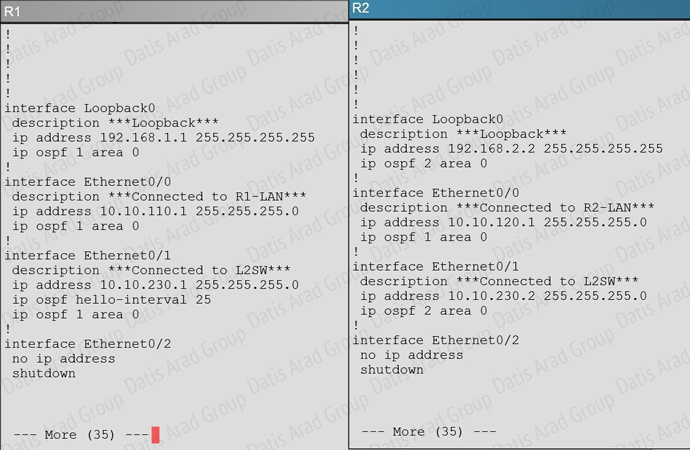
An OSPF neighbor adjacency is not formed between R3 in the main office and R4 in the Branchl office. What is causing the problem?
A. There is an area ID mismatch.
B. There is a Layer 2 issue; an encapsulation mismatch on serial links.
C. There is an OSPF hello and dead interval mismatch.
D. The R3 router ID is configured on R4.
Answer: A
Explanation:
A show running-config command on R3 and R4 shows that R4 is incorrectly configured for area 2:
QUESTION NO: 310 Scenario
Refer to the topology. Your company has decided to connect the main office with three other remote branch offices using point-to-point serial links. You are required to troubleshoot and resolve OSPF neighbor adjacency issues between the main office and the routers located in the remote branch offices.
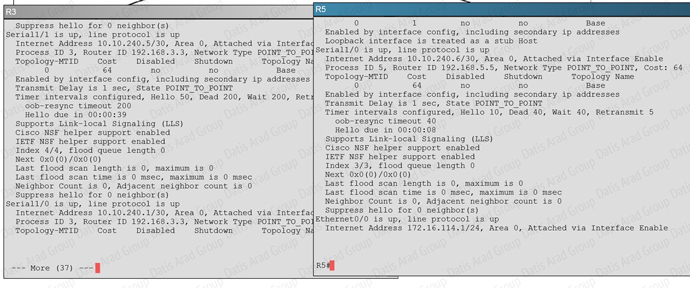
An OSPF neighbor adjacency is not formed between R3 in the main office and R5 in the Branch2 office. What is causing the problem?
A. There is an area ID mismatch.
B. There is a PPP authentication issue; a password mismatch.
C. There is an OSPF hello and dead interval mismatch.
D. There is a missing network command in the OSPF process on R5.
Answer: C
Explanation:
The “show ip ospf interface command on R3 and R5 shows that the hello and dead intervals do not match. They are 50 and 200 on R3 and 10 and 40 on R5.
QUESTION NO: 311 Scenario
Refer to the topology. Your company has decided to connect the main office with three other remote branch offices using point-to-point serial links. You are required to troubleshoot and resolve OSPF neighbor adjacency issues between the main office and the routers located in the remote branch offices.
R1 does not form an OSPF neighbor adjacency with R2. Which option would fix the issue?
A. R1 ethernetO/1 is shutdown. Configure no shutdown command.
B. R1 ethernetO/1 configured with a non-default OSPF hello interval of 25: configure no ip ospf hello-interval 25
C. R2 ethernetO/1 and R3 ethernetO/O are configured with a non-default OSPF hello interval of 25; configure no ip ospf hello-interval 25
D. Enable OSPF for R1 ethernetO/1; configure ip ospf 1 area 0 command under ethernetO/1
Answer: B
Explanation:
Looking at the configuration of R1, we see that R1 is configured with a hello interval of 25 on interface Ethernet 0/1 while R2 is left with the default of 10 (not configured).
QUESTION NO: 312 Scenario
Refer to the topology. Your company has decided to connect the main office with three other remote branch offices using point-to-point serial links. You are required to troubleshoot and resolve OSPF neighbor adjacency issues between the main office and the routers located in the remote branch offices.
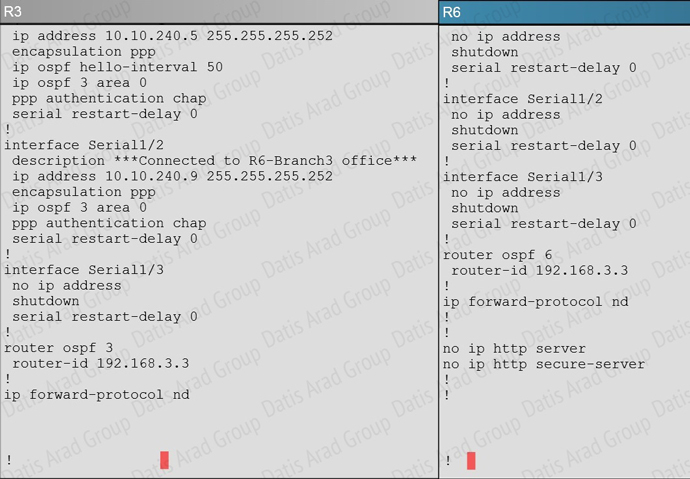
An OSPF neighbor adjacency is not formed between R3 in the main office and R6 in the Branch3 office. What is causing the problem?
A. There is an area ID mismatch.
B. There is a PPP authentication issue; the username is not configured on R3 and R6.
C. There is an OSPF hello and dead interval mismatch.
D. The R3 router ID is configured on R6.
Answer: D
Explanation:
Using the show running-config command we see that R6 has been incorrectly configured with the same router ID as R3 under the router OSPF process.
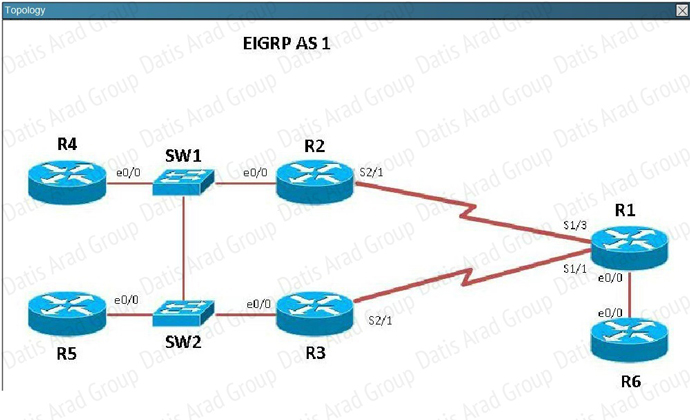
QUESTION NO: 313 Scenario
Refer to the topology. Your company has connected the routers R1. R2. and R3 with serial links.
R2 and R3 are connected to the switches SW1 and SW2, respectively. SW1 and SW2 are also connected to the routers R4 and R5.
The EIGRP routing protocol is configured. You are required to troubleshoot and resolve the EIGRP issues between the various routers. Use the appropriate show commands to troubleshoot the issues.
The loopback interfaces on R4 with the IP addresses of 10.4.4.4 /32, 10.4.4.5/32. and 10.4.4.6/32 are not appearing in the routing table of R5 Why are the interfaces missing?
A. The interfaces are shutdown, so they are not being advertised.
B. R4 has been incorrectly configured to be in another AS, so it does not peer with R5.
C. Automatic summarization is enabled, so only the 10.0.0.0 network is displayed.
D. The loopback addresses haven't been advertised, and the network command is missing on R4.
Answer: B
Explanation:
For an EIGRP neighbor to form, the following must match:
- Neighbors must be in the same subnet- K values- AS numbers- Authentication method and key strings.
Here, we see that R4 is configured for EIGRP AS 2, when it should be AS 1.

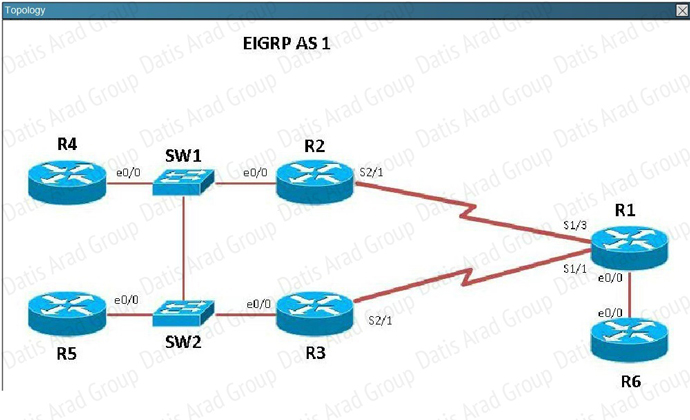
QUESTION NO: 314 Scenario
Refer to the topology. Your company has connected the routers R1. R2. and R3 with serial links. R2 and R3 are connected to the switches SW1 and SW2, respectively. SW1 and SW2 are also connected to the routers R4 and R5.
The EIGRP routing protocol is configured. You are required to troubleshoot and resolve the EIGRP issues between the various routers. Use the appropriate show commands to troubleshoot the issues.
Which path does traffic take from R1 to R5?
A. The traffic goes through R2.
B. The traffic goes through R3.
C. The traffic is equally load-balanced over R2 and R3.
D. The traffic is unequally load-balanced over R2 and R3.
Answer: A
Explanation:
Using the “show ip int brief command” on R5 we can see the IP addresses assigned to this router. Then, using the “show ip route” command on R1 we can see that to reach 10.5.5.5 and 10.5.5.55 the preferred path is via Serial 1/3, which we see from the diagram is the link to R2.
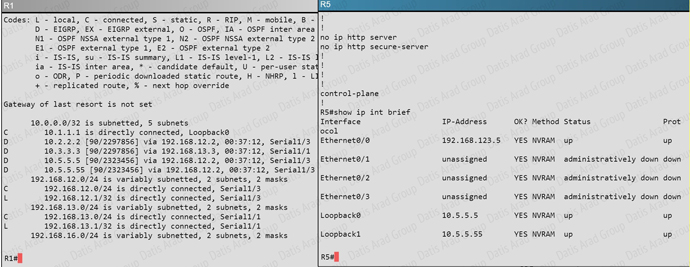
QUESTION NO: 315 Scenario
Refer to the topology. Your company has connected the routers R1. R2. and R3 with serial links. R2 and R3 are connected to the switches SW1 and SW2, respectively. SW1 and SW2 are also connected to the routers R4 and R5. The EIGRP routing protocol is configured.
You are required to troubleshoot and resolve the EIGRP issues between the various routers. Use the appropriate show commands to troubleshoot the issues.
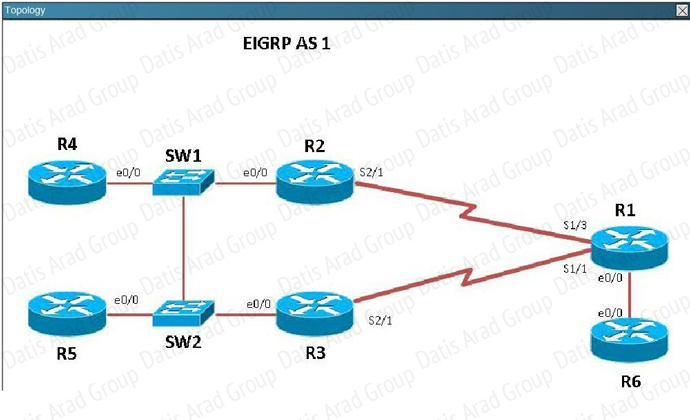
Router R6 does not form an EIGRP neighbor relationship correctly with router R1. What is the cause for this misconfiguration?
A. The K values mismatch.
B. The AS does not match.
C. The network command is missing.
D. The passive-interface command is enabled.
Answer: C
Explanation:
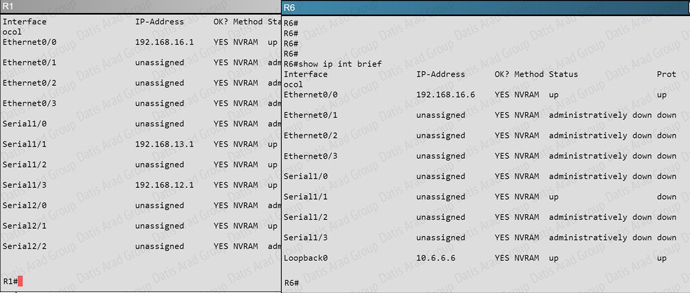
The link from R1 to R6 is shown below:
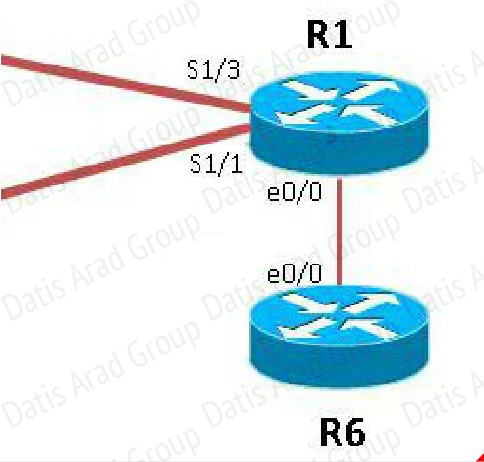
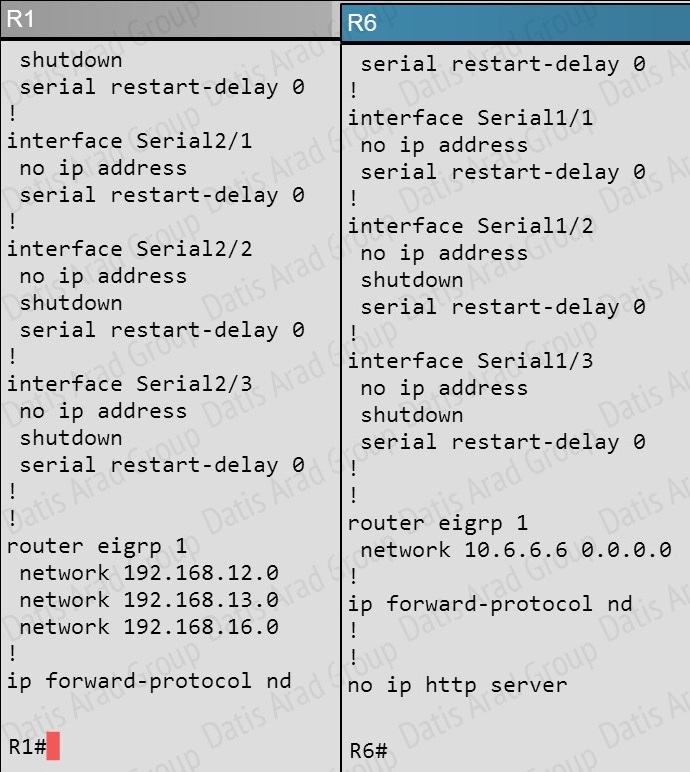
As you can see, they are both using e0/0. The IP addresses are in the 192.168.16.0 network:
But when we look at the EIGRP configuration, the “network 192.168.16.0” command is missing on R6.
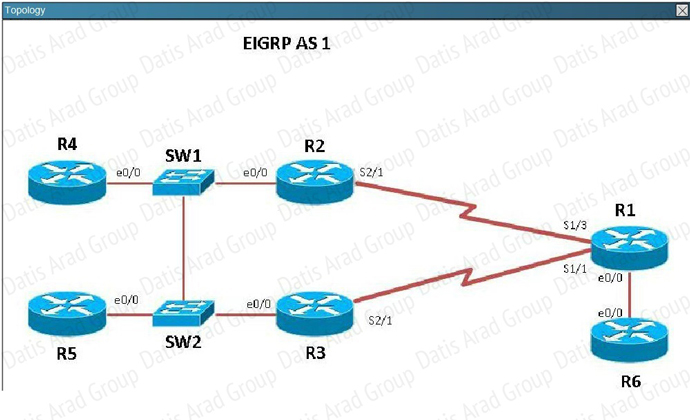
QUESTION NO: 316 Scenario
Refer to the topology. Your company has connected the routers R1. R2. and R3 with serial links. R2 and R3 are connected to the switches SW1 and SW2, respectively. SW1 and SW2 are also connected to the routers R4 and R5. The EIGRP routing protocol is configured.
You are required to troubleshoot and resolve the EIGRP issues between the various routers. Use the appropriate show commands to troubleshoot the issues.
A. The network statement is missing on R5.
B. The loopback interface is shut down on R5.
C. The network statement is missing on R1.
D. The IP address that is configured on the Lo1 interface on R5 is incorrect.
Answer: C
Explanation:
R5 does not have a route to the 10.1.1.1 network, which is the loopback0 IP address of R1. When looking at the EIGRP configuration on R1, we see that the 10.1.1.1 network statement is missing on R1.
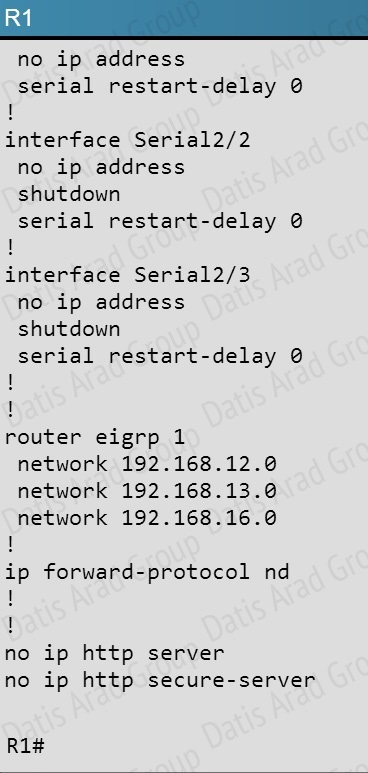
QUESTION NO: 317
Refer to the exhibit.
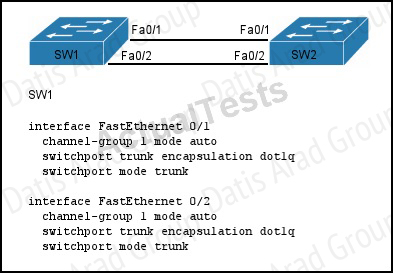
A network administrator is configuring an EtherChannel between SW1 and SW2. The SW1 configuration is shown. What is the correct configuration for SW2?
A. interface FastEthernet 0/1
channel-group 1 mode active
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 1 mode active
switchport trunk encapsulation dot1q
switchport mode trunk
B. interface FastEthernet 0/1
channel-group 2 mode auto
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 2 mode auto
switchport trunk encapsulation dot1q
switchport mode trunk
C. interface FastEthernet 0/1
channel-group 1 mode desirable
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 1 mode desirable
switchport trunk encapsulation dot1q
switchport mode trunk
D. interface FastEthernet 0/1
channel-group 1 mode passive
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 1 mode passive
switchport trunk encapsulation dot1q
switchport mode trunk
Answer: C
Explanation:
If the etherchannel was configured with mode “auto”, it was using PagP, so, we need to configure the other switch with “desirable” mode.
PagP modes: auto | Desirable
LACP modes: active | pasive
QUESTION NO: 318
Which feature builds a FIB and an adjacency table to expedite packet forwarding?
A. Cisco Express Forwarding
B. process switching
C. fast switching
D. cut-through
Answer: A
QUESTION NO: 319
What is the purpose of the POST operation on a router?
A. determine whether additional hardware has been added
B. locate an IOS image for booting
C. enable a TFTP server
D. set the configuration register
Answer: A
QUESTION NO: 320
Which command can you enter to set the default route for all traffic to an interface?
A. router(config)#ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/1
B. router(config)#ip route 0.0.0.0 255.255.255.255 GigabitEthernet0/1
C. router(config-router)#default-information originate
D. router(config-router)#default-information originate always
Answer: A