
نمونه سوالات آزمون CCNA Routing & Switching 200-120
Topic 2, LAN Switching Technologies
QUESTION NO: 61
Which command can be used from a PC to verify the connectivity between hosts that connect through a switch in the same LAN?
A. ping address
B. tracert address
C. traceroute address
D. arp address
Answer: A
Explanation:
ICMP pings are used to verify connectivity between two IP hosts. Traceroute is used to verify the router hop path traffic will take but in this case since the hosts are in the same LAN there will be no router hops involved.
QUESTION NO: 62
Based on the network shown in the graphic
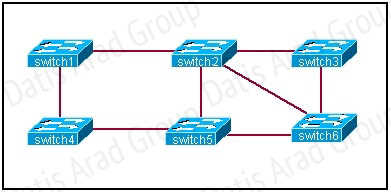
Which option contains both the potential networking problem and the protocol or setting that should be used to prevent the problem?
A. routing loops, hold down timers
B. switching loops, split horizon
C. routing loops, split horizon
D. switching loops, VTP
E. routing loops, STP
F. switching loops, STP
Answer: F
Explanation:
The Spanning-Tree Protocol (STP) prevents loops from being formed when switches or bridges are interconnected via multiple paths. Spanning-Tree Protocol implements the 802.1D IEEE algorithm by exchanging BPDU messages with other switches to detect loops, and then removes the loop by shutting down selected bridge interfaces. This algorithm guarantees that there is one and only one active path between two network devices.
QUESTION NO: 63
Refer to the exhibit.
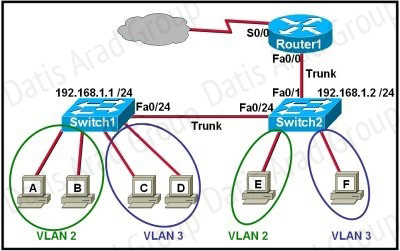
Which two statements are true about interVLAN routing in the topology that is shown in the
exhibit? (Choose two.)
A. Host E and host F use the same IP gateway address.
B. Router1 and Switch2 should be connected via a crossover cable.
C. Router1 will not play a role in communications between host A and host D.
D. The FastEthernet 0/0 interface on Router1 must be configured with subinterfaces.
E. Router1 needs more LAN interfaces to accommodate the VLANs that are shown in the exhibit.
F. The FastEthernet 0/0 interface on Router1 and the FastEthernet 0/1 interface on Switch2 trunk ports must be configured using the same encapsulation type.
Answer: D,F
Explanation:
In order for multiple VLANs to connect to a single physical interface on a Cisco router, subinterfaces must be used, one for each VLAN. This is known as the router on a stick configuration. Also, for any trunk to be formed, both ends of the trunk must agree on the encapsulation type, so each one must be configured for 802.1q or ISL.
QUESTION NO: 64
Which two of these are characteristics of the 802.1Q protocol? (Choose two.)
A. It is used exclusively for tagging VLAN frames and does not address network reconvergence following switched network topology changes.
B. It modifies the 802.3 frame header, and thus requires that the FCS be recomputed.
C. It is a Layer 2 messaging protocol which maintains VLAN configurations across networks.
D. It includes an 8-bit field which specifies the priority of a frame.
E. It is a trunking protocol capable of carrying untagged frames.
Answer: B,E
Explanation:
802.1Q protocol, or Virtual Bridged Local Area Networks protocol, mainly stipulates the realization of the VLAN. 802.1Q is a standardized relay method that inserts 4 bytes field into the original Ethernet frame and re-calculate the FCS. 802.1Q frame relay supports two types of frame: marked and non-marked. Non-marked frame carries no VLAN identification information.
QUESTION NO: 65
Refer to the exhibit.
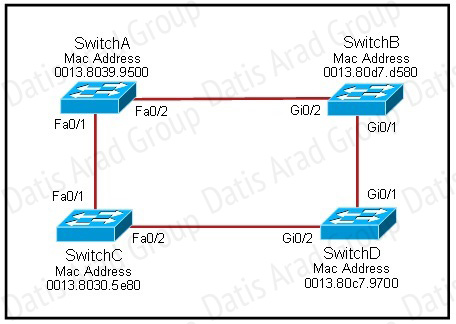
Each of these four switches has been configured with a hostname, as well as being configured to run RSTP. No other configuration changes have been made. Which three of these show the correct RSTP port roles for the indicated switches and interfaces? (Choose three.)
A. SwitchA, Fa0/2, designated
B. SwitchA, Fa0/1, root
C. SwitchB, Gi0/2, root
D. SwitchB, Gi0/1, designated
E. SwitchC, Fa0/2, root
F. SwitchD, Gi0/2, root
Answer: A,B,F
Explanation:
The question says “no other configuration changes have been made” so we can understand these switches have the same bridge priority. Switch C has lowest MAC address so it will become root bridge and 2 of its ports (Fa0/1 & Fa0/2) will be designated ports. Because SwitchC is the root bridge so the 2 ports nearest SwitchC on SwitchA (Fa0/1) and SwitchD (Gi0/2) will be root ports.
Now we come to the most difficult part of this question: SwitchB must have a root port so which port will it choose? To answer this question we need to know about STP cost and port cost. In general, “cost” is calculated based on bandwidth of the link. The higher the bandwidth on a link, the lower the value of its cost. Below are the cost values you should memorize:
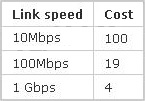
SwitchB will choose the interface with lower cost to the root bridge as the root port so we must calculate the cost on interface Gi0/1 & Gi0/2 of SwitchB to the root bridge. This can be calculated from the “cost to the root bridge” of each switch because a switch always advertises its cost to the root bridge in its BPDU. The receiving switch will add its local port cost value to the cost in the BPDU.
One more thing to notice is that a root bridge always advertises the cost to the root bridge (itself) with an initial value of 0.
Now let’s have a look at the topology again
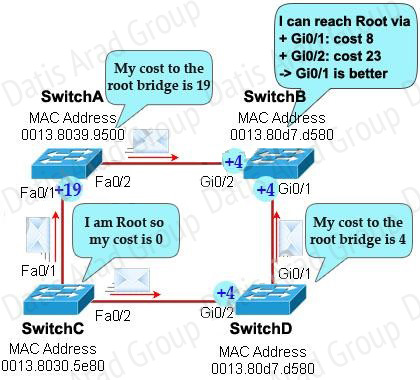
SwitchC advertises its cost to the root bridge with a value of 0. Switch D adds 4 (the cost value of 1Gbps link) and advertises this value (4) to SwitchB. SwitchB adds another 4 and learns that it can reach SwitchC via Gi0/1 port with a total cost of 8. The same process happens for SwitchA and SwitchB learns that it can reach SwitchC via Gi0/2 with a total cost of 23 -> Switch B chooses Gi0/1 as its root port.
Now our last task is to identify the port roles of the ports between SwitchA & SwitchB. It is rather easy as the MAC address of SwitchA is lower than that of SwitchB so Fa0/2 of SwitchA will be designated port while Gi0/2 of SwitchB will be alternative port.
Below summaries all the port roles of these switches:
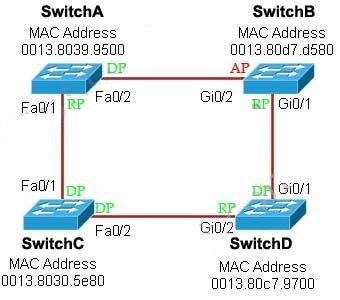
+ DP: Designated Port (forwarding state)
+ RP: Root Port (forwarding state)
+ AP: Alternative Port (blocking state)
QUESTION NO: 66
Refer to the exhibit.
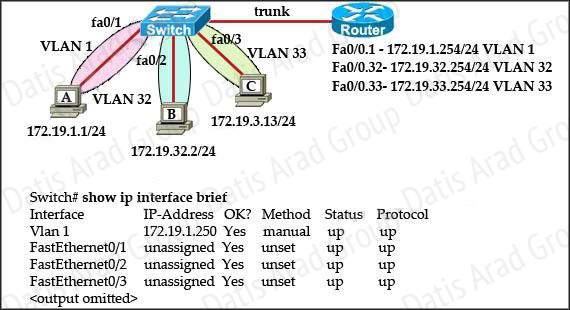
The network administrator normally establishes a Telnet session with the switch from host A. However, host A is unavailable. The administrator's attempt to telnet to the switch from host B fails, but pings to the other two hosts are successful. What is the issue?
A. Host B and the switch need to be in the same subnet.
B. The switch interface connected to the router is down.
C. Host B needs to be assigned an IP address in VLAN 1.
D. The switch needs an appropriate default gateway assigned.
E. The switch interfaces need the appropriate IP addresses assigned.
Answer: D
Explanation:
Ping was successful form host B to other hosts because of intervlan routing configured on router. But to manage switch via telnet the VLAN32 on the switch needs to be configured interface vlan32 along with ip address and its appropriate default-gateway address. Since VLAN1 interface is already configure on switch Host A was able to telnet switch.
QUESTION NO: 67
Refer to the exhibit.
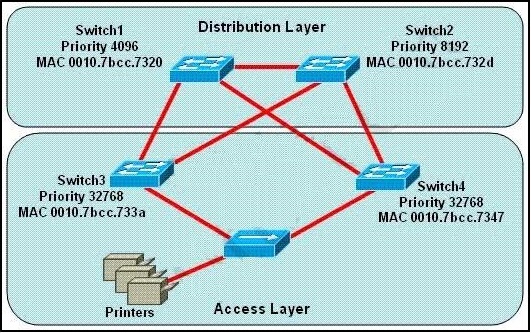
Which switch provides the spanning-tree designated port role for the network segment that services the printers?
A. Switch1
B. Switch2
C. Switch3
D. Switch4
Answer: C
Explanation:
Printers are connected by hubs. Decide the switch that provides the spanning-tree designated port role between Switch3 and Switch4. They have the same priority 32768. Compare their MAC addresses. Switch3 with a smaller MAC address will provide a designated port for printers.
QUESTION NO: 68
What is one benefit of PVST+?
A. PVST+ supports Layer 3 load balancing without loops.
B. PVST+ reduces the CPU cycles for all the switches in the network.
C. PVST+ allows the root switch location to be optimized per VLAN.
D. PVST+ automatically selects the root bridge location, to provide optimized bandwidth usage.
Answer: C
Explanation:
The PVST+ provides Layer 2 load-balancing for the VLAN on which it runs. You can create different logical topologies by using the VLANs on your network to ensure that all of your links are used but that no one link is oversubscribed. Each instance of PVST+ on a VLAN has a single root switch. This root switch propagates the spanning-tree information associated with that VLAN to all other switches in the network. Because each switch has the same information about the network, this process ensures that the network topology is maintained and optimized per VLAN.
QUESTION NO: 69
Which are valid modes for a switch port used as a VLAN trunk? (Choose three.)
A. transparent
B. auto
C. on
D. desirable
E. blocking
F. forwarding
Answer: B,C,D
QUESTION NO: 70
Refer to Exhibit:
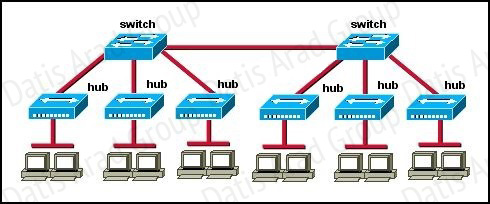
How many broadcast domains are shown in the graphic assuming only the default VLAN is
configured on the switches?
A. one
B. two
C. six
D. twelve
Answer: A
Explanation:
Only router can break up broadcast domains but in this exhibit no router is used so there is only 1 broadcast domain.
For your information, there are 7 collision domains in this exhibit (6 collision domains between hubs & switches + 1 collision between the two switches).
QUESTION NO: 71
Which three of these statements regarding 802.1Q trunking are correct? (Choose three.)
A. 802.1Q native VLAN frames are untagged by default.
B. 802.1Q trunking ports can also be secure ports.
C. 802.1Q trunks can use 10 Mb/s Ethernet interfaces.
D. 802.1Q trunks require full-duplex, point-to-point connectivity.
E. 802.1Q trunks should have native VLANs that are the same at both ends.
Answer: A,C,E
Explanation:
By default, 802.1Q trunk defined Native VLAN in order to forward unmarked frame. Switches can forward Layer 2 frame from Native VLAN on unmarked trunks port. Receiver switches will transmit all unmarked packets to Native VLAN. Native VLAN is the default VLAN configuration of port. Note for the 802.1Q trunk ports between two devices, the same Native VLAN configuration is required on both sides of the link. If the Native VLAN in 802.1Q trunk ports on same trunk link is properly configured, it could lead to layer 2 loops. The 802.1Q trunk link transmits VLAN information through Ethernet.
QUESTION NO: 72
Refer to the exhibit.
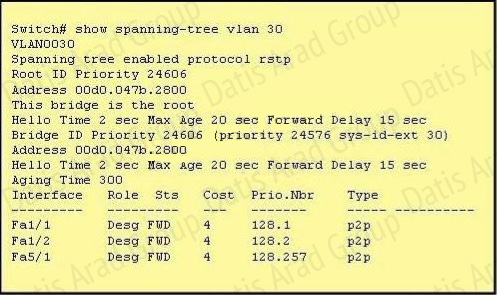
The output that is shown is generated at a switch. Which three statements are true? (Choose three.)
A. All ports will be in a state of discarding, learning, or forwarding.
B. Thirty VLANs have been configured on this switch.
C. The bridge priority is lower than the default value for spanning tree.
D. All interfaces that are shown are on shared media.
E. All designated ports are in a forwarding state.
F. This switch must be the root bridge for all VLANs on this switch.
Answer: A,C,E
Explanation:
From the output, we see that all ports are in designated role (forwarding state). The command “show spanning-tree vlan 30 only shows us information about VLAN 30. We don’t know how many VLAN exists in this switch.
The bridge priority of this switch is 24606 which is lower than the default value bridge priority 32768.
All three interfaces on this switch have the connection type “p2p”, which means Point-to-point environment – not a shared media. The only thing we can specify is this switch is the root bridge for VLAN 3o but we can not guarantee it is also the root bridge for other VLANs.
QUESTION NO: 73
Refer to the exhibit.
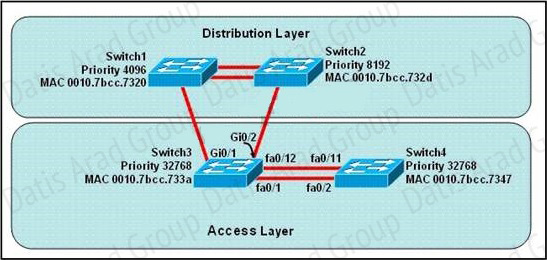
At the end of an RSTP election process, which access layer switch port will assume the discarding role?
A. Switch3, port fa0/1
B. Switch3, port fa0/12
C. Switch4, port fa0/11
D. Switch4, port fa0/2
E. Switch3, port Gi0/1
F. Switch3, port Gi0/2
Answer: C
Explanation:
In this question, we only care about the Access Layer switches (Switch3 & 4). Switch 3 has a lower bridge ID than Switch 4 (because the MAC of Switch3 is smaller than that of Switch4) so both ports of Switch3 will be in forwarding state. The alternative port will surely belong to Switch4. Switch4 will need to block one of its ports to avoid a bridging loop between the two switches. But how does Switch4 select its blocked port? Well, the answer is based on the BPDUs it receives from Switch3. A BPDU is superior to another if it has:
1. A lower Root Bridge ID
2. A lower path cost to the Root
3. A lower Sending Bridge ID
4. A lower Sending Port ID
These four parameters are examined in order. In this specific case, all the BPDUs sent by Switch3 have the same Root Bridge ID, the same path cost to the Root and the same Sending Bridge ID. The only parameter left to select the best one is the Sending Port ID (Port ID = port priority + port index). In this case the port priorities are equal because they use the default value, so Switch4 will compare port index values, which are unique to each port on the switch, and because Fa0/12 is inferior to Fa0/1, Switch4 will select the port connected with Fa0/1 (of Switch3) as its root port and block the other port -> Port fa0/11 of Switch4 will be blocked (discarding role).
QUESTION NO: 74
Which term describes a spanning-tree network that has all switch ports in either the blocking or fowarding state?
A. converged
B. redundant
C. provisioned
D. spanned
Answer: A
Explanation:
Spanning Tree Protocol convergence (Layer 2 convergence) happens when bridges and switches have transitioned to either the forwarding or blocking state. When layer 2 is converged, root bridge is elected and all port roles (Root, Designated and Non-Designated) in all switches are selected.
QUESTION NO: 75
What are the possible trunking modes for a switch port? (Choose three.)
A. transparent
B. auto
C. on
D. desirable
E. client
F. forwarding
Answer: B,C,D
QUESTION NO: 76
Which two of these statements regarding RSTP are correct? (Choose two.)
A. RSTP cannot operate with PVST+.
B. RSTP defines new port roles.
C. RSTP defines no new port states.
D. RSTP is a proprietary implementation of IEEE 802.1D STP.
E. RSTP is compatible with the original IEEE 802.1D STP.
Answer: B,E
Explanation:
When network topology changes, rapid spanning tree protocol (IEEE802.1W, referred to as RSTP) will speed up significantly the speed to re-calculate spanning tree. RSTP not only defines the role of other ports: alternative port and backup port, but also defines status of 3 ports: discarding status, learning status, forwarding status. RSTP is 802.1D standard evolution, not revolution. It retains most of the parameters, and makes no changes.
QUESTION NO: 77
Refer to the exhibit.
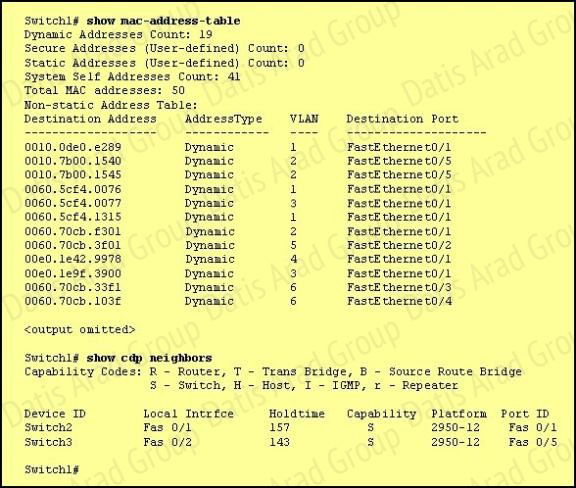
Which two statements are true of the interfaces on Switch1? (Choose two.)
A. Multiple devices are connected directly to FastEthernet0/1.
B. A hub is connected directly to FastEthernet0/5.
C. FastEthernet0/1 is connected to a host with multiple network interface cards.
D. FastEthernet0/5 has statically assigned MAC addresses.
E. FastEthernet0/1 is configured as a trunk link.
F. Interface FastEthernet0/2 has been disabled.
Answer: B,E
Explanation:
Carefully observe the information given after command show. Fa0/1 is connected to Switch2, seven MAC addresses correspond to Fa0/1, and these MAC are in different VLAN. From this we know that Fa0/1 is the trunk interface. From the information given by show cdp neighbors we find that there is no Fa0/5 in CDP neighbor. However, F0/5 corresponds to two MAC addresses in the same VLAN. Thus we know that Fa0/5 is connected to a Hub.
Based on the output shown, there are multiple MAC addresses from different VLANs attached to the FastEthernet 0/1 interface. Only trunks are able to pass information from devices in multiple VLANs.
QUESTION NO: 78
Three switches are connected to one another via trunk ports. Assuming the default switch configuration, which switch is elected as the root bridge for the spanning-tree instance of VLAN 1?
A. the switch with the highest MAC address
B. the switch with the lowest MAC address
C. the switch with the highest IP address
D. the switch with the lowest IP address
Answer: B
Explanation:
Each switch in your network will have a Bridge ID Priority value, more commonly referred to as a BID. This BID is a combination of a default priority value and the switch's MAC address, with the priority value listed first. The lowest BID will win the election process. For example, if a Cisco switch has the default priority value of 32,768 and a MAC address of 11-22-33-44-55-66, the BID would be 32768:11-22-33-44-55-66. Therefore, if the switch priority is left at the default, the MAC address is the deciding factor in the root bridge election.
QUESTION NO: 79
What are three advantages of VLANs? (Choose three.)
A. VLANs establish broadcast domains in switched networks.
B. VLANs utilize packet filtering to enhance network security.
C. VLANs provide a method of conserving IP addresses in large networks.
D. VLANs provide a low-latency internetworking alternative to routed networks.
E. VLANs allow access to network services based on department, not physical location.
F. VLANs can greatly simplify adding, moving, or changing hosts on the network.
Answer: A,E,F
Explanation:
VLAN technology is often used in practice, because it can better control layer2 broadcast to improve network security. This makes network more flexible and scalable. Packet filtering is a function of firewall instead of VLAN.
QUESTION NO: 80
Cisco Catalyst switches CAT1 and CAT2 have a connection between them using ports FA0/13. An 802.1Q trunk is configured between the two switches. On CAT1, VLAN 10 is chosen as native, but on CAT2 the native VLAN is not specified.
What will happen in this scenario?
A. 802.1Q giants frames could saturate the link.
B. VLAN 10 on CAT1 and VLAN 1 on CAT2 will send untagged frames.
C. A native VLAN mismatch error message will appear.
D. VLAN 10 on CAT1 and VLAN 1 on CAT2 will send tagged frames.
Answer: C
Explanation:
A “native VLAN mismatch” error will appear by CDP if there is a native VLAN mismatch on an 802.1Q link. “VLAN mismatch” can cause traffic from one vlan to leak into another vlan.