نمونه سوالات آزمون CCIE Routing and Switching 400-101
QUESTION NO: 241
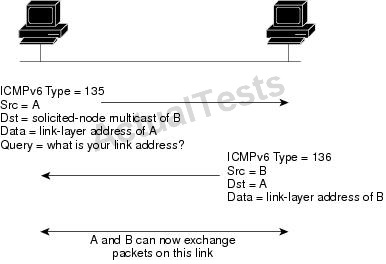
Which neighbor-discovery message type is used to verify connectivity to a neighbor when the linklayer address of the neighbor is known?
A. neighbor solicitation
B. neighbor advertisement
C. router advertisement
D. router solicitation
Answer: A
Explanation:
IPv6 Neighbor Solicitation Message
A value of 135 in the Type field of the ICMP packet header identifies a neighbor solicitation message. Neighbor solicitation messages are sent on the local link when a node wants to determine the link-layer address of another node on the same local link (see the figure below). When a node wants to determine the link-layer address of another node, the source address in a neighbor solicitation message is the IPv6 address of the node sending the neighbor solicitation message. The destination address in the neighbor solicitation message is the solicited-node multicast address that corresponds to the IPv6 address of the destination node. The neighbor solicitation message also includes the link-layer address of the source node.
IPv6 Neighbor Discovery: Neighbor Solicitation Message
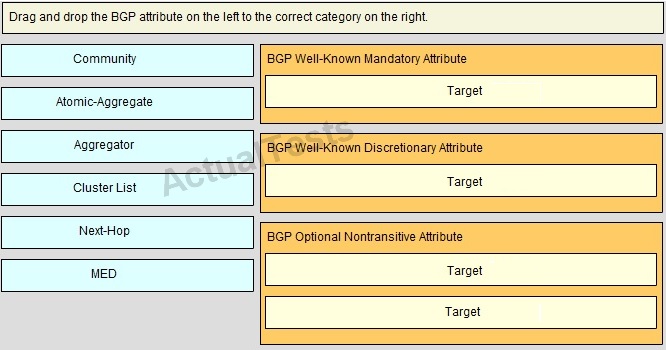
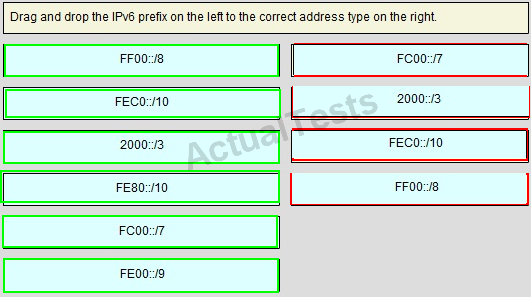
QUESTION NO: 242
Drag and Drop
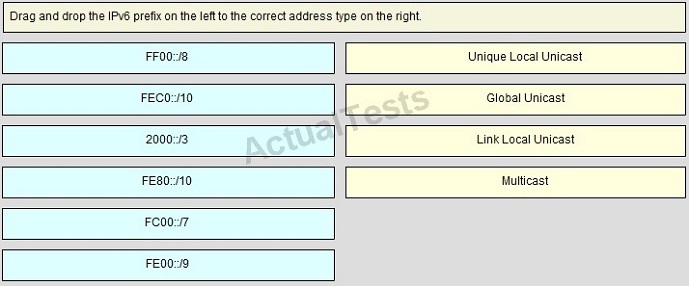
Answer:
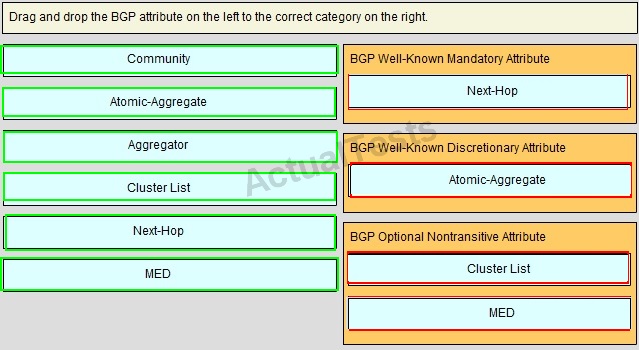
QUESTION NO: 243
Drag and Drop
Answer:
QUESTION NO: 244
Drag and Drop
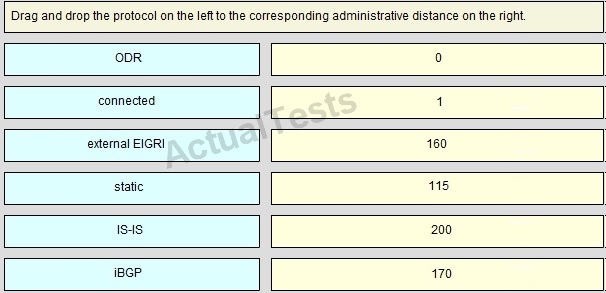
Answer:
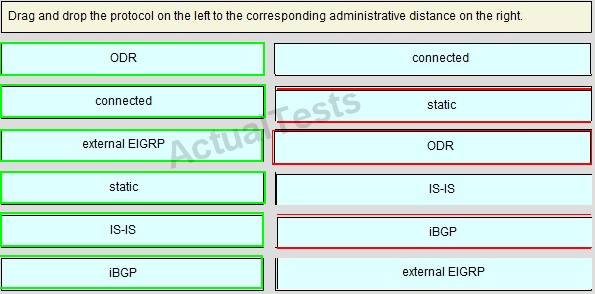
QUESTION NO: 245
Drag and Drop
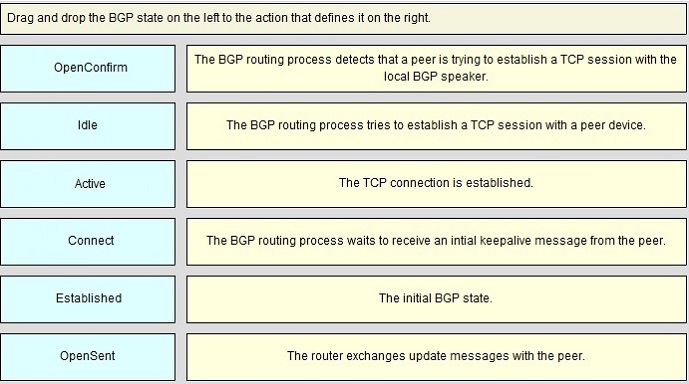
Answer:
QUESTION NO: 246
Drag and Drop
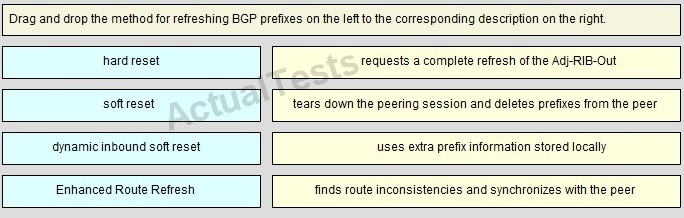
Answer:
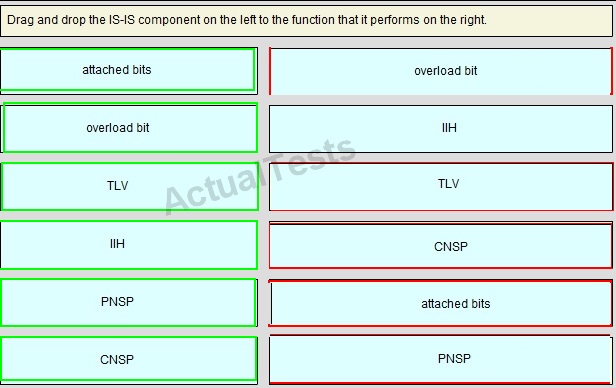
QUESTION NO: 247
Drag and Drop
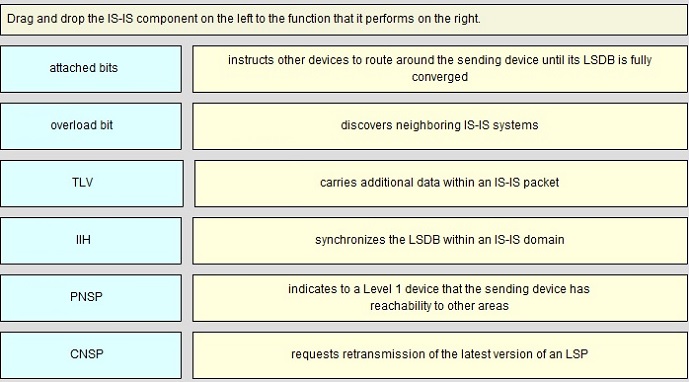
Answer:
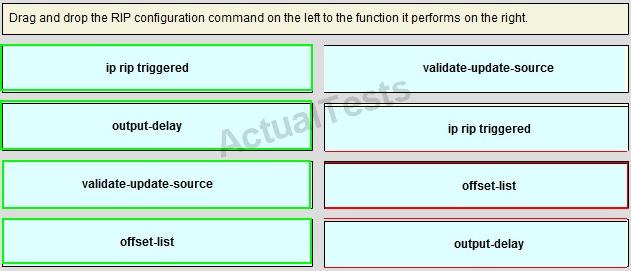
QUESTION NO: 248
Drag and Drop
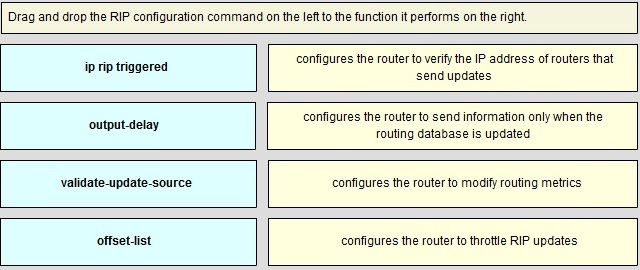
Answer:
QUESTION NO: 249
Refer to the exhibit.
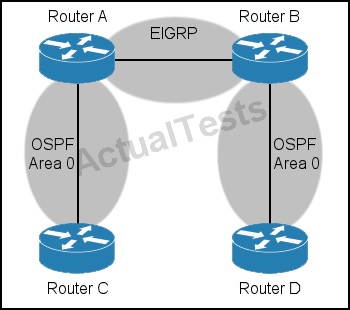
Which action must you take to enable full reachability from router C to router D?
A. Build an OSPF virtual link.
B. Build an OSPF sham link.
C. Configure mutual redistribution between OSPF and EIGRP on routers A and B.
D. Add a static route on router D.
Answer: C
Explanation:
For full connectivity, we need to configure mutual redistribution to advertise the EIGRP routes into OSPF and to advertise the OSPF routes into the EIGRP network. This needs to be done at the two border routers that connect to both the EIGRP and OSPF domains.
QUESTION NO: 250
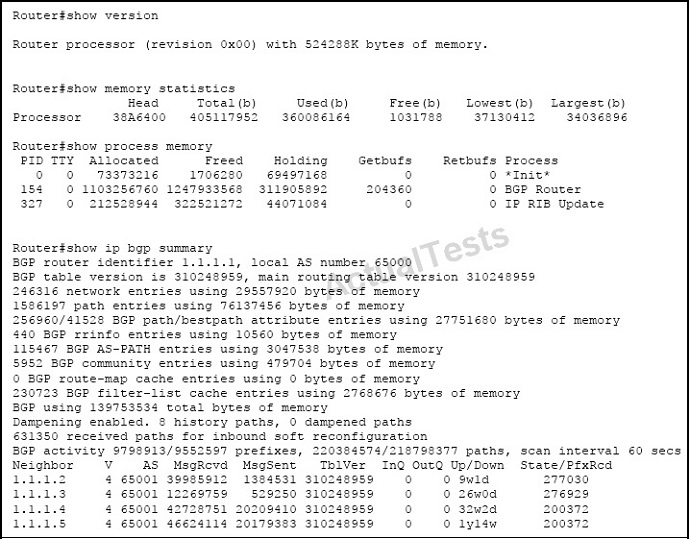
Refer to the exhibit.
Why is the router out of memory?
A. The router is experiencing a BGP memory leak software defect.
B. The BGP peers have been up for too long.
C. The amount of BGP update traffic in the network is too high.
D. The router has insufficient memory due to the size of the BGP database.
Answer: D
Explanation:
Here we can see that this router is running out of memory due to the large size of the BGP routing database. In this case, this router is receiving over 200,000 routes from each of the 4 peers.
QUESTION NO: 11
What is the cause of ignores and overruns on an interface, when the overall traffic rate of the interface is low?
A. a hardware failure of the interface
B. a software bug
C. a bad cable
D. microbursts of traffic
Answer: D
Explanation:
Micro-bursting is a phenomenon where rapid bursts of data packets are sent in quick succession, leading to periods of full line-rate transmission that can overflow packet buffers of the network stack, both in network endpoints and routers and switches inside the network.
Symptoms of micro bursts will manifest in the form of ignores and/ or overruns (also shown as accumulated in “input error” counter within show interface output). This is indicative of receive ring and corresponding packet buffer being overwhelmed due to data bursts coming in over extremely short period of time (microseconds). You will never see a sustained data traffic within show interface’s “input rate” counter as they are averaging bits per second (bps) over 5 minutes by default (way too long to account for microbursts). You can understand microbursts from a scenario where a 3-lane highway merging into a single lane at rush hour – the capacity burst cannot exceed the total available bandwidth (i.e. single lane), but it can saturate it for a period of time.
QUESTION NO: 12
Refer to the exhibit.
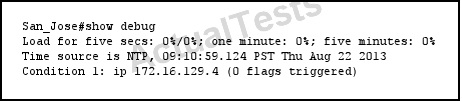 Which statement about the debug behavior of the device is true?
Which statement about the debug behavior of the device is true?
A. The device debugs all IP events for 172.16.129.4.
B. The device sends all debugging information for 172.16.129.4.
C. The device sends only NTP debugging information to 172.16.129.4.
D. The device sends debugging information every five seconds.
Answer: A
Explanation:
This is an example of a conditional debug, where there is a single condition specified of IP address 172.16.129.4. so all IP events for that address will be output in the debug.
QUESTION NO: 13
Which statement about MSS is true?
A. It is negotiated between sender and receiver.
B. It is sent in all TCP packets.
C. It is 20 bytes lower than MTU by default.
D. It is sent in SYN packets.
E. It is 28 bytes lower than MTU by default.
Answer: D
Explanation:
The maximum segment size (MSS) is a parameter of the Options field of the TCP header that specifies the largest amount of data, specified in octets, that a computer or communications device can receive in a single TCP segment. It does not count the TCP header or the IP header. The IP datagram containing a TCP segment may be self-contained within a single packet, or it may be reconstructed from several fragmented pieces; either way, the MSS limit applies to the total amount of data contained in the final, reconstructed TCP segment. The default TCP Maximum Segment Size is 536. Where a host wishes to set the maximum segment size to a value other than the default, the maximum segment size is specified as a TCP option, initially in the TCP SYN packet during the TCP handshake. The value cannot be changed after the connection is established.
QUESTION NO: 14
Which two methods change the IP MTU value for an interface? (Choose two.)
A. Configure the default MTU.
B. Configure the IP system MTU.
C. Configure the interface MTU.
D. Configure the interface IP MTU.
Answer: C,D
Explanation:
An IOS device configured for IP+MPLS routing uses three different Maximum Transmission Unit (MTU) values: The hardware MTU configured with the mtu interface configuration command The hardware MTU specifies the maximum packet length the interface can support … or at least that's the theory behind it. In reality, longer packets can be sent (assuming the hardware interface chipset doesn't complain); therefore you can configure MPLS MTU to be larger than the interface MTU and still have a working network. Oversized packets might not be received correctly if the interface uses fixed-length buffers; platforms with scatter/gather architecture (also called particle buffers) usually survive incoming oversized packets.
IP MTU is used to determine whether am IP packet forwarded through an interface has to be fragmented. It has to be lower or equal to hardware MTU (and this limitation is enforced). If it equals the HW MTU, its value does not appear in the running configuration and it tracks the changes in HW MTU. For example, if you configure ip mtu 1300 on a Serial interface, it will appear in the running configuration as long as the hardware MTU is not equal to 1300 (and will not change as the HW MTU changes). However, as soon as the mtu 1300 is configured, the ip mtu 1300 command disappears from the configuration and the IP MTU yet again tracks the HW MTU.
QUESTION NO: 15
Which implementation can cause packet loss when the network includes asymmetric routing paths?
A. the use of ECMP routing
B. the use of penultimate hop popping
C. the use of Unicast RPF
D. disabling Cisco Express Forwarding
Answer: C
Explanation:
When administrators use Unicast RPF in strict mode, the packet must be received on the interface that the router would use to forward the return packet. Unicast RPF configured in strict mode may drop legitimate traffic that is received on an interface that was not the router's choice for sending return traffic. Dropping this legitimate traffic could occur when asymmetric routing paths are present in the network.
QUESTION NO: 16
Which two mechanisms can be used to eliminate Cisco Express Forwarding polarization? (Choose two.)
A. Make all of the changes at once to minimize the impact to users.A. alternating cost links
B. the unique-ID/universal-ID algorithm
C. Cisco Express Forwarding antipolarization
D. different hashing inputs at each layer of the network
Answer: B,D
Explanation:
This document describes how Cisco Express Forwarding (CEF) polarization can cause suboptimal use of redundant paths to a destination network. CEF polarization is the effect when a hash algorithm chooses a particular path and the redundant paths remain completely unused.
How to Avoid CEF Polarization
1: 12: 7-83: 1-1-14: 1-1-1-25: 1-1-1-1-16: 1-2-2-2-2-27: 1-1-1-1-1-1-18: 1-1-1-2-2-2-2-2
The number before the colon represents the number of equal-cost paths. The number after the colon represents the proportion of traffic which is forwarded per path.This means that: This illustrates that, when there is even number of ECMP links, the traffic is not load-balanced.
QUESTION NO: 17
Which two mechanisms provide Cisco IOS XE Software with control plane and data plane separation? (Choose two.)
A. Forwarding and Feature Manager
B. Forwarding Engine Driver
C. Forwarding Performance Management
D. Forwarding Information Base
Answer: A,B
Explanation:
Control Plane and Data Plane Separation
IOS XE introduces an opportunity to enable teams to now build drivers for new Data Plane ASICs outside the IOS instance and have them program to a set of standard APIs which in turn enforces Control Plane and Data Plane processing separation.
IOS XE accomplishes Control Plane / Data Plane separation through the introduction of the Forwarding and Feature Manager (FFM) and its standard interface to the Forwarding Engine Driver (FED). FFM provides a set of APIs to Control Plane processes. In turn, the FFM programs the Data Plane via the FED and maintains forwarding state for the system. The FED is the instantiation of the hardware driver for the Data Plane and is provided by the platform.
QUESTION NO: 18
Refer to the exhibit.
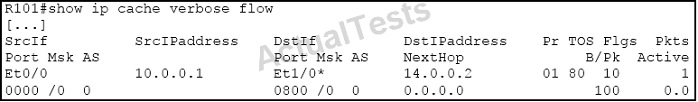 What is the PHB class on this flow?
What is the PHB class on this flow?
A. EF
B. none
C. AF21
D. CS4
Answer: D
Explanation:
The Standard CCM Admin Users role includes no permissions beyond logging into Cisco Unified Communications Manager Administration. The administrator must add another authorization role to define the parts of the Cisco Unified Communications Manager Administration that the user can administer.
The Standard CCMADMIN Administration role allows a user to access and make changes in all of Cisco Unified Communications Manager Administration.
QUESTION NO: 19
Refer to the exhibit.
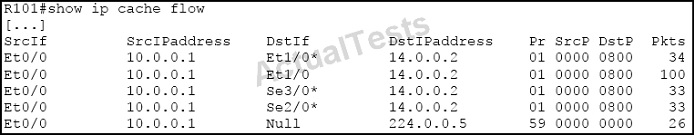
What kind of load balancing is done on this router?
A. per-packet load balancing
B. per-flow load balancing
C. per-label load balancing
D. star round-robin load balancing
Answer: A
Explanation:
Here we can see that for the same traffic source/destination pair of 10.0.0.1 to 14.0.0.2 there were a total of 100 packets (shown by second entry without the *) and that the packets were distributed evenly across the three different outgoing interfaces (34, 33, 33 packets, respectively.
QUESTION NO: 20
What is the most efficient way to confirm whether microbursts of traffic are occurring?
A. Monitor the output traffic rate using the show interface command.
B. Monitor the output traffic rate using the show controllers command.
C. Check the CPU utilization of the router.
D. Sniff the traffic and plot the packet rate over time.
Answer: D
Explanation:
Micro-bursting is a phenomenon where rapid bursts of data packets are sent in quick succession, leading to periods of full line-rate transmission that can overflow packet buffers of the network stack, both in network endpoints and routers and switches inside the network. In order to troubleshoot microbursts, you need a packet sniffer that can capture traffic over a long period of time and allow you to analyze it in the form of a graph which displays the saturation points (packet rate during microbursts versus total available bandwidth). You can eventually trace it to the source causing the bursts (e.g. stock trading applications).