نمونه سوالات آزمون CCIE Routing and Switching 400-101
QUESTION NO: 121
Which two fields reside in the initial CHAP challenge packet? (Choose two.)
A. the authentication name of the challenger
B. a random hash value generated by the device
C. the hashed packet type ID
D. the packet type ID in clear text
Answer: A,D
Explanation:
When a caller A dials in to an access server B, The Access server sends across the link an initial Type 1 authentication packet called a Challenge. This Challenge packet contains a randomly generated number, an ID sequence number to identify the challenge (sent in clear text) and the authentication name of the challenger.
QUESTION NO: 122
Which statement about WAN Ethernet Services is true?
A. Rate-limiting can be configured per EVC.
B. Point-to-point processing and encapsulation are performed on the customer network.
C. Ethernet multipoint services function as a multipoint-to-multipoint VLAN-based connection.
D. UNIs can perform service multiplexing and all-in-one bundling.
Answer: A
Explanation:
The MEF has defined a set of bandwidth profiles that can be applied at the UNI or to an EVC. A bandwidth profile is a limit on the rate at which Ethernet frames can traverse the UNI or the EVC.
QUESTION NO: 123
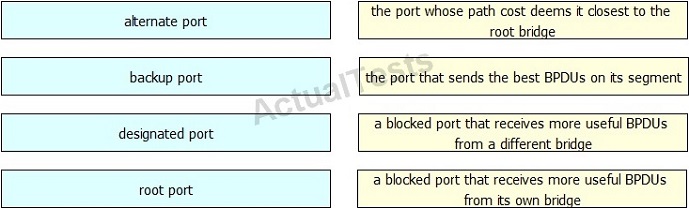
Drag and drop each STP port role on the left to the matching statement on the right.
Answer:
QUESTION NO: 124
Drag and drop the VLAN number on the left to the corresponding default VLAN name on the right.
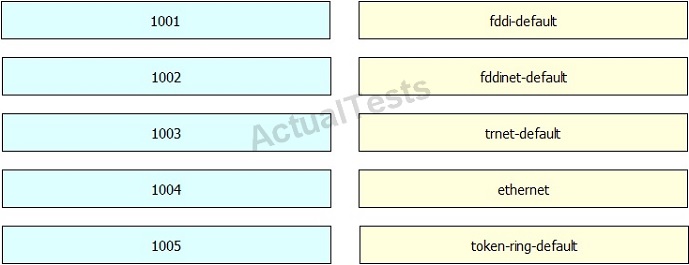
Answer:

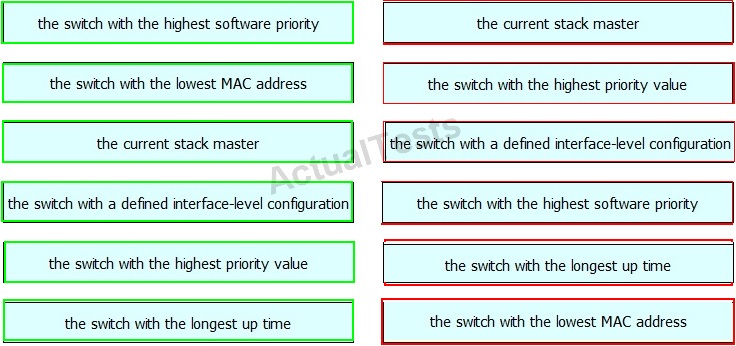
QUESTION NO: 125
Drag and drop the StackWise stack master election rule on the left into the correct priority order on the right.

Answer:
QUESTION NO: 126
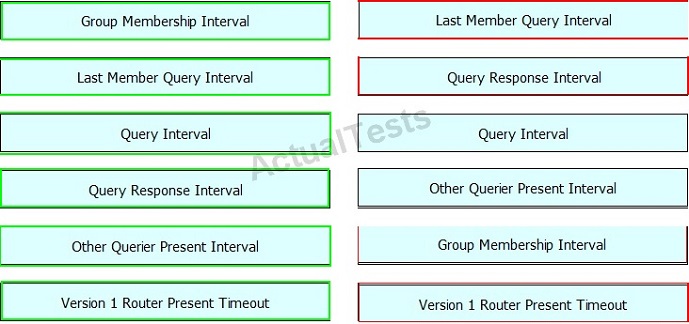
Drag and drop the IGMPv2 timer on the left to its default value on the right.
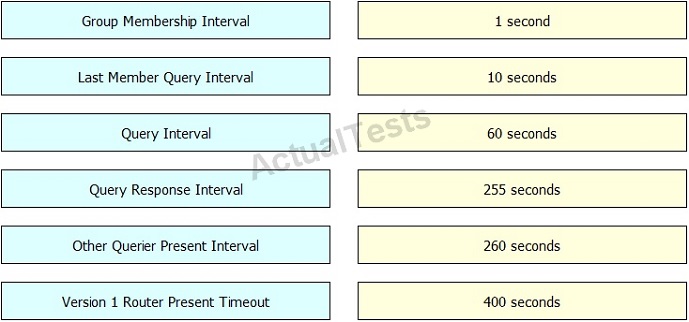
Answer:
QUESTION NO: 127
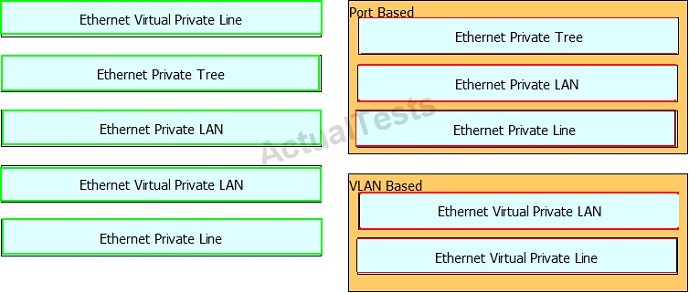
Drag and drop the Metro Ethernet circuit on the left to the corresponding Service Type category on the right.
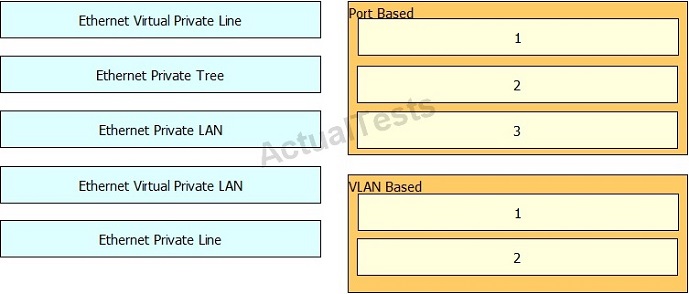
Answer:
QUESTION NO: 128
You are configuring Wireshark on a Cisco Catalyst 4500E Switch with a Supervisor 8. Which three actions can you take to prevent the capture from overloading the CPU? (Choose three.)
A. Attach the specific ports that are part of the data path.
B. Use an in-line filter.
C. Use an appropriate ACL.
D. Add memory to the Supervisor.
E. Reconfigure the buffers to accommodate the additional traffic.
F. Configure a policy map, class map, and an access list to express the match conditions.
Answer: A,B,C
Explanation:
Because packet forwarding typically occurs in hardware, packets are not copied to the CPU for software processing. For Wireshark packet capture, packets are copied and delivered to the CPU, which causes an increase in CPU usage.
QUESTION NO: 129
Which three statements about VTP version 3 are true? (Choose three.)
A. It supports other databases in addition to VLAN.
B. It supports VLANs up to 4095.
C. It supports the synchronization of switch configuration templates between switches in the domain.
D. It supports the transfer of information about private VLAN structures.
E. It supports the transfer of PVST+ configuration information.
F. It supports RSTP.
Answer: A,B,D
Explanation:
Much work has gone into improving the usability of VTP version 3 in three major areas:
• The new version of VTP offers better administrative control over which device is allowed to update other devices' view of the VLAN topology. The chance of unintended and disruptive changes is significantly reduced, and availability is increased. The reduced risk of unintended changes will ease the change process and help speed deployment.
• Functionality for the VLAN environment has been significantly expanded. Two enhancements are most beneficial for today's networks:
– In addition to supporting the earlier ISL VLAN range from 1 to 1001, the new version supports the whole IEEE 802.1Q VLAN range up to 4095.
– In addition to supporting the concept of normal VLANs, VTP version 3 can transfer information regarding Private VLAN (PVLAN) structures.
• The third area of major improvement is support for databases other than VLAN (for example, MST).
QUESTION NO: 130
In an STP domain, which two statements are true for a nonroot switch, when it receives a configuration BPDU from the root bridge with the TC bit set? (Choose two.)
A. It sets the MAC table aging time to max_age + forward_delay time.
B. It sets the MAC table aging time to forward_delay time.
C. It recalculates the STP topology upon receiving topology change notification from the root switch.
D. It receives the topology change BPDU on both forwarding and blocking ports.
Answer: B,D
Explanation:
When the TC bit is received, Every bridge is then notified and reduces the aging time to forward_delay (15 seconds by default) for a certain period of time (max_age + forward_delay). It is more beneficial to reduce the aging time instead of clearing the table because currently active hosts, that effectively transmit traffic, are not cleared from the table.
Once the root is aware that there has been a topology change event in the network, it starts to send out its configuration BPDUs with the topology change (TC) bit set. These BPDUs are relayed by every bridge in the network with this bit set. As a result all bridges become aware of the topology change situation and it can reduce its aging time to forward_delay. Bridges receive topology change BPDUs on both forwarding and blocking ports.
An important point to consider here is that a TCN does not start a STP recalculation. This fear comes from the fact that TCNs are often associated with unstable STP environments; TCNs are a consequence of this, not a cause. The TCN only has an impact on the aging time. It does not change the topology nor create a loop.
QUESTION NO: 131
Which two statements about RSTP and MSTP BPDUs are true? (Choose two.)
A. MSTP switches can detect boundary ports when they receive RSTP version 2 BPDUs.
B. MSTP switches can detect boundary ports when they receive RSTP version 1 BPDUs.
C. RSTP switches can process MSTP version 3 BPDUs.
D. When all boundary switches are running RSTP, MST sends only version 0 configuration BPDUs.
Answer: A,C
Explanation:
A switch running both MSTP and RSTP supports a built-in protocol migration mechanism that enables it to interoperate with legacy 802.1D switches. If this switch receives a legacy 802.1D configuration BPDU (a BPDU with the protocol version set to 0), it sends only 802.1D BPDUs on that port. An MST switch can also detect that a port is at the boundary of a region when it receives a legacy BPDU, an MST BPDU (version 3) associated with a different region, or an RST BPDU (version 2).
QUESTION NO: 132
Which three options are sources from which a SPAN session can copy traffic? (Choose three.)
A. ports
B. EtherChannels
C. VLANs
D. subnets
E. primary IP addresses
F. secondary IP addresses
Answer: A,B,C
QUESTION NO: 133
Which three capabilities are provided by MLD snooping? (Choose three.)
A. dynamic port learning
B. IPv6 multicast router discovery
C. user-configured ports age out automatically
D. a 5-minute aging timer
E. flooding control packets to the egress VLAN
F. a 60-second aging timer
Answer: A,B,D
Explanation:
Like IGMP snooping, MLD snooping performs multicast router discovery, with these characteristics:
• Ports configured by a user never age out.
• Dynamic port learning results from MLDv1 snooping queries and IPv6 PIMv2 packets.
•If there are multiple routers on the same Layer 2 interface, MLD snooping tracks a single multicast router on the port (the router that most recently sent a router control packet).
• Dynamic multicast router port aging is based on a default timer of 5 minutes; the multicast router is deleted from the router port list if no control packet is received on the port for 5 minutes.
• IPv6 multicast router discovery only takes place when MLD snooping is enabled on the switch.
QUESTION NO: 134
Refer to the exhibit.
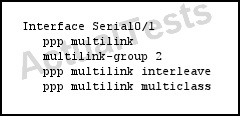
Which two statements about the implementation are true? (Choose two.)
A. The PPP multilink protocol header is omitted on delay-sensitive packets.
B. The maximum number of fragments is 1.
C. Small real-time packets are multilink-encapsulated.
D. A transmit queue is provided for smaller packets.
Answer: A,D
Explanation:
Previous implementations of Cisco IOS Multilink PPP (MLP) include support for Link Fragmentation Interleaving (LFI). This feature allows the delivery of delay-sensitive packets, such as the packets of a Voice call, to be expedited by omitting the PPP Multilink Protocol header and sending the packets as raw PPP packets in between the fragments of larger data packets. This feature works well on bundles consisting of a single link. However, when the bundle contains multiple links there is no way to keep the interleaved packets in sequence with respect to each other.
The Multiclass Multilink PPP (MCMP) feature in Cisco IOS Release 12.2(13)T addresses the limitations of MLP LFI on bundles containing multiple links by introducing multiple data classes. With multiclass multilink PPP interleaving, large packets can be multilink-encapsulated and fragmented into smaller packets to satisfy the delay requirements of real-time voice traffic; small real-time packets, which are not multilink encapsulated, are transmitted between fragments of the large packets. The interleaving feature also provides a special transmit queue for the smaller, delay-sensitive packets, enabling them to be transmitted earlier than other flows. Interleaving provides the delay bounds for delay-sensitive voice packets on a slow link that is used for other best-effort traffic.
QUESTION NO: 135
Which two statements are characteristics of Ethernet private LAN circuits? (Choose two.)
A. They support communication between two or more customer endpoints.
B. They utilize more than one bridge domain.
C. They support point-to-multipoint EVC.
D. They support multipoint-to-multipoint EVC.
Answer: A,D
Explanation:
An Ethernet Private LAN (EPLAN) is a multipoint–to–multipoint EVC. EPLAN is an EVC that supports communication between two or more UNIs. In EPLAN, only one EVC can exist on a port and the port can have only one EFP.
QUESTION NO: 136
Which two statements about Inverse ARP are true? (Choose two.)
A. It uses the same operation code as ARP.
B. It uses the same packet format as ARP.
C. It uses ARP stuffing.
D. It supports static mapping.
E. It translates Layer 2 addresses to Layer 3 addresses.
F. It translates Layer 3 addresses to Layer 2 addresses.
Answer: B,E
Explanation:
Inverse Address Resolution Protocol (Inverse ARP or InARP) is used to obtain Network Layer addresses (for example, IP addresses) of other nodes from Data Link Layer (Layer 2) addresses. It is primarily used in Frame Relay (DLCI) and ATM networks, in which Layer 2 addresses of virtual circuits are sometimes obtained from Layer 2 signaling, and the corresponding Layer 3 addresses must be available before those virtual circuits can be used.
Since ARP translates Layer 3 addresses to Layer 2 addresses, InARP may be described as its inverse. In addition, InARP is implemented as a protocol extension to ARP: it uses the same packet format as ARP, but different operation codes.
Topic 3, Layer 3 Technologies
QUESTION NO: 137
Refer to the exhibit.
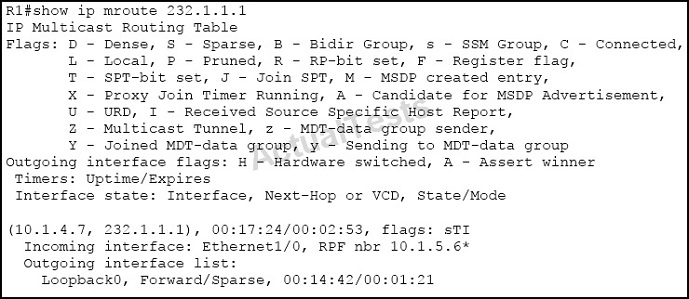
What is the meaning of the asterisk (*) in the output?
A. PIM neighbor 10.1.5.6 is the RPF neighbor for the group 232.1.1.1 for the shared tree.
B. PIM neighbor 10.1.5.6 is the one that is seen as the RPF neighbor when performing the command show ip rpf 10.1.4.7.
C. PIM neighbor 10.1.5.6 is the winner of an assert mechanism.
D. The RPF neighbor 10.1.5.6 is invalid.
Answer: C
Explanation:
RPF neighbor or RPF nbr
IP address of the upstream router to the source. Tunneling indicates that this router is sending data to the RP encapsulated in register packets. The hexadecimal number in parentheses indicates to which RP it is registering. Each bit indicates a different RP if multiple RPs per group are used. If an asterisk (*) appears after the IP address in this field, the RPF neighbor has been learned through an assert.
QUESTION NO: 138
Refer to the exhibit.
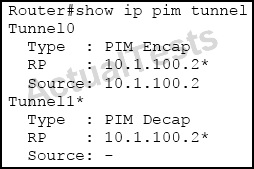 What is the role of this multicast router?
What is the role of this multicast router?
A. a first-hop PIM router
B. a last-hop PIM router
C. a PIM rendezvous point
D. a PIM inter-AS router
Answer: C
QUESTION NO: 139
Refer to the exhibit.
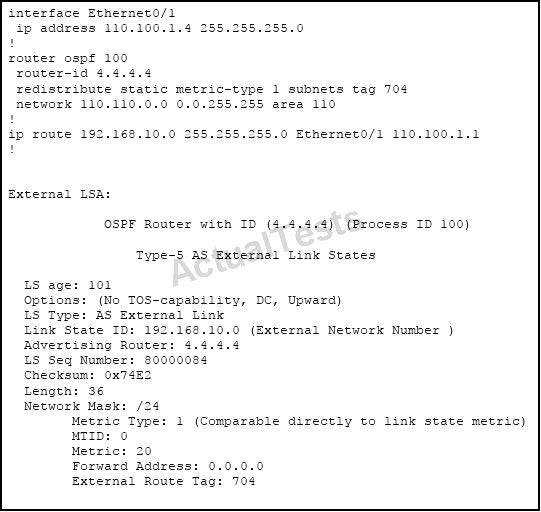 Which option explains why the forwarding address is set to 0.0.0.0 instead of 110.100.1.1?
Which option explains why the forwarding address is set to 0.0.0.0 instead of 110.100.1.1?
A. The interface Ethernet0/1 is in down state.
B. The next-hop ip address 110.100.1.1 is not directly attached to the redistributing router.
C. The next-hop interface (Ethernet0/1) is specified as part of the static route command; therefore, the forwarding address is always set to 0.0.0.0.
D. OSPF is not enabled on the interface Ethernet0/1.
Answer: D
Explanation:
From the output of the “show ip ospf database” command (although this command is not shown) we can conclude this is an ASBR (with Advertising Router is itself) and E0/1 is the ASBR’s next hop interface for other routers to reach network 192.168.10.0.
The Forwarding Address is determined by these conditions:
* The forwarding address is set to 0.0.0.0 if the ASBR redistributes routes and OSPF is not enabled on the next hop interface for those routes.
enabled on the next hop interface for those routes.
* These conditions set the forwarding address field to a non-zero address:
+ OSPF is enabled on the ASBR’s next hop interface AND
+ ASBR’s next hop interface is non-passive under OSPF AND
+ ASBR’s next hop interface is not point-to-point AND
+ ASBR’s next hop interface is not point-to-multipoint AND
+ ASBR’s next hop interface address falls under the network range specified in the router ospf command.
* Any other conditions besides these set the forwarding address to 0.0.0.0.
-> We can see E0/1 interface is not running OSPF because it does not belong to network 110.110.0.0 0.0.255.255 which is declared under OSPF process -> F.A address is set to 0.0.0.0.
QUESTION NO: 140
Refer to the exhibit.
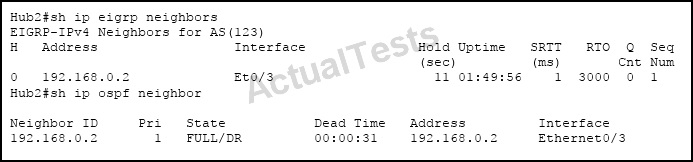
You have configured two routing protocols across this point-to-point link. How many BFD sessions will be established across this link?
A. three per interface
B. one per multicast address
C. one per routing protocol
D. one per interface
Answer: D
Explanation:
Cisco devices will use one Bidirectional Forwarding Detection (BFD) session for multiple client protocols in the Cisco implementation of BFD for Cisco IOS Releases 12.2(18)SXE, 12.0(31)S, and 12.4(4)T. For example, if a network is running OSPF and EIGRP across the same link to the same peer, only one BFD session will be established, and BFD will share session information with both routing protocols.
QUESTION NO: 141
Refer to the exhibit.
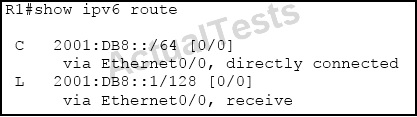 Which statement is true?
Which statement is true?
A. 2001:DB8::1/128 is a local host route, and it can be redistributed into a dynamic routing protocol.
B. 2001:DB8::1/128 is a local host route, and it cannot be redistributed into a dynamic routing protocol.
C. 2001:DB8::1/128 is a local host route that was created because ipv6 unicast-routing is not enabled on this router.
D. 2001:DB8::1/128 is a route that was put in the IPv6 routing table because one of this router's loopback interfaces has the IPv6 address 2001:DB8::1/128.
Answer: B
Explanation:
The local routes have the administrative distance of 0. This is the same adminstrative distance as connected routes. However, when you configure redistributed connected under any routing process, the connected routes are redistributed, but the local routes are not. This behavior allows the networks to not require a large number of host routes, because the networks of the interfaces are advertised with their proper masks. These host routes are only needed on the router that owns the IP address in order to process packets destined to that IP address.
It is normal for local host routes to be listed in the IPv4 and IPv6 routing table for IP addresses of the router's interfaces. Their purpose is to create a corresponding CEF entry as a receive entry so that the packets destined to this IP address can be processed by the router itself. These routes cannot be redistributed into any routing protocol.
QUESTION NO: 142
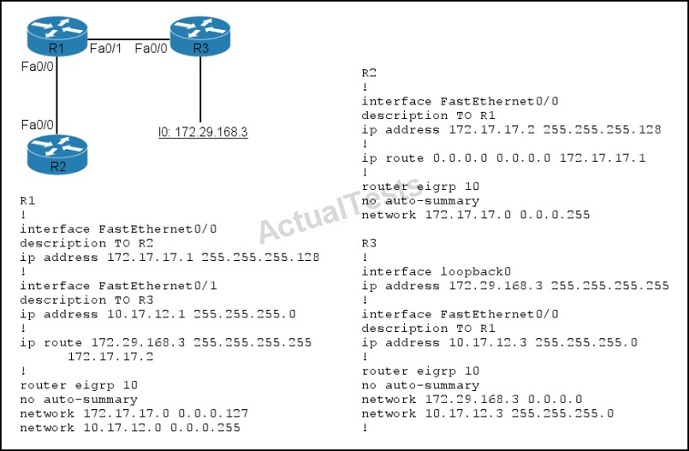
Refer to the exhibit.
Routers R1, R2, and R3 are configured as shown, and traffic from R2 fails to reach 172.29.168.3.
Which action can you take to correct the problem?
A. Correct the static route on R1.
B. Correct the default route on R2.
C. Edit the EIGRP configuration of R3 to enable auto-summary.
D. Correct the network statement for 172.29.168.3 on R3.
Answer: A
Explanation:
On R1 we see there is a wrongly configured static route : ip route 172.29.168.3 255.255.255.255 172.17.17.2. It should be ip route 172.29.168.3 255.255.255.255 10.17.12.3.
QUESTION NO: 143
Refer to the exhibit.

R3 prefers the path through R1 to reach host 10.1.1.1.
Which option describes the reason for this behavior?
A. The OSPF reference bandwidth is too small to account for the higher speed links through R2.
B. The default OSPF cost through R1 is less than the cost through R2.
C. The default OSPF cost through R1 is more than the cost through R2.
D. The link between R2 and R1 is congested.
Answer: A
Explanation:
The default formula to calculate OSPF bandwidth is BW = Bandwidth Reference / interface
bandwidth [bps] = 10^8 / / interface bandwidth [bps]
BW of the R1-R3 link = 10^8 / 100Mbps = 10^8 / 10^8 = 1
BW of the R2-R3 link = 10^8 / 1Gbps = 10^8 / 10^9 = 1 (round up)
Therefore OSPF considers the two above links have the same Bandwidth -> R3 will go to 10.1.1.1 via the R1-R3 link. The solution here is to increase the Bandwidth Reference to a higher value using the “auto-cost reference-bandwidth” command under OSPF router mode. For example:
Router(config)#router ospf 1
Router(config-router)#auto-cost reference-bandwidth 10000
This will increase the reference bandwidth to 10000 Mbps which increases the BW of the R2-R3 link to 10^10 / 10^8 = 100.
QUESTION NO: 144
Refer to the exhibit.

For which reason could a BGP-speaking device in autonomous system 65534 be prevented from installing the given route in its BGP table?
A. The AS number of the BGP is specified in the given AS_PATH.
B. The origin of the given route is unknown.
C. BGP is designed only for publicly routed addresses.
D. The AS_PATH for the specified prefix exceeds the maximum number of ASs allowed.
E. BGP does not allow the AS number 65535.
Answer: A
Explanation:
BGP is considered to be a 'Path Vector' routing protocol rather than a distance vector routing protocol since it utilises a list of AS numbers to describe the path that a packet should take. This list is called the AS_PATH. Loops are prevented because if a BGP speaking router sees it's own AS in the AS_PATH of a route it rejects the route.
QUESTION NO: 145
Which statement about the feasibility condition in EIGRP is true?
A. The prefix is reachable via an EIGRP peer that is in the routing domain of the router.
B. The EIGRP peer that advertises the prefix to the router has multiple paths to the destination.
C. The EIGRP peer that advertises the prefix to the router is closer to the destination than the router.
D. The EIGRP peer that advertises the prefix cannot be used as a next hop to reach the destination.
Answer: C
Explanation:
The advertised metric from an EIGRP neighbor (peer) to the local router is called Advertised Distance (or reported distance) while the metric from the local router to that network is called Feasible Distance. For example, R1 advertises network 10.10.10.0/24 with a metric of 20 to R2. For R2, this is the advertised distance. R2 calculates the feasible distance by adding the metric from the advertised router (R1) to itself. So in this case the feasible distance to network 10.10.10.0/24 is 20 + 50 = 70.

Before a router can be considered a feasible successor, it must pass the feasibility condition rule. In short, the feasibility condition says that if we learn about a prefix from a neighbor, the advertised distance from that neighbor to the destination must be lower than our feasible distance to that same destination.
Therefore we see the Advertised Distance always smaller than the Feasible Distance to satisfy the feasibility condition.
QUESTION NO: 146
Which two statements about the function of the stub feature in EIGRP are true? (Choose two.)
A. It stops the stub router from sending queries to peers.
B. It stops the hub router from sending queries to the stub router.
C. It stops the stub router from propagating dynamically learned EIGRP prefixes to the hub routers.
D. It stops the hub router from propagating dynamically learned EIGRP prefixes to the stub routers.
Answer: B,C
Explanation:
When using the EIGRP Stub Routing feature, you need to configure the distribution and remote routers to use EIGRP, and to configure only the remote router as a stub. Only specified routes are propagated from the remote (stub) router. The router responds to queries for summaries, connected routes, redistributed static routes, external routes, and internal routes with the message "inaccessible." A router that is configured as a stub will send a special peer information packet to all neighboring routers to report its status as a stub router.
Without the stub feature, even after the routes that are sent from the distribution router to the remote router have been filtered or summarized, a problem might occur. If a route is lost somewhere in the corporate network, EIGRP could send a query to the distribution router, which in turn will send a query to the remote router even if routes are being summarized. If there is a problem communicating over the WAN link between the distribution router and the remote router, an EIGRP stuck in active (SIA) condition could occur and cause instability elsewhere in the network. The EIGRP Stub Routing feature allows a network administrator to prevent queries from being sent to the remote router.
QUESTION NO: 147
In which type of EIGRP configuration is EIGRP IPv6 VRF-Lite available?
A. stub
B. named mode
C. classic mode
D. passive
Answer: B
Explanation:
The EIGRP IPv6 VRF Lite feature provides EIGRP IPv6 support for multiple VRFs. EIGRP for IPv6 can operate in the context of a VRF. The EIGRP IPv6 VRF Lite feature provides separation between routing and forwarding, providing an additional level of security because no communication between devices belonging to different VRFs is allowed unless it is explicitly configured. The EIGRP IPv6 VRF Lite feature simplifies the management and troubleshooting of traffic belonging to a specific VRF.
The EIGRP IPv6 VRF Lite feature is available only in EIGRP named configurations.
QUESTION NO: 148
Two routers are trying to establish an OSPFv3 adjacency over an Ethernet link, but the adjacency is not forming. Which two options are possible reasons that prevent OSPFv3 to form between these two routers? (Choose two.)
A. mismatch of subnet masks
B. mismatch of network types
C. mismatch of authentication types
D. mismatch of instance IDs
E. mismatch of area types
Answer: D,E
Explanation:
An OSPFv3 interface must have a compatible configuration with a remote interface before the two can be considered neighbors. The two OSPFv3 interfaces must match the following criteria:
• Hello interval
• Dead interval
• Area ID
• Optional capabilities
The OSPFv3 header includes an instance ID field to identify that OSPFv3 packet for a particular OSPFv3 instance. You can assign the OSPFv3 instance. The interface drops all OSPFv3 packets that do not have a matching OSPFv3 instance ID in the packet header.
QUESTION NO: 149
Like OSPFv2, OSPFv3 supports virtual links. Which two statements are true about the IPv6 address of a virtual neighbor? (Choose two.)
A. It is the link-local address, and it is discovered by examining the hello packets received from the virtual neighbor.
B. It is the link-local address, and it is discovered by examining link LSA received by the virtual neighbor.
C. It is the global scope address, and it is discovered by examining the router LSAs received by the virtual neighbor.
D. Only prefixes with the LA-bit not set can be used as a virtual neighbor address.
E. It is the global scope address, and it is discovered by examining the intra-area-prefix-LSAs received by the virtual neighbor.
F. Only prefixes with the LA-bit set can be used as a virtual neighbor address.
Answer: E,F
Explanation:
OSPF for IPv6 assumes that each router has been assigned link-local unicast addresses on each of the router's attached physical links. On all OSPF interfaces except virtual links, OSPF packets are sent using the interface's associated link-local unicast address as the source address. A router learns the link-local addresses of all other routers attached to its links and uses these addresses as next-hop information during packet forwarding.
On virtual links, a global scope IPv6 address MUST be used as the source address for OSPF protocol packets.
The collection of intra-area-prefix-LSAs originated by the virtual neighbor is examined, with the virtual neighbor's IP address being set to the first prefix encountered with the LA-bit set.
QUESTION NO: 150
Which field is specific to the OPSFv3 packet header, as opposed to the OSPFv2 packet header?
A. checksum
B. router ID
C. AuType
D. instance ID
Answer: D
Explanation:
In OSPFv3, Instance ID is a new field that is used to have multiple OSPF process’ instance per link. By default it is 0 and for any additional instance it is increased, instance ID has local link significance only. OSPFv3 routers will only become neighbors if the instanceIDs match. It is thus possible to have multiple routers on a broadcast domain and all run Ospfv3 but not all of them becoming neighbors.