نمونه سوالات آزمون CCIE Routing and Switching 400-101
QUESTION NO: 181
Refer to the exhibit.
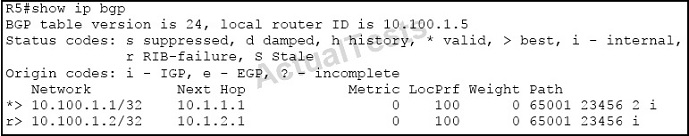 Which two statements are true? (Choose two.)
Which two statements are true? (Choose two.)
A. This router is not 4-byte autonomous system aware.
B. This router is 4-byte autonomous system aware.
C. The prefix 10.100.1.1/32 was learned through an autonomous system number with a length of 4 bytes, and this router is 4-byte autonomous system aware.
D. The prefix 10.100.1.1/32 was learned through an autonomous system number with a length of 4 bytes, and this router is not 4-byte autonomous system aware.
E. The prefix 10.100.1.1/32 was originated from a 4-byte autonomous system.
Answer: A,D
Explanation:
Prior to January 2009, BGP autonomous system (AS) numbers that were allocated to companies were 2-octet numbers in the range from 1 to 65535 as described in RFC 4271, A Border Gateway Protocol 4 (BGP-4). Due to increased demand for AS numbers, the Internet Assigned Number Authority (IANA) started to allocate four-octet AS numbers in the range from 65536 to 4294967295. RFC 5396, Textual Representation of Autonomous System (AS) Numbers, documents three methods of representing AS numbers.
QUESTION NO: 182
Refer to the exhibit.
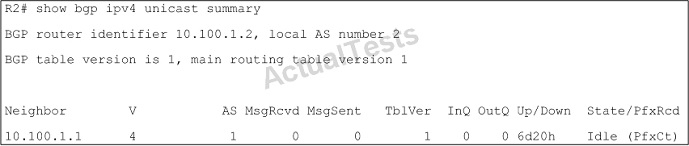 Which command is configured on this router?
Which command is configured on this router?
A. bgp update-delay 60
B. neighbor 10.100.1.1 maximum-prefix 200
C. neighbor 10.100.1.1 maximum-path 2
D. neighbor 10.100.1.1 ebgp-multihop 2
Answer: B
Explanation:
The BGP Maximum-Prefix feature allows you to control how many prefixes can be received from a neighbor. By default, this feature allows a router to bring down a peer when the number of received prefixes from that peer exceeds the configured Maximum-Prefix limit. This feature is commonly used for external BGP peers, but can be applied to internal BGP peers also. When the maximum number of prefixes have been received, the BGP sessions closes into the IDLE state.
QUESTION NO: 183
Refer to the exhibit.
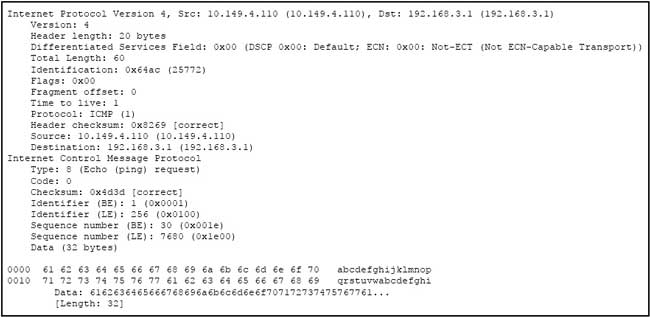
Why is network 172.16.1.0/24 not installed in the routing table?
A. There is no ARP entry for 192.168.1.1.
B. The router cannot ping 192.168.1.1.
C. The neighbor 192.168.1.1 just timed out and BGP will flush this prefix the next time that the BGP scanner runs.
D. There is no route for 192.168.1.1 in the routing table.
Answer: D
Explanation:
Here we see that the next hop IP address to reach the 172.16.1.0 network advertised by the BGP peer is 192.168.1.1. However, the 192.168.1.1 IP is not in the routing table of R3 so it adds the route to the BGP table but marks it as inaccessible, as shown.
QUESTION NO: 184
Refer to the exhibit.
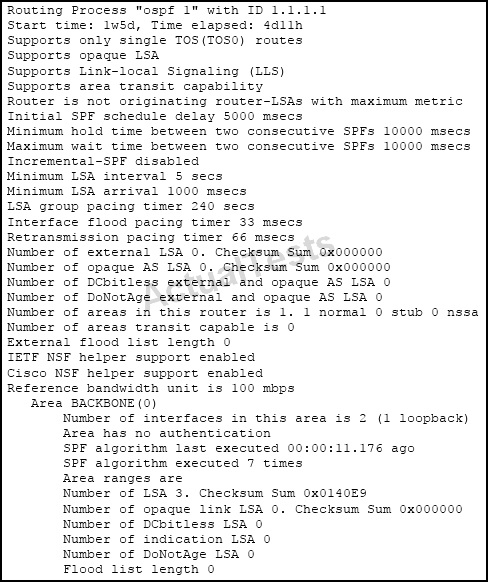
Which two statements are true? (Choose two.)
A. This is the output of the show ip ospf command.
B. This is the output of the show ip protocols command.
C. This router is an ABR.
D. This router is an ASBR.
E. Authentication is not configured for the area.
Answer: A,E
Explanation:
The following is sample output from the show ip ospf command when entered without a specific OSPF process ID with no authentication
Router# show ip ospf
Routing Process "ospf 201" with ID 10.0.0.1 and Domain ID 10.20.0.1
Supports only single TOS(TOS0) routes
Supports opaque LSA
SPF schedule delay 5 secs, Hold time between two SPFs 10 secs
Minimum LSA interval 5 secs. Minimum LSA arrival 1 secs
LSA group pacing timer 100 secs
Interface flood pacing timer 55 msecs
Retransmission pacing timer 100 msecs
Number of external LSA 0. Checksum Sum 0x0
Number of opaque AS LSA 0. Checksum Sum 0x0
Number of DCbitless external and opaque AS LSA 0
Number of DoNotAge external and opaque AS LSA 0
Number of areas in this router is 2. 2 normal 0 stub 0 nssa
External flood list length 0
Area BACKBONE(0)
Number of interfaces in this area is 2
Area has no authentication
SPF algorithm executed 4 times
Area ranges are
Number of LSA 4. Checksum Sum 0x29BEB
Number of opaque link LSA 0. Checksum Sum 0x0
Number of DCbitless LSA 3
Number of indication LSA 0
Number of DoNotAge LSA 0
Flood list length 0
QUESTION NO: 185
Consider a network that mixes link bandwidths from 128 kb/s to 40 Gb/s. Which value should be set for the OSPF reference bandwidth?
A. Set a value of 128.
B. Set a value of 40000.
C. Set a manual OSPF cost on each interface.
D. Use the default value.
E. Set a value of 40000000.
F. Set a value of 65535.
Answer: C
Explanation:
Unlike the metric in RIP which is determined by hop count and EIGRP’s crazy mathematical formulated metric, OSPF is a little more simple. The default formula to calculate the cost for the OSPF metric is (10^8/BW).
By default the metrics reference cost is 100Mbps, so any link that is 100Mbps will have a metric of 1. a T1 interface will have a metric of 64 so in this case if a router is trying to get to a FastEthernet network on a router that is through a T1 the metric would be 65 (64 +1). You do however have the ability to statically specify a metric on a per interface basis by using the ip ospf cost # where the cost is an integer between 1-65535. So the big question is why would you want to statically configure a metric? The biggest advantage of statically configuring an OSPF metric on an interface is to manipulate which route will be chosen dynamically via OSPF. In a nut shell it’s like statically configuring a dynamic protocol to use a specific route. It should also be used when the interface bandwidths vary greatly (some very low bandwidth interfaces and some very high speed interfaces on the same router).
QUESTION NO: 186
C. It is an LSA that is originated by an ASBR, that is flooded throughout the area, and that
describes a route to the ASBR.
D. It is an LSA that is originated by an ABR, that is flooded throughout the AS, and that describes
a route to the ABR.
E. It is an LSA that is originated by an ABR, that is flooded throughout the area, and that describes
a route to the ASBR.
Answer: E
Explanation:
LSA Type 4 (called Summary ASBR LSA) is generated by the ABR to describe an ASBR to routers in other areas so that routers in other areas know how to get to external routes through that ASBR.
QUESTION NO: 187
Refer to the exhibit.
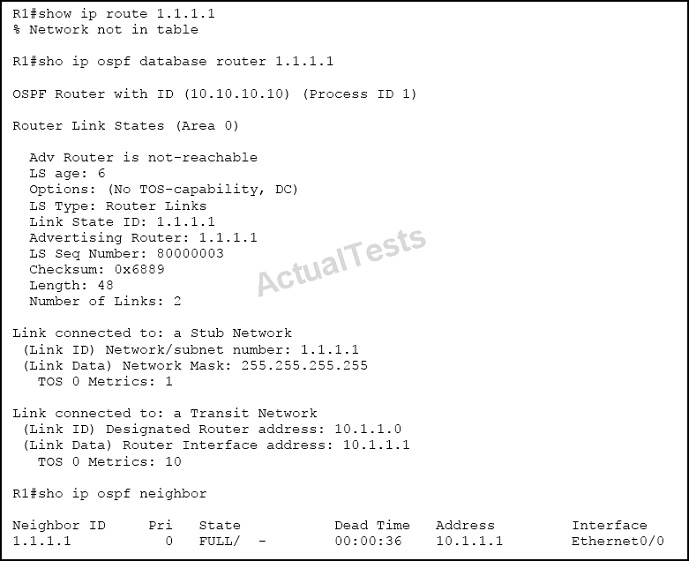 Why is the prefix 1.1.1.1/32 not present in the routing table of R1?
Why is the prefix 1.1.1.1/32 not present in the routing table of R1?
A. There is a duplicate router ID.
B. There is a subnet mask mismatch on Ethernet0/0.
C. The router LSA has an invalid checksum.
D. There is an OSPF network type mismatch that causes the advertising router to be unreachable.
Answer: D
Explanation:
A common problem when using Open Shortest Path First (OSPF) is routes in the database don't appear in the routing table. In most cases OSPF finds a discrepancy in the database so it doesn't install the route in the routing table. Often, you can see the Adv Router is not-reachable message (which means that the router advertising the LSA is not reachable through OSPF) on top of the link-state advertisement (LSA) in the database when this problem occurs.
QUESTION NO: 188
Which authentication method does OSPFv3 use to secure communication between neighbors?
A. plaintext
B. MD5 HMAC
C. PKI
D. IPSec
Answer: D
Explanation:
In order to ensure that OSPFv3 packets are not altered and re-sent to the device, causing the device to behave in a way not desired by its system administrators, OSPFv3 packets must be authenticated. OSPFv3 uses the IPsec secure socket API to add authentication to OSPFv3 packets. This API supports IPv6.
OSPFv3 requires the use of IPsec to enable authentication. Crypto images are required to use authentication, because only crypto images include the IPsec API needed for use with OSPFv3.
QUESTION NO: 189
Which three statements are true about OSPFv3? (Choose three.)
A. The only method to enable OSPFv3 on an interface is via the interface configuration mode.
B. Multiple instances of OSPFv3 can be enabled on a single link.
C. There are two methods to enable OSPFv3 on an interface, either via the interface configuration mode or via the router configuration mode.
D. For OSPFv3 to function, IPv6 unicast routing must be enabled.
E. For OSPFv3 to function, IPv6 must be enabled on the interface.
F. Only one instance of OSPFv3 can be enabled on a single link.
Answer: B,D,E
QUESTION NO: 190
Which statement about OSPF multiaccess segments is true?
A. The designated router is elected first.
B. The designated and backup designated routers are elected at the same time.
C. The router that sent the first hello message is elected first.
D. The backup designated router is elected first.
Answer: D
Explanation:
According to the RFC, the BDR is actually elected first, followed by the DR. The RFC explains why:
“The reason behind the election algorithm’s complexity is the desire for an orderly transition from Backup Designated Router to Designated Router, when the current Designated Router fails. This orderly transition is ensured through the introduction of hysteresis: no new Backup Designated Router can be chosen until the old Backup accepts its new Designated Router responsibilities. The above procedure may elect the same router to be both Designated Router and Backup
Designated Router, although that router will never be the calculating router (Router X) itself.”
QUESTION NO: 191
What are the minimal configuration steps that are required to configure EIGRP HMAC SHA2 authentication?
A. classic router mode, interface XX, authentication mode hmac-sha-256 <password>
B. named router mode, address-family statement, authentication mode hmac-sha-256 <password>
C. named router mode, address-family statement, af-interface default, authentication mode hmacsha- 256 <password>
D. named router mode, address-family statement, authentication mode hmac-sha-256 <password>
Answer: C
Explanation:
The example below shows how to configure EIGRP HMAC-SHA2 on Cisco router:
Device(config)# router eigrp name1
Device(config-router)# address-family ipv4 autonomous-system 45000
Device(config-router-af)# af-interface ethernet 0/0
Device(config-router-af-interface)# authentication mode hmac-sha-256 0 password1
Device(config-router-af-interface)# end
QUESTION NO: 192
Refer to the exhibit.
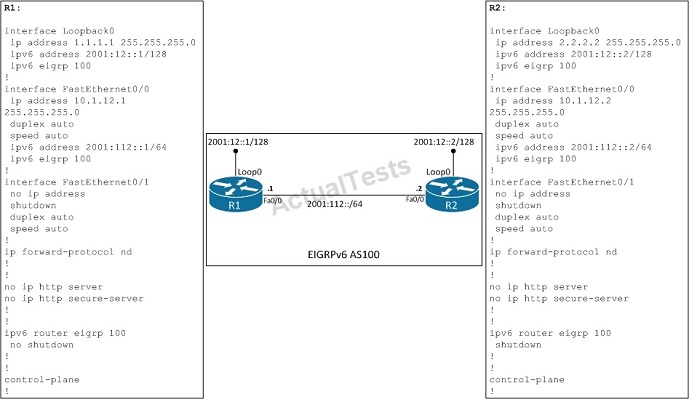 How many EIGRP routes will appear in the routing table of R2?
How many EIGRP routes will appear in the routing table of R2?
A. 0
B. 1
C. 2
D. 3
Answer: A
Explanation:
EIGRPv6 on R2 was shut down so there is no EIGRP routes on the routing table of R2. If we turn on EIGRPv6 on R2 (with “no shutdown” command) then we would see the prefix of the loopback interface of R1 in the routing table of R2.
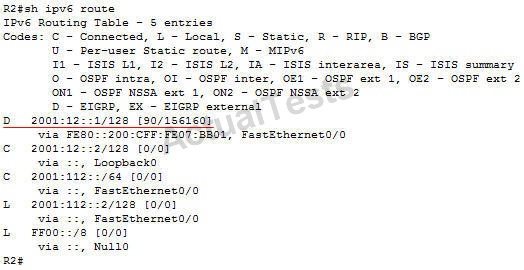
NotE. EIGRPv6 requires the “ipv6 unicast-routing” global command to be turned on first or it will not work.
QUESTION NO: 193
Which two configuration changes should be made on the OTP interface of an EIGRP OTP route reflector? (Choose two.)
A. passive-interface
B. no split-horizon
C. no next-hop-self
D. hello-interval 60, hold-time 180
Answer: B,C
Explanation:
The EIGRP Over the Top feature enables a single end-to-end Enhanced Interior Gateway Routing Protocol (EIGRP) routing domain that is transparent to the underlying public or private WAN transport that is used for connecting disparate EIGRP customer sites. When an enterprise extends its connectivity across multiple sites through a private or a public WAN connection, the service provider mandates that the enterprise use an additional routing protocol, typically the Border Gateway Protocol (BGP), over the WAN links to ensure end-to-end routing. The use of an additional protocol causes additional complexities for the enterprise, such as additional routing processes and sustained interaction between EIGRP and the routing protocol to ensure connectivity, for the enterprise. With the EIGRP Over the Top feature, routing is consolidated into a single protocol (EIGRP) across the WAN.
Perform this task to configure a customer edge (CE) device in a network to function as an EIGRP Route Reflector:
1. enable
2. configure terminal
3. router eigrp virtual-name
4. address-family ipv4 unicast autonomous-system as-number
5. af-interface interface-type interface-number
6. no next-hop-self
7. no split-horizon
8. exit
9. remote-neighbors source interface-type interface-number unicast-listen lisp-encap
10. network ip-address
11. end
Note. Use no next-hop-self to instructs EIGRP to use the received next hop and not the local outbound interface address as the next hop to be advertised to neighboring devices. If no nexthop- self is not configured, the data traffic will flow through the EIGRP Route Reflector.
QUESTION NO: 194
Which statement about the function of poison reverse in EIGRP is true?
A. It tells peers to remove paths that previously might have pointed to this router.
B. It tells peers to remove paths to save memory and bandwidth.
C. It provides reverse path information for multicast routing.
D. It tells peers that a prefix is no longer reachable.
Answer: A
Explanation:
Poison Reverse in EIGRP states: “Once you learn of a route through an interface, advertise it as unreachable back through that same interface”. For more information please read herE.
QUESTION NO: 195
What is the preferred method to improve neighbor loss detection in EIGRP?
A. EIGRP natively detects neighbor down immediately, and no additional feature or configuration is required.
B. BFD should be used on interfaces that support it for rapid neighbor loss detection.
C. Fast hellos (subsecond) are preferred for EIGRP, so that it learns rapidly through its own mechanisms.
D. Fast hellos (one-second hellos) are preferred for EIGRP, so that it learns rapidly through its own mechanisms.
Answer: B
Explanation:
Bi-directional Forwarding Detection (BFD) provides rapid failure detection times between forwarding engines, while maintaining low overhead. It also provides a single, standardized method of link/device/protocol failure detection at any protocol layer and over any media.
QUESTION NO: 196
How does EIGRP derive the metric for manual summary routes?
A. It uses the best composite metric of any component route in the topology table.
B. It uses the worst composite metric of any component route in the topology table.
C. It uses the best metric vectors of all component routes in the topology table.
D. It uses the worst metric vectors of all component routes in the topology table.
Answer: A
QUESTION NO: 197
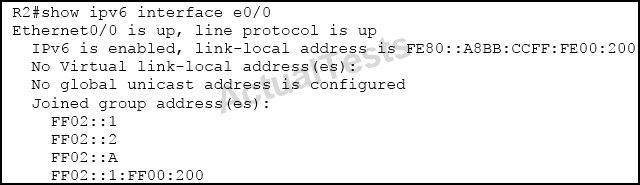
Refer to the exhibit.
Which part of the joined group addresses list indicates that the interface has joined the EIGRP multicast group address?
A. FF02::1
B. FF02::1:FF00:200
C. FF02::A
D. FF02::2
Answer: C
Explanation:
FF02::A is an IPv6 link-local scope multicast addresses. This address is for all devices on a wire that want to "talk" EIGRP with one another.
QUESTION NO: 198
EIGRP allows configuration of multiple MD5 keys for packet authentication to support easy rollover from an old key to a new key. Which two statements are true regarding the usage of multiple authentication keys? (Choose two.)
A. Received packets are authenticated by the key with the smallest key ID.
B. Sent packets are authenticated by all valid keys, which means that each packet is replicated as many times as the number of existing valid keys.
C. Received packets are authenticated by any valid key that is chosen.
D. Sent packets are authenticated by the key with the smallest key ID.
Answer: C,D
QUESTION NO: 199
Refer to the exhibit.
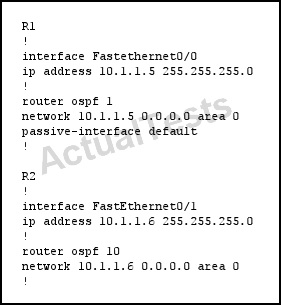 Which additional configuration is necessary for R1 and R2 to become OSPF neighbors?
Which additional configuration is necessary for R1 and R2 to become OSPF neighbors?
A. R1
!
router ospf 1
no passive-interface Fastethernet0/0
!
B. R2
!
router ospf 10
no network 10.1.1.6 0.0.0.0 area 0
network 10.1.1.6 0.0.0.0 area 1
!
C. R1
!
interface FastEthernet0/0
ip ospf mtu-ignore
!
R2
!
interface FastEthernet0/1
ip ospf mtu-ignore
!
D. R1
!
no router ospf 1
router ospf 10
network 10.1.1.5 0.0.0.0 area 0
Answer: A
Explanation:
Because the passive interface default command is used, by default all interfaces are passive and no neighbors will form on these interfaces. We need to disable passive interface on the link to R2 by using the “no passive-interface Fastethernet0/0” on R1 under OSPF.
QUESTION NO: 200
Consider an OSPFv3 network with four parallel links between each pair of routers. Which measure can you use to reduce the CPU load and at the same time keep all links available for ECMP?
A. Configure some interfaces as passive interface.
B. Configure ipv6 ospf priority 0 on some interfaces.
C. Configure some routers with a distribute list in ingress of the OSPFv3 process.
D. Configure ipv6 ospf database-filter all out on some interfaces.
Answer: D
Explanation:
To filter outgoing link-state advertisements (LSAs) to an Open Shortest Path First version 3 (OSPFv3) interface, use the ipv6 ospf database-filter all out command in interface configuration mode. This can be done on some of the links to reduce the CPU load while still ensuring that all links in the equal cost path are still being used.
QUESTION NO: 201
Refer to the exhibit.
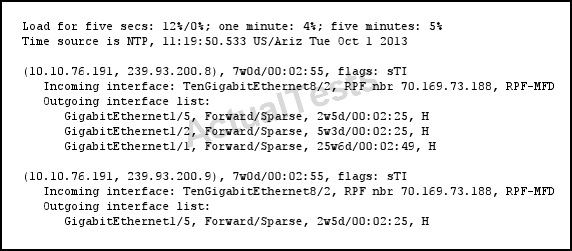 Which two statements about the device that generated the output are true? (Choose two.)
Which two statements about the device that generated the output are true? (Choose two.)
A. The SPT-bit is set.
B. The sparse-mode flag is set.
C. The RP-bit is set.
D. The source-specific host report was received.
Answer: A,D
QUESTION NO: 202
Refer to the exhibit.
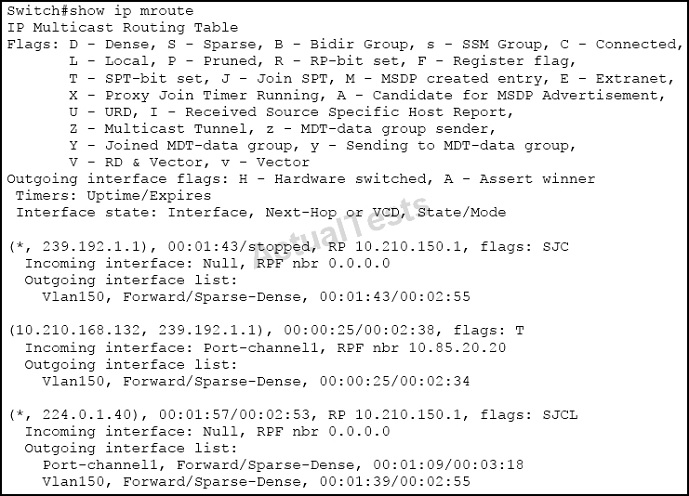 Which three statements about the output are true? (Choose three.)
Which three statements about the output are true? (Choose three.)
A. This switch is currently receiving a multicast data stream that is being forwarded out VLAN 150.
B. A multicast receiver has requested to join one or more of the multicast groups.
C. Group 224.0.1.40 is a reserved address, and it should not be used for multicast user data transfer.
D. One or more multicast groups are operating in PIM dense mode.
E. One or more of the multicast data streams will be forwarded out to neighbor 10.85.20.20.
F. Group 239.192.1.1 is a reserved address, and it should not be used for multicast user data transfer.
Answer: A,B,C
Explanation:
A; VLAN 150 shows up in the outgoing interface list so those specific multicast streams are being forwarded to this VLAN.
B. A receiver has requested to receive the multicast stream associated with the multicast address of 239.192.1.1, that is why this stream appears in the mroute table.
C. The 224.0.1.40 is a reserved multicast group for cisco's Rp descovery. All cisco routers are members of this grup by default and listen to this group for Cisco RP discovery messages advertised by mapping agent even if it is not configured
QUESTION NO: 203
Which statement about the RPF interface in a BIDIR-PIM network is true?
A. In a BIDIR-PIM network, the RPF interface is always the interface that is used to reach the PIM rendezvous point.
B. In a BIDIR-PIM network, the RPF interface can be the interface that is used to reach the PIM rendezvous point or the interface that is used to reach the source.
C. In a BIDIR-PIM network, the RPF interface is always the interface that is used to reach the source.
D. There is no RPF interface concept in BIDIR-PIM networks.
Answer: A
Explanation:
RPF stands for "Reverse Path Forwarding". The RPF Interface of a router with respect to an address is the interface that the MRIB indicates should be used to reach that address. In the case of a BIDIR-PIM multicast group, the RPF interface is determined by looking up the Rendezvous Point Address in the MRIB. The RPF information determines the interface of the router that would be used to send packets towards the Rendezvous Point Link for the group.
QUESTION NO: 204
Which technology is an application of MSDP, and provides load balancing and redundancy between the RPs?
A. static RP
B. PIM BSR
C. auto RP
D. anycast RP
Answer: D
Explanation:
Using Anycast RP is an implementation strategy that provides load sharing and redundancy in Protocol Independent Multicast sparse mode (PIM-SM) networks. Anycast RP allows two or more rendezvous points (RPs) to share the load for source registration and the ability to act as hot backup routers for each other. Multicast Source Discovery Protocol (MSDP) is the key protocol that makes Anycast RP possible.
QUESTION NO: 205
Which two statements are true about IPv6 multicast? (Choose two.)
A. Receivers interested in IPv6 multicast traffic use IGMPv6 to signal their interest in the IPv6 multicast group.
B. The PIM router with the lowest IPv6 address becomes the DR for the LAN.
C. An IPv6 multicast address is an IPv6 address that has a prefix of FF00::/8.
D. The IPv6 all-routers multicast group is FF02:0:0:0:0:0:0:2.
Answer: C,D
Explanation:
Multicast addresses in IPv6 have the prefix ff00::/8.
Well-known IPv6 multicast addresses
Address
Description
ff02::1
All nodes on the local network segment
ff02::2
All routers on the local network segment
QUESTION NO: 206
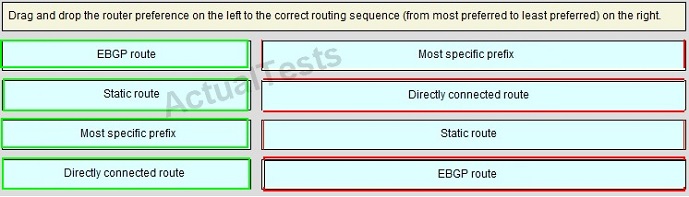
Drag and Drop
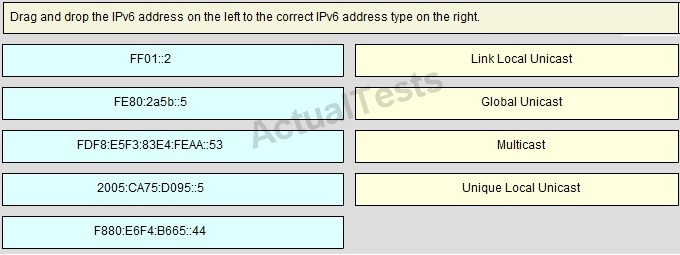
Answer:
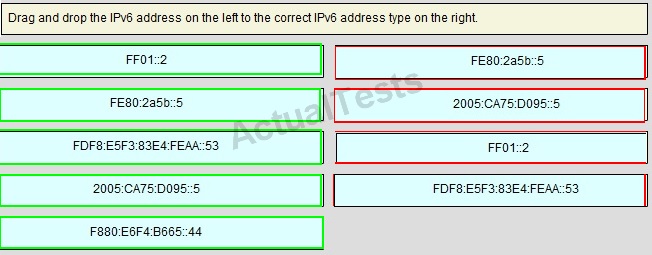
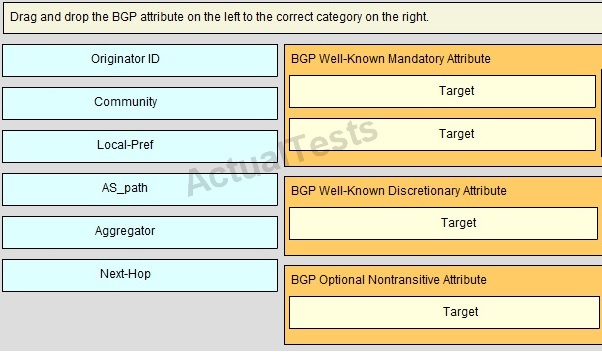
QUESTION NO: 207
Drag and Drop
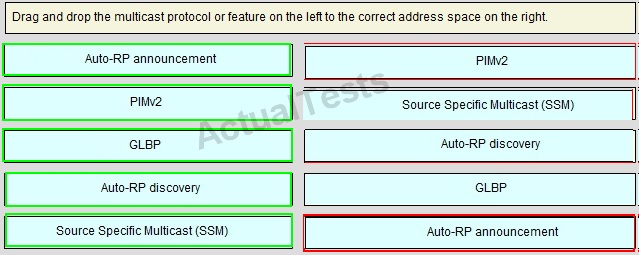
Answer:
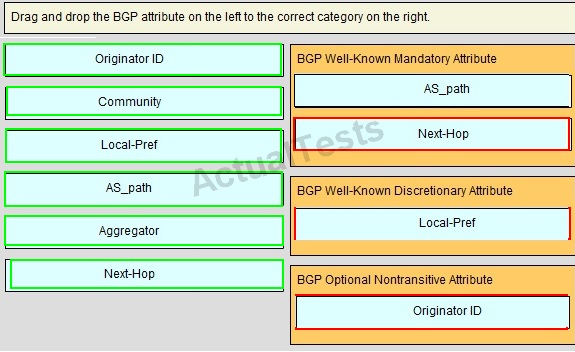
QUESTION NO: 208
Drag and Drop
Answer:
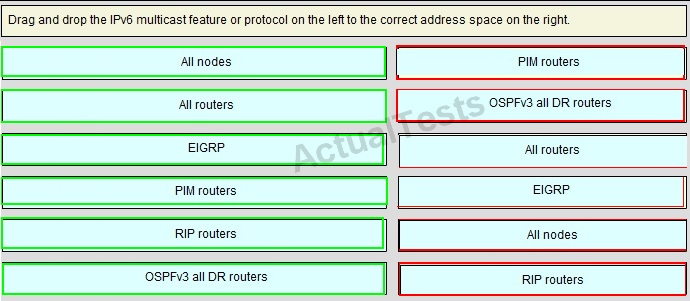
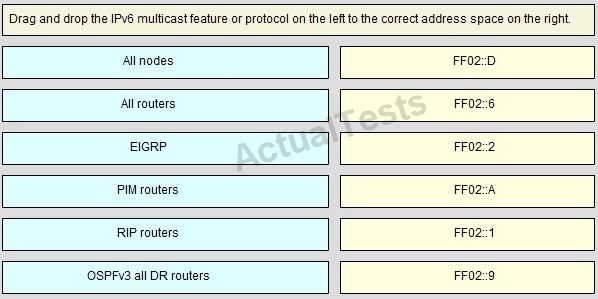
QUESTION NO: 209
Drag and Drop
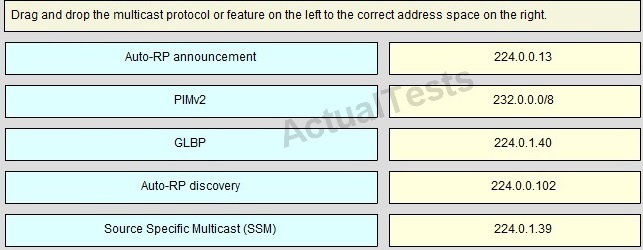
Answer:
QUESTION NO: 210
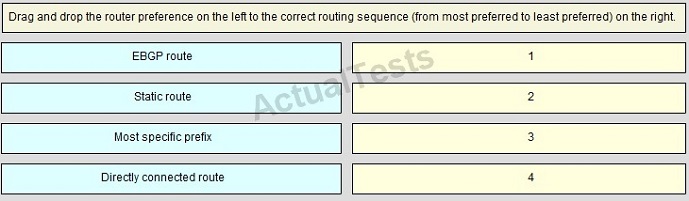
Answer: