نمونه سوالات آزمون CCIE Routing and Switching 400-101
QUESTION NO: 31 Drag & Drop
Answer:
QUESTION NO: 32 Drag & Drop
Answer:
QUESTION NO: 33
Which two Cisco Express Forwarding tables are located in the data plane? (Choose two.)
A. the forwarding information base
B. the label forwarding information base
C. the IP routing table
D. the label information table
E. the adjacency table
Answer: A,B
Explanation:
The control plane runs protocols such as OSPF, BGP, STP, LDP. These protocols are needed so that routers and switches know how to forward packets and frames.
The data plane is where the actual forwarding takes place. The data plane is populated based on the protocols running in the control plane. The Forwarding Information Base (FIB) is used for IP traffic and the Label FIB is used for MPLS.
QUESTION NO: 34
Which option is the most effective action to avoid packet loss due to microbursts?
A. Implement larger buffers.
B. Install a faster CPU.
C. Install a faster network interface.
D. Configure a larger tx-ring size.
Answer: A
Explanation:
You can't avoid or prevent them as such without modifying the sending host's application/network stack so it smoothes out the bursts. However, you can manage microbursts by tuning the size of receive buffers / rings to absorb occasional microbursts.
QUESTION NO: 35
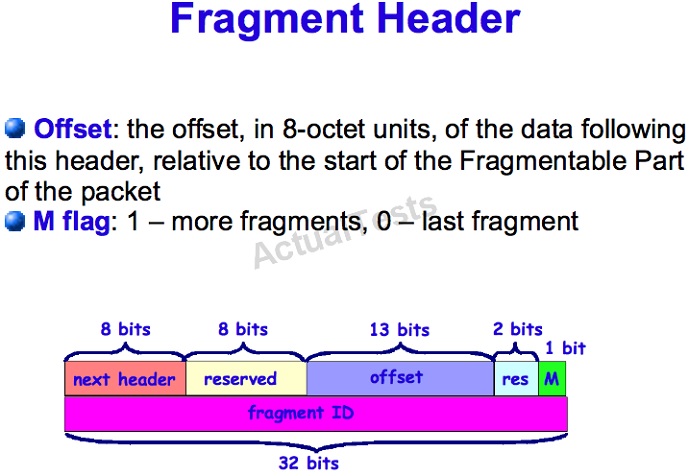
Which two statements about packet fragmentation on an IPv6 network are true? (Choose two.)
A. The fragment header is 64 bits long.
B. The identification field is 32 bits long.
C. The fragment header is 32 bits long.
D. The identification field is 64 bits long.
E. The MTU must be a minimum of 1280 bytes.
F. The fragment header is 48 bits long.
Answer: A,B
Explanation:
The fragment header is shown below, being 64 bits total with a 32 bit identification field:
QUESTION NO: 36
You are backing up a server with a 1 Gbps link and a latency of 2 ms. Which two statements about the backup are true? (Choose two.)
A. The bandwidth delay product is 2 Mb.
B. The default TCP send window size is the limiting factor.
C. The default TCP receive window size is the limiting factor.
D. The bandwidth delay product is 500 Mb.
E. The bandwidth delay product is 50 Mb.
Answer: A,C
Explanation:
1 Gbps is the same as 1000 Mbps, and 1000Mb x .0002 = 2 Mbps. With TCP based data transfers, the receive window is always the limiting factor, as the sender is generally able to send traffic at line rate, but then must wait for the acknowledgements to send more data.
QUESTION NO: 37
Which two pieces of information does RTCP use to inform endpoint devices about the RTP flow?(Choose two.)
A. the transmitted octet
B. the lost packet count
C. session control function provisioning information
D. the CNAME for session participants
E. the authentication method
F. MTU size changes in the path of the flow
Answer: A,B
Explanation:
RTCP transports statistics for a media connection and information such as transmitted octet and packet counts, packet loss, packet delay variation, and round-trip delay time. An application may use this information to control quality of service parameters, perhaps by limiting flow, or using a different codec.
QUESTION NO: 38 Drag & Drop
Answer:

QUESTION NO: 39 Drag & Drop
Answer:
QUESTION NO: 40 Drag & Drop
Answer:
QUESTION NO: 41
How many hash buckets does Cisco Express Forwarding use for load balancing?
A. 8
B. 16
C. 24
D. 32
Answer: B
Explanation:
In order to understand how the load balance takes place, you must first see how the tables relate. The Cisco Express Forwarding table points to 16 hash buckets (load share table), which point to the adjacency table for parallel paths. Each packet to be switched is broken up into the source and destination address pair and checked against the loadshare table.
QUESTION NO: 42
Which three features require Cisco Express Forwarding? (Choose three.)
A. NBAR
B. AutoQoS
C. fragmentation
D. MPLS
E. UplinkFast
F. BackboneFast
Answer: A,B,D
Explanation:
QoS Features That Require CEF
These class-based QoS features are supported only on routers that run CEF.
• Network Based Application Recognition (NBAR) provides intelligent network classification. For more information, refer to Network Based Application Recognition.
•The AutoQoS -VoIP feature simplifies and speeds up the implementation and provisioning of QoS for VoIP traffic. This feature is enabled with the help of the auto qos voip command. CEF must be enabled at the interface or ATM PVC before the auto qos command can be used. For more information about this feature and its prerequisites, refer to AutoQoS - VoIP.
From MPLS Fundamentals - Luc De Ghein
Why Is CEF Needed in MPLS Networks?
Concerning MPLS, CEF is special for a certain reason; otherwise, this book would not explicitly cover it. Labeled packets that enter the router are switched according to the label forwarding information base (LFIB) on the router. IP packets that enter the router are switched according to the CEF table on the router. Regardless of whether the packet is switched according to the LFIB or the CEF table, the outgoing packet can be a labeled packet or an IP packet
QUESTION NO: 43
Which two options are interface requirements for turbo flooding? (Choose two.)
A. The interface is Ethernet.
B. The interface is configured for ARPA encapsulation.
C. The interface is PPP.
D. The interface is configured for GRE encapsulation.
E. The interface is configured for 802.1Q encapsulation.t.
Answer: A,B
Explanation:
In the switch, the majority of packets are forwarded in hardware; most packets do not go through the switch CPU. For those packets that do go to the CPU, you can speed up spanning tree-based UDP flooding by a factor of about four to five times by using turbo-flooding. This feature is supported over Ethernet interfaces configured for ARPA encapsulation.
QUESTION NO: 44
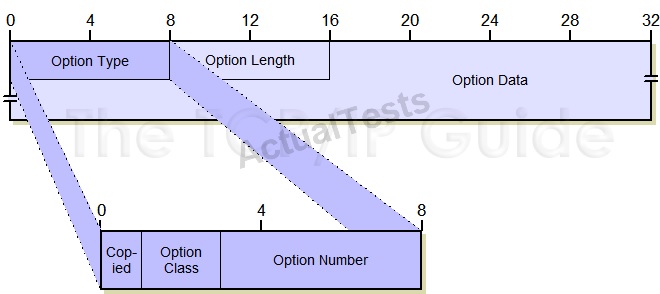
Which three option are sub-subfields of the IPv4 Option Type subfield? (Choose three.)
A. Option Class
B. GET
C. Copied
D. PUSH
E. Option Number
F. TTL
Answer: A,C,E
Explanation:
Each IP option has its own subfield format, generally structured as shown below. For most
options, all three subfields are useD. Option Type, Option Length and Option Data.
QUESTION NO: 45
Which TCP mechanism prevents the sender from sending data too quickly for the receiver to process?
A. Congestion control
B. Error detection
C. Selective acknowledgement
D. Flow control
Answer: D
Explanation:
In data communications, flow control is the process of managing the rate of data transmission between two nodes to prevent a fast sender from overwhelming a slow receiver. It provides a mechanism for the receiver to control the transmission speed, so that the receiving node is not overwhelmed with data from transmitting node.
QUESTION NO: 46
Which two packet types does an RTP session consist of? (Choose two.)
A. TCP
B. RTCP
C. RTP
D. ICMP
E. BOOTP
F. ARP
Answer: B.C
Explanation:
An RTP session is established for each multimedia stream. A session consists of an IP address with a pair of ports for RTP and RTCP. For example, audio and video streams use separate RTP sessions, enabling a receiver to deselect a particular stream. The ports which form a session are negotiated using other protocols such as RTSP (using SDP in the setup method) and SIP. According to the specification, an RTP port should be even and the RTCP port is the next higher odd port number.
QUESTION NO: 47
Which technology can create a filter for an embedded packet capture?
A. Control plane policing
B. Access lists
C. NBAR
D. Traffic shaping
Answer: B
Explanation:
A filter can be applied to limit the capture to desired traffic. Define an Access Control List (ACL) within config mode and apply the filter to the buffer:
ip access-list extended BUF-FILTER
permit ip host 192.168.1.1 host 172.16.1.1
permit ip host 172.16.1.1 host 192.168.1.1
monitor capture buffer BUF filter access-list BUF-FILTER
QUESTION NO: 48
Which option describes a limitation of Embedded Packet Capture?
A. It can capture data only on physical interfaces and subinterfaces.
B. It can store only packet data.
C. It can capture multicast packets only on ingress.
D. It can capture multicast packets only on egress.
Answer: C
QUESTION NO: 49
Refer to the exhibit.
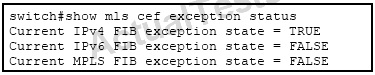 A Cisco Catalyst 6500 Series Switch experiences high CPU utilization. What can be the cause of this issue, and how can it be prevented?
A Cisco Catalyst 6500 Series Switch experiences high CPU utilization. What can be the cause of this issue, and how can it be prevented?
A. The hardware routing table is full. Redistribute from BGP into IGP.
B. The software routing table is full. Redistribute from BGP into IGP.
C. The hardware routing table is full. Reduce the number of routes in the routing table.
D. The software routing table is full. Reduce the number of routes in the routing table.
Answer: C
QUESTION NO: 50
Refer to the exhibit.
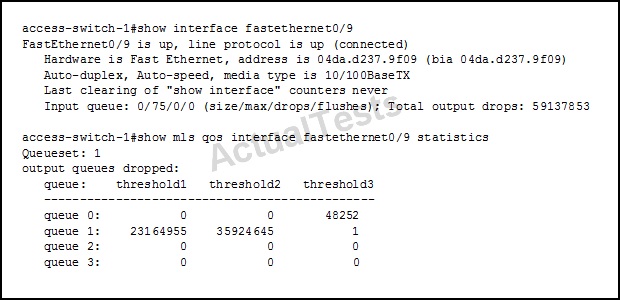
Your network is suffering excessive output drops. Which two actions can you take to resolve the problem? (Choose two.)
A. Install a switch with larger buffers.
B. Configure a different queue set.
C. Reconfigure the switch buffers.
D. Configure the server application to use TCP.
E. Update the server operating system.
Answer: A,B
Explanation:
Installing a switch with larger buffers and correctly configuring the buffers can solve output queue problems.
For each queue we need to configure the assigned buffers. The buffer is like the ‘storage’ space for the interface and we have to divide it among the different queues. This is how to do it:
mls qos queue-set output <queue set> buffers Q1 Q2 Q3 Q4
In this example, there is nothing hitting queue 2 or queue 3 so they are not being utilized.
QUESTION NO: 51 Drag and Drop
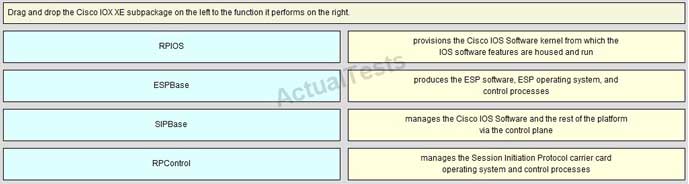
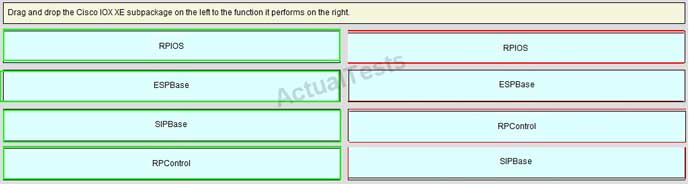
Drag and drop the Cisco IOS XE subpackage on the left to the function it performs on the right.
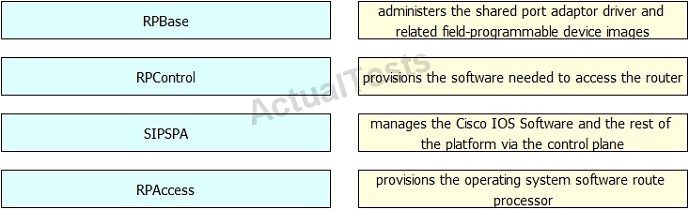
Answer: B

QUESTION NO: 52
Which two Cisco IOS XE commands can install a subpackage onto a router? (Choose two.)
B. boot system flash bootflash:filename
C. copy sourceUrl destinationUrl
D. license install file storedLocationUrl
E. issu loadversion rp identifier file diskType imageFilename
F. config-register value
Answer: A,C
Explanation:
In the following example, the request platform software package install command is used to upgrade a consolidated package running on RP 0. The force option, which forces the upgrade past any prompt (such as already having the same consolidated package installed), is used in this example.
Router# request platform software package install rp 0 file bootflash:asr1000rp1- adventerprisek9.02.01.00.122-33.XNA.bin force
To upgrade a consolidated package on the Cisco ASR 1000 Series Routers using the copy command, copy the consolidated package into the bootflash: directory on the router using the copy command as you would on most other Cisco routers. After making this copy, configure the router to boot using the consolidated package file.
In the following example, the consolidated package file is copied onto the bootflash: file system from TFTP. The config-register is then set to boot using boot system commands, and the boot system commands instruct the router to boot using the consolidated package stored in the bootflash: file system. The new configuration is then saved using the copy running-config startup-config command, and the system is then reloaded to complete the process.
QUESTION NO: 53
Which two statements about Cisco Express Forwarding are true? (Choose two.)
A. Cisco Express Forwarding tables contain reachability information and adjacency tables contain forwarding information.
B. Cisco Express Forwarding tables contain forwarding information and adjacency tables contain reachability information.
C. Changing MAC header rewrite strings requires cache validation.
D. Adjacency tables and Cisco Express Forwarding tables can be built separately.
E. Adjacency tables and Cisco Express Forwarding tables require packet process switching.
Answer: A,D
Explanation:
Information conventionally stored in a route cache is stored in several data structures for Cisco Express Forwarding switching. The data structures provide optimized lookup for efficient packet forwarding. The two main components of Cisco Express Forwarding operation are the forwarding information base (FIB) and the adjacency tables.
The FIB is conceptually similar to a routing table or information base. A router uses this lookup table to make destination-based switching decisions during Cisco Express Forwarding operation. The FIB is updated when changes occur in the network and contains all routes known at the time. Adjacency tables maintain Layer 2 next-hop addresses for all FIB entries.
QUESTION NO: 54
Which TCP feature allows a client to request a specific packet that was lost?
A. flow control
B. sliding window
C. fast recovery
D. selective acknowledgment
Answer: D
Explanation:
The TCP Selective Acknowledgment feature improves performance if multiple packets are lost from one TCP window of data.
Prior to this feature, because of limited information available from cumulative acknowledgments, a TCP sender could learn about only one lost packet per-round-trip time. An aggressive sender could choose to resend packets early, but such re-sent segments might have already been successfully received.
The TCP selective acknowledgment mechanism helps improve performance. The receiving TCP host returns selective acknowledgment packets to the sender, informing the sender of data that has been received. In other words, the receiver can acknowledge packets received out of order. The sender can then resend only missing data segments (instead of everything since the first missing packet).
Prior to selective acknowledgment, if TCP lost packets 4 and 7 out of an 8-packet window, TCP would receive acknowledgment of only packets 1, 2, and 3. Packets 4 through 8 would need to be re-sent. With selective acknowledgment, TCP receives acknowledgment of packets 1, 2, 3, 5, 6, and 8. Only packets 4 and 7 must be re-sent.
TCP selective acknowledgment is used only when multiple packets are dropped within one TCP window. There is no performance impact when the feature is enabled but not used. Use the ip tcp selective-ack command in global configuration mode to enable TCP selective acknowledgment. Refer to RFC 2018 for more details about TCP selective acknowledgment.
QUESTION NO: 55
Which two solutions can reduce UDP latency? (Choose two.)
A. fast retransmission
B. fast recovery
C. fast start
D. low-latency queuing
E. IP service level agreements
F. congestion-avoidance algorithm
Answer: D,E
Explanation:
IP SLA uses active traffic monitoring, which generates traffic in a continuous, reliable, and predictable manner to measure network performance. IP SLA sends data across the network to measure performance between multiple network locations or across multiple network paths. It simulates network data and IP services, and collects network performance information in real time.
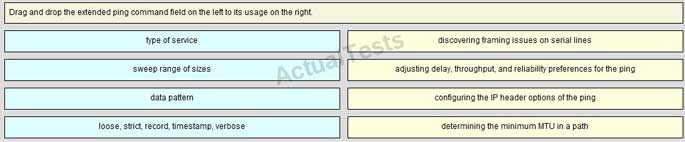
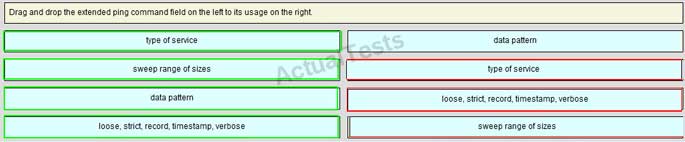
QUESTION NO: 56 Drag & Drop
Drag and drop the extended ping command field on the left to its usage on the right.
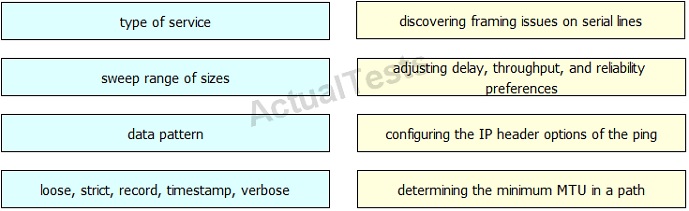
Answer:

QUESTION NO: 57 Drag and Drop
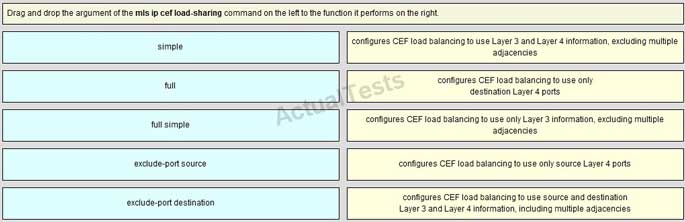
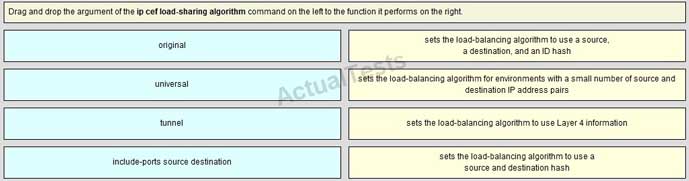
Drag and drop the argument of the mpls ip cef load-sharing command on the left to the function it performs on the right.
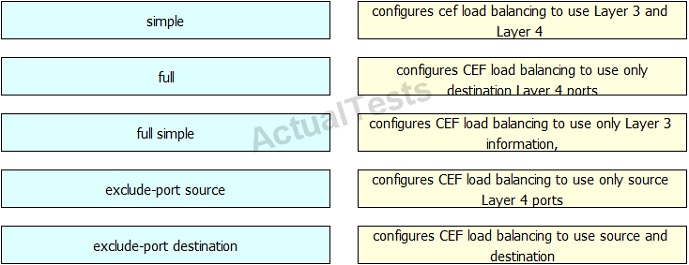
Answer:
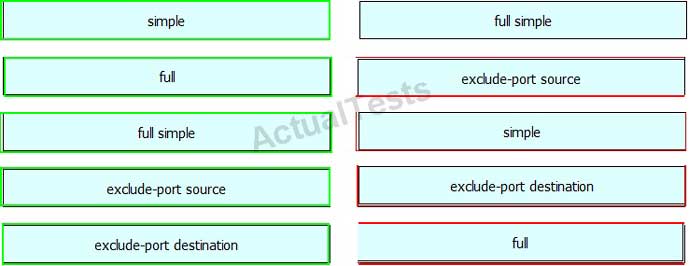
QUESTION NO: 58
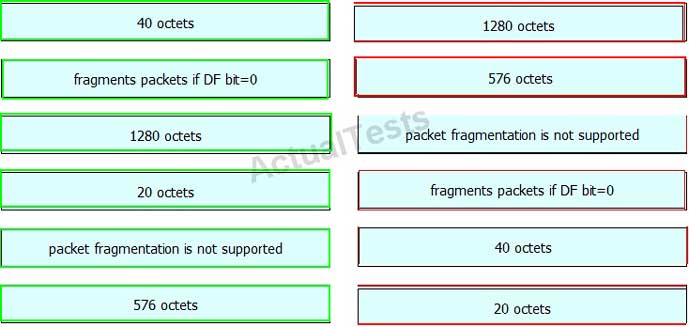
Drag and drop the fragmentation characteristics on the left to the corresponding protocol on the right.
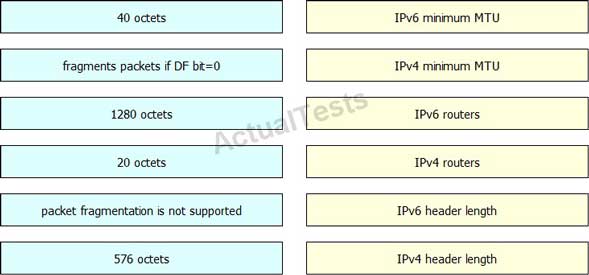
Answer:
Topic 2, Layer 2 Technologies
QUESTION NO: 59
Refer to the exhibit.
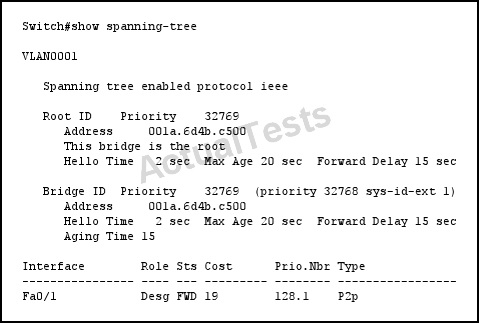 If you change the Spanning Tree Protocol from pvst to rapid-pvst, what is the effect on the interface Fa0/1 port state?
If you change the Spanning Tree Protocol from pvst to rapid-pvst, what is the effect on the interface Fa0/1 port state?
A. It transitions to the listening state, and then the forwarding state.
B. It transitions to the learning state and then the forwarding state.
C. It transitions to the blocking state, then the learning state, and then the forwarding state.
D. It transitions to the blocking state and then the forwarding state.
Answer: C
QUESTION NO: 60
Refer to the exhibit.Which type of port would have root guard enabled on it?
A. A root port
B. An alternate port
C. A blocked port
D. A designated port
Answer: D
Explanation:
The root guard feature provides a way to enforce the root bridge placement in the network. The root guard ensures that the port on which root guard is enabled is the designated port. Normally, root bridge ports are all designated ports, unless two or more ports of the root bridge are connected together. If the bridge receives superior STP Bridge Protocol Data Units (BPDUs) on a root guard-enabled port, root guard moves this port to a root-inconsistent STP state. This rootinconsistent state is effectively equal to a listening state. No traffic is forwarded across this port. In this way, the root guard enforces the position of the root bridge.