
نمونه سوالات آزمون CCIE Routing and Switching 400-101
QUESTION NO: 211
Drag and Drop
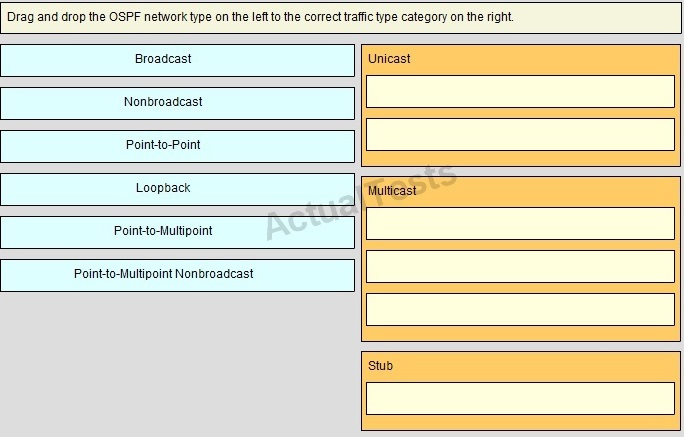
Answer:
QUESTION NO: 212
Refer to the exhibit.
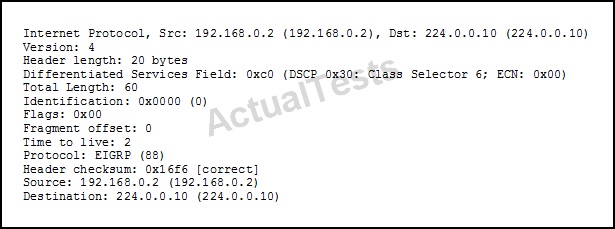 Which two pieces of information in this Wireshark capture indicate that you are viewing EIGRP traffic? (Choose two.)
Which two pieces of information in this Wireshark capture indicate that you are viewing EIGRP traffic? (Choose two.)
A. the header length
B. the protocol number
C. the destination address
D. the Class Selector
E. the source address
F. the header checksum
Answer: B,C
Explanation:
EIGRP uses protocol number 88, which shows as EIGRP in the capture. Also, we in the capture that the destination IP address is 224.0.0.10, which is the Enhanced Interior Gateway Routing Protocol (EIGRP) group address is used to send routing information to all EIGRP routers on a network segment.
QUESTION NO: 213
When BGP route reflectors are used, which attribute ensures that a routing loop is not created?
A. weight
B. local preference
C. multiexit discriminator
D. originator ID
Answer: D
Explanation:
As the iBGP learned routes are reflected, routing information may loop. The route reflector model has the following mechanisms to avoid routing loops:
* Originator ID is an optional, nontransitive BGP attribute. It is a 4-byte attributed created by a route reflector. The attribute carries the router ID of the originator of the route in the local autonomous system. Therefore, if a misconfiguration causes routing information to come back to the originator, the information is ignored.
* Cluster-list is an optional, nontransitive BGP attribute. It is a sequence of cluster IDs that the route has passed. When a route reflector reflects a route from its clients to nonclient peers, and vice versa, it appends the local cluster ID to the cluster-list. If the cluster-list is empty, a new cluster-list is created. Using this attribute, a route reflector can identify if routing information is looped back to the same cluster due to misconfiguration. If the local cluster ID is found in the cluster-list, the advertisement is ignored.
QUESTION NO: 214
Refer to the exhibit.
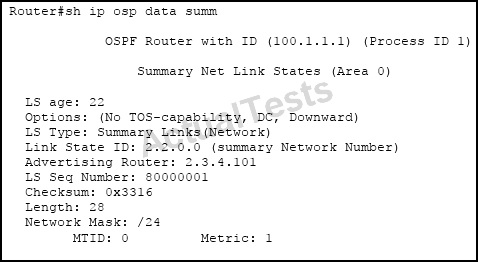
Which statement is true about the downward bit?
A. It forces the CE router to use a backup link instead of sending traffic via MPLS VPN.
B. It informs the PE router that the LSA metric has been recently decreased to 1 and that partial SPF calculation cannot be delayed.
C. It forces the CE router to install the LSA with the downward bit set into its routing table as a discard route.
D. It informs the PE router that the LSA was already redistributed into BGP by another PE router and that the LSA must not be redistributed into BGP again.
Answer: D
Explanation:
From RFC 4577, specifically section 4.2.5.1
When a type 3 LSA is sent from a PE router to a CE router, the DN bit [OSPF-DN] in the LSA Options field MUST be set. This is used to ensure that if any CE router sends this type 3 LSA to a PE router, the PE router will not redistribute it further.
When a PE router needs to distribute to a CE router a route that comes from a site outside the latter’s OSPF domain, the PE router presents itself as an ASBR (Autonomous System Border Router), and distributes the route in a type 5 LSA. The DN bit [OSPF-DN] MUST be set in these LSAs to ensure that they will be ignored by any other PE routers that receive them.
QUESTION NO: 215
Which regular expression will match prefixes that originated from AS200?
A. ^$
B. ^200_
C. _200$
D. ^200)
E. _200_
Answer: C
Explanation:
Example on how to deny all prefixes originated in Autonomous System 200
router bgp 100
neighbor 10.1.1.1 remote-as 65535
neighbor 10.1.1.1 route-map map1 in
!
route-map map1 permit 10
match as-path 1
!
ip as-path access-list 5 deny _200$
ip as-path access-list 5 permit .*
QUESTION NO: 216
Which statement describes the difference between a stub area and a totally stub area?
A. The ABR advertises a default route to a totally stub area and not to a stub area.
B. Stub areas do not allow LSA types 4 and 5, while totally stub areas do not allow LSA types 3, 4, and 5.
C. Totally stub areas allow limited external routes in the area via a special type 7 LSA, while stub areas do not
D. Stub areas do not allow external LSAs, ASBR summary LSAs, or summary LSAs with the exception of a default route originated by the ABR via a summary LSA.
Answer: A
QUESTION NO: 217
Which two statements are true about IS-IS? (Choose two.)
A. IS-IS DIS election is nondeterministic.
B. IS-IS SPF calculation is performed in three phases.
C. IS-IS works over the data link layer, which does not provide for fragmentation and reassembly.
D. IS-IS can never be routed beyond the immediate next hop.
Answer: C,D
Explanation:
IS-IS runs directly over the data link alongside IP. On Ethernet, IS-IS packets are always 802.3 frames, with LSAPs 0xFEFE while IP packets are either Ethernet II frames or SNAP frames identified with the protocol number 0x800. OSPF runs over IP as protocol number 89.
IS-IS runs directly over layer 2 and hence:
- cannot support virtual links unless some explicit tunneling is implemented
- packets are kept small so that they don't require hop-by-hop fragmentation
- uses ATM/SNAP encapsulation on ATM but there are hacks to make it use VcMux encapsulation
- some operating systems that support IP networking have been implemented to differentiate Layer 3 packets in kernel. Such Oss require a lot of kernel modifications to support IS-IS for IP routing.
- can never be routed beyond the immediate next hop and hence shielded from IP spoofing and similar Denial of Service attacks
QUESTION NO: 218
Which command do you use to connect a dense-mode domain to a sparse-mode multicast domain?
A. none, because there is no such command
B. ip pim spt-threshold infinity
C. ip pim register dense-mode
D. ip pim dense-mode proxy-register
Answer: D
Explanation:
For IP PIM multicast, Cisco recommends Sparse-Mode over Dense-Mode. In the midst of our network migration, we have a new network operating in Sparse-Mode with Anycast rendezvous point (RP) but our existing network is still operating in Dense-Mode. To bridge two different modes across both PIM domains, we should use the ip pim dense-mode proxy-register command on the interface leading toward the bordering dense mode region. This configuration will enable the border router to register traffic from the dense mode region (which has no concept of registration) with the RP in the sparse mode domain.
QUESTION NO: 219
Which two statements about the function of a PIM designated router are true? (Choose two.)
A. It forwards multicast traffic from the source into the PIM network.
B. It registers directly connected sources to the PIM rendezvous point.
C. It sends PIM Join/Prune messages for directly connected receivers.
D. It sends IGMP queries.
E. It sends PIM asserts on the interfaces of the outgoing interface list.
Answer: B,C
Explanation:
In PIM ASM and SSM modes, the software chooses a designated router (DR) from the routers on each network segment. The DR is responsible for forwarding multicast data for specified groups and sources on that segment.
In ASM mode, the DR is responsible for unicasting PIM register packets to the RP. When a DR receives an IGMP membership report from a directly connected receiver, the shortest path is formed to the RP, which may or may not go through the DR. The result is a shared tree that connects all sources transmitting on the same multicast group to all receivers of that group. In SSM mode, the DR triggers (*, G) or (S, G) PIM join messages toward the RP or the source. The path from the receiver to the source is determined hop by hop. The source must be known to the receiver or the DR.
QUESTION NO: 220
Refer to the exhibit.
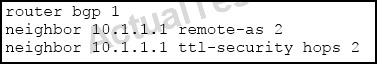
Which IP packets will be accepted from EBGP neighbor 10.1.1.1?
A. IP packets with a TTL count in the header that is equal to or greater than 253
B. IP packets with a TTL count in the header that is equal to 253
C. IP packets with a TTL count in the header that is equal to or greater than 2
D. IP packets with a TTL count in the header that is equal to 2
Answer: A
Explanation:
neighbor ip-address ttl-security hops hop-count
Example.
Router(config-router)# neighbor 10.1.1.1 ttl-security hops 2 Configures the maximum number of hops that separate two peers.
• The hop-count argument is set to number of hops that separate the local and remote peer. If the expected TTL value in the IP packet header is 254, then the number 1 should be configured for the hop-count argument. The range of values is a number from 1 to 254.
• When this feature is enabled, BGP will accept incoming IP packets with a TTL value that is equal to or greater than the expected TTL value. Packets that are not accepted are silently discarded.
• The example configuration sets the expected incoming TTL value to at least 253, which is 255 minus the TTL value of 2, and this is the minimum TTL value expected from the BGP peer. The local router will accept the peering session from the 10.1.1.1 neighbor only if it is 1 or 2 hops away.
QUESTION NO: 221
Refer to the exhibit.
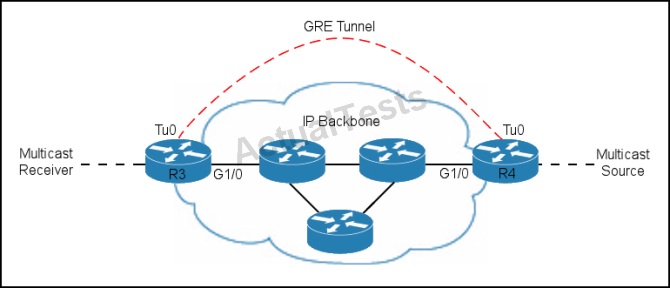 A tunnel is configured between R3 to R4 sourced with their loopback interfaces. The ip pim sparse-dense mode command is configured on the tunnel interfaces and multicast-routing is enabled on R3 and R4. The IP backbone is not configured for multicast routing.
A tunnel is configured between R3 to R4 sourced with their loopback interfaces. The ip pim sparse-dense mode command is configured on the tunnel interfaces and multicast-routing is enabled on R3 and R4. The IP backbone is not configured for multicast routing.
The RPF check has failed toward the multicast source.
Which two conditions could have caused the failure? (Choose two.)
A. The route back to the RP is through a different interface than tunnel 0.
B. The backbone devices can only route unicast traffic.
C. The route back to the RP is through the same tunnel interface.
D. A static route that points the RP to GigabitEthernet1/0 is configured.
Answer: A,D
Explanation:
For a successful RPF verification of multicast traffic flowing over the shared tree (*,G) from RP, an ip mroute rp-address nexthop command needs to be configured for the RP address, that points to the tunnel interface.
QUESTION NO: 222
Which option is the default number of routes over which EIGRP can load balance?
A. 1
B. 4
C. 8
D. 16
Answer: B
Explanation:
By default, EIGRP load-shares over four equal-cost paths. For load sharing to happen, the routes to load-share over must show up in the IP forwarding table or with the show ip route command. Only when a route shows up in the forwarding table with multiple paths to it will load sharing occur.
QUESTION NO: 223
When EIGRP is used as the IPv4 PE-CE protocol, which two requirements must be configured before the BGP IPv4 address family can be configured? (Choose two.)
A. the route distinguisher
B. the virtual routing and forwarding instance
C. the loopback interface
D. the router ID
Answer: A,B
Explanation:
A VRF must be created, and a route distinguisher and route target must be configured in order for the PE routers in the BGP network to carry EIGRP routes to the EIGRP CE site. The VRF must also be associated with an interface in order for the PE router to send routing updates to the CE router.
Prerequisites
Before this feature can be configured, MPLS and CEF must be configured in the BGP network, and multiprotocol BGP and EIGRP must be configured on all PE routers that provide VPN services to CE routers.
QUESTION NO: 224
Which three EIGRP packet types are valid? (Choose three.)
A. open
B. notification
C. keep-alive
D. hello
E. query
F. reply
Answer: D,E,F
Explanation:
EIGRP uses the following packet types: hello and acknowledgment, update, and query and reply. Hello packets are multicast for neighbor discovery/recovery and do not require acknowledgment. An acknowledgment packet is a hello packet that has no data. Acknowledgment packets contain a nonzero acknowledgment number and always are sent by using a unicast address. Update packets are used to convey reachability of destinations. When a new neighbor is discovered, unicast update packets are sent so that the neighbor can build up its topology table. In other cases, such as a link-cost change, updates are multicast. Updates always are transmitted reliably.
Query and reply packets are sent when a destination has no feasible successors. Query packets are always multicast. Reply packets are sent in response to query packets to instruct the originator not to recompute the route because feasible successors exist. Reply packets are unicast to the originator of the query. Both query and reply packets are transmitted reliably.
QUESTION NO: 225
Which term describes an EIGRP route that has feasible successors?
A. active
B. passive
C. redistributed
D. invalid
Answer: B
Explanation:
A topology table entry for a destination can have one of two states. A route is considered in the Passive state when a router is not performing a route recomputation. The route is in Active state when a router is undergoing a route recomputation. If there are always feasible successors, a route never has to go into Active state and avoids a route recomputation.
When there are no feasible successors, a route goes into Active state and a route recomputation occurs. A route recomputation commences with a router sending a query packet to all neighbors. Neighboring routers can either reply if they have feasible successors for the destination or optionally return a query indicating that they are performing a route recomputation. While in Active state, a router cannot change the next-hop neighbor it is using to forward packets. Once all replies are received for a given query, the destination can transition to Passive state and a new successor can be selected.
QUESTION NO: 226
Refer to the exhibit.
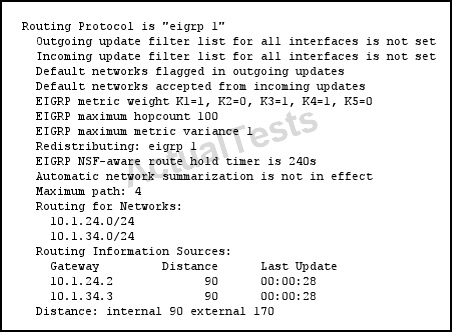 If EIGRP is configured between two routers as shown in this output, which statement about their EIGRP relationship is true?
If EIGRP is configured between two routers as shown in this output, which statement about their EIGRP relationship is true?
A. The routers will establish an EIGRP relationship successfully.
B. The routers are using different authentication key-strings.
C. The reliability metric is enabled.
D. The delay metric is disabled.
Answer: C
Explanation:
The 5 K values used in EIGRP are:
K1 = Bandwidth modifier
K2 = Load modifier
K3 = Delay modifier
K4 = Reliability modifier
K5 = Additional Reliability modifier
However, by default, only K1 and K3 are used (bandwidth and delay). In this output we see that K1, K3, and K4 (Reliability) are all set.
QUESTION NO: 227
Which type of OSPF packet is an OSPF link state update packet?
A. type 1
B. type 2
C. type 3
D. type 4
E. type 5
Answer: D
Explanation:
Link State Update packets are OSPF packet type 4. These packets implement the flooding of link state advertisements. Each Link State Update packet carries a collection of link state advertisements one hop further from its origin. Several link state advertisements may be included in a single packet.
QUESTION NO: 228
If two OSPF type 3 prefixes have the same metric, and are within the same process, which prefix(es) are installed into the routing table?
A. The route whose originator has the lower router ID.
B. Both routes are installed.
C. The route whose originator has the higher router ID.
D. The first route that is learned.
Answer: B
Explanation:
OSPF allows multiple equal-cost paths to the same destination. Since all link-state information is flooded and used in the SPF calculation, multiple equal cost paths can be computed and used for routing, and each route will be installed in the routing table.
QUESTION NO: 229
Which OSPF feature supports LSA rate limiting in milliseconds to provide faster convergence?
A. LSA throttling
B. incremental SPF
C. fast hello
D. SPF tuning
Answer: A
Explanation:
The OSPF Link-State Advertisement (LSA) Throttling feature provides a dynamic mechanism to slow down link-state advertisement (LSA) updates in OSPF during times of network instability. It also allows faster Open Shortest Path First (OSPF) convergence by providing LSA rate limiting in milliseconds.
QUESTION NO: 230
Which two options are BGP attributes that are updated when router sends an update to its eBGP peer? (Choose two.)
A. weight
B. local preference
C. AS_path
D. next-hop
Answer: C,D
Explanation:
AS_Path describes the inter-AS path taken to reach a destination. It gives a list of AS Numbers traversed when reaching to a destination. Every BGP speaker when advertising a route to a peer will include its own AS number in the NLRI. The subsequent BGP speakers who advertise this route will add their own AS number to the AS_Path, the subsequent AS numbers get prepended to the list. The end result is the AS_Path attribute is able to describe all the autonomous systems it has traversed, beginning with the most recent AS and ending with the originating AS.
NEXT_HOP Attribute specifies the next hop IP address to reach the destination advertised in the NLRI. NEXT_HOP is a well-known mandatory attribute that is included in every eBGP update.
QUESTION NO: 231
Which BGP aggregate address configuration advertises only the aggregate address, with attributes inherited from the more specific routes?
A. summary-only as-set
B. as-set
C. summary
D. summary-only
Answer: A
QUESTION NO: 232
Refer to the exhibit.
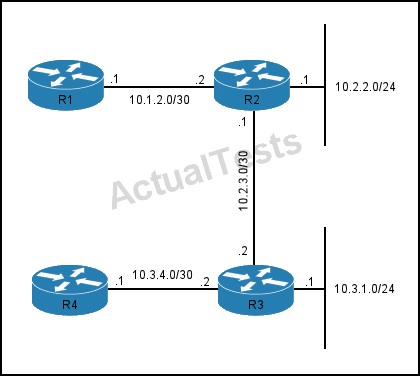 If ISIS is configured utilizing default metrics, what is the cost for Router 4 to reach the 10.2.2.0/24 network?
If ISIS is configured utilizing default metrics, what is the cost for Router 4 to reach the 10.2.2.0/24 network?
A. 1
B. 20
C. 30
D. 63
Answer: C
Explanation:
By default, every link is an IS-IS network has a metric of 10.
QUESTION NO: 233
Refer to the exhibit.
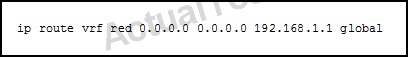 Which three statements about this configuration are true? (Choose three.)
Which three statements about this configuration are true? (Choose three.)
A. The default route appears in the global routing table.
B. The static route appears in the VRF red routing table.
C. The subnet 192.168.1.0 is unique to the VRF red routing table.
D. The static route is added to the global routing table and leaked from the VRF red.
E. The subnet 192.168.1.0 is unique to the global routing table.
F. 192.168.1.1 is reachable using any of the addresses on the router where the static route is configured.
Answer: A,B,E
Explanation:
This is an example of the route leaking feature. Here, this static route is created for the red VRF so it will be installed into the red VRF routing table, but the use of the global keyword will cause this default route to appear in the global routing table.
QUESTION NO: 234
Refer to the exhibit.
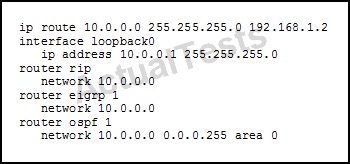 Which route type is displayed when you enter the command show ip route supernets-only on a device with this configuration?
Which route type is displayed when you enter the command show ip route supernets-only on a device with this configuration?
A. Connected
B. OSPF
C. RIP
D. EIGRP
E. An empty route set
Answer: E
Explanation:
This command shows supernets only; it does not show subnets. In this case, the routing table would contain the 10.0.0.0/24 subnet, but not the 10.0.0.0/8 supernet.
QUESTION NO: 235
Which statement about passive interfaces is true?
A. The interface with the OSPF passive interface configuration appears as a not-so-stubby network.
B. The interface with the EIGRP passive interface configuration ignores routes after the exchange of hello packets.
C. The interface with the IS-IS passive interface configuration sends the IP address of that interface in the link-state protocol data units.
D. Passive interface can be configured on the interface for IS-IS.
Answer: C
Explanation:
With IS-IS, passive interfaces are used to prevent unnecessary LSA packets out that interface, but the IP address of passive interfaces are still included in updates going out the other interfaces. This behavior is what enables the best practice of configuring loopback interfaces as passive, but still having the loopback be reachable.
QUESTION NO: 236
Refer to the exhibit.
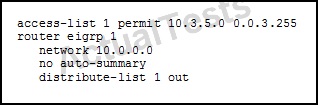 Which two routes are included in the route update? (Choose two.)
Which two routes are included in the route update? (Choose two.)
A. 10.3.0.0
B. 10.3.2.0
C. 10.3.4.0
D. 10.3.6.0
Answer: C,D
Explanation:
This access list will permit the 10.3.4.0, 10.3.5.0, 10.3.6.0, and 10.3.7.0 subnets.
QUESTION NO: 237
Which two statements about the metric-style wide statement as it applies to route redistribution are true? (Choose two.)
A. It is used in IS-IS.
B. It is used in OSPF.
C. It is used in EIGRP.
D. It is used for accepting TLV.
E. It is used in PIM for accepting mroutes.
F. It is used for accepting external routes.
Answer: A,D
Explanation:
To configure a router running IS-IS to generate and accept only new-style TLVs (TLV stands for type, length, and value object), use the metric-style wide command.
QUESTION NO: 238
You are tasked with configuring a router on an OSPF domain to import routes from an EIGRP domain and summarize the routes to 192.168.64.0.
Which statement configures the summarized route and provides equal-path route redundancy?
A. area 32 range 192.168.64.0 255.255.192.0 cost 100
B. area 32 range 192.168.64.0 255.255.63.0 cost 100
C. area 32 range 192.168.64.0 255.255.64.0 cost 100
D. area 32 range 192.168.64.0 255.255.192.0 multi-path
Answer: A
QUESTION NO: 239
Packets from a router with policy-based routing configured are failing to reach the next hop.
Which two additions can you make to the router configuration to enable the packets to flow correctly? (Choose two.)
A. Enable ip proxy-arp on the exiting interface.
B. Specify the next hop as an address.
C. Specify the next hop as an interface.
D. Add a match-any permit statement to the route map.
Answer: A,B
Explanation:
Here is an example:
Router(config)#route-map Engineers permit 20
Router(config-route-map)#match ip address 2
Router(config-route-map)#set interface Ethernet1
Here, instead of specifying a next-hop, it specifies that any packets matching this rule will be forwarded directly out the interface Ethernet1. This means that either the destination device must be on this segment, or there must be a router configured with Proxy ARP that can forward the packet to the ultimate destination.
QUESTION NO: 240
Which two options are EIGRP route authentication encryption modes? (Choose two.)
A. MD5
B. HMAC-SHA-256bit
C. ESP-AES
D. HMAC-AES
Answer: A,B
Explanation:
Packets exchanged between neighbors must be authenticated to ensure that a device accepts packets only from devices that have the same preshared authentication key. Enhanced Interior Gateway Routing Protocol (EIGRP) authentication is configurable on a per-interface basis; this means that packets exchanged between neighbors connected through an interface are authenticated. EIGRP supports message digest algorithm 5 (MD5) authentication to prevent the introduction of unauthorized information from unapproved sources. MD5 authentication is defined in RFC 1321. EIGRP also supports the Hashed Message Authentication Code-Secure Hash Algorithm-256 (HMAC-SHA-256) authentication method.