
نمونه سوالات آزمون
Implementing Cisco IP Switched Networks - exam 300-115
Topic 1, Layer 2 Technologies
QUESTION NO: 41
What does the command vlan dot1q tag native accomplish when configured under global configuration?
A. All frames within the native VLAN are tagged, except when the native VLAN is set to 1.
B. It allows control traffic to pass using the non-default VLAN.
C. It removes the 4-byte dot1q tag from every frame that traverses the trunk interface(s).
D. Control traffic is tagged.
Answer: D
Explanation:
The “vlan dot1q tag native” will tag all untagged frames, including control traffic, with the defined native VLAN.
QUESTION NO: 42
A network engineer has just deployed a non-Cisco device in the network and wants to get information about it from a connected device. Cisco Discovery Protocol is not supported, so the open standard protocol must be configured. Which protocol does the network engineer configure on both devices to accomplish this?
A. IRDP
B. LLDP
C. NDP
D. LLTD
Answer: B
Explanation:
The Link Layer Discovery Protocol (LLDP) is a vendor-neutral link layer protocol in the Internet Protocol Suite used by network devices for advertising their identity, capabilities, and neighbors on an IEEE 802 local area network, principally wired Ethernet. LLDP performs functions similar to several proprietary protocols, such as the Cisco Discovery Protocol (CDP).
QUESTION NO: 43
A manager tells the network engineer to permit only certain VLANs across a specific trunk interface. Which option can be configured to accomplish this?
A. allowed VLAN list
B. VTP pruning
C. VACL
D. L2P tunneling
Answer: A
Explanation:
When a trunk link is established, all of the configured VLANs are allowed to send and receive traffic across the link. VLANs 1 through 1005 are allowed on each trunk by default. However, VLAN traffic can be removed from the allowed list. This keeps traffic from the VLANs from passing over the trunk link.
Note: The allowed VLAN list on both the ends of the trunk link should be the same.
For Integrated Cisco IOS Software based switches, perform these steps:
1.To restrict the traffic that a trunk carries, issue the switchport trunk vlan-list interface configuration command.
This removes specific VLANs from the allowed list.
QUESTION NO: 44
For client server failover purposes, the application server team has indicated that they must not have the standard 30 second delay before their switchport enters a forwarding state. For their disaster recovery feature to operate successfully, they require the switchport to enter a forwarding state immediately. Which spanning-tree feature satisfies this requirement?
A. Rapid Spanning-Tree
B. Spanning-Tree Timers
C. Spanning-Tree FastPort
D. Spanning-Tree PortFast
E. Spanning-Tree Fast Forward
Answer: D
Explanation:
In order to allow immediate transition of the port into forwarding state, enable the STP PortFast feature. PortFast immediately transitions the port into STP forwarding mode upon linkup. The port still participates in STP. So if the port is to be a part of the loop, the port eventually transitions into STP blocking mode.
Example configuration:
Switch-C# configure terminal
Switch-C(config)# interface range fa0/3 - 24
Switch-C(config-if-range)# spanning-tree portfast
QUESTION NO: 45
Which command does a network engineer use to verify the spanning-tree status for VLAN 10?
A. switch# show spanning-tree vlan 10
B. switch# show spanning-tree bridge
C. switch# show spanning-tree brief
D. switch# show spanning-tree summary
E. switch# show spanning-tree vlan 10 brief
Answer: A
Explanation:
QUESTION NO: 46
A new network that consists of several switches has been connected together via trunking interfaces. If all switches currently have the default VTP domain name "null", which statement describes what happens when a domain name is configured on one of the switches?
A. The switch with the non-default domain name restores back to "null" upon reboot.
B. Switches with higher revision numbers does not accept the new domain name.
C. VTP summary advertisements are sent out of all ports with the new domain name.
D. All other switches with the default domain name become VTP clients.
Answer: C
Explanation:
By default, a switch will have a domain name of NULL and no password. If the switch hears a VTP advertisement it will automatically learn the VTP domain name, VLANs, and the configuration revision number.
Summary advertisements – sent out every 300 seconds and every time a change occurs on the VLAN database. Contained in a summary advertisement:
• VTP version
• Domain name
• Configuration revision number
• Time stamp
• MD5 encryption hash code
QUESTION NO: 47
A network engineer is setting up a new switched network. The network is expected to grow and add many new VLANs in the future. Which Spanning Tree Protocol should be used to reduce switch resources and managerial burdens that are associated with multiple spanning-tree instances?
A. RSTP
B. PVST
C. MST
D. PVST+
E. RPVST+
Answer: C
Explanation:
Multiple Spanning Tree (MST) extends the IEEE 802.1w RST algorithm to multiple spanning trees. The main purpose of MST is to reduce the total number of spanning-tree instances to match the physical topology of the network and thus reduce the CPU cycles of a switch. PVRST+ runs STP instances for each VLAN and does not take into consideration the physical topology that might not require many different STP topologies. MST, on the other hand, uses a minimum number of STP instances to match the number of physical topologies present.
Figure 3-15 shows a common network design, featuring an access Switch A, connected to two Building Distribution submodule Switches D1 and D2. In this setup, there are 1000 VLANs, and the network administrator typically seeks to achieve load balancing on the access switch uplinks based on even or odd VLANs—or any other scheme deemed appropriate.
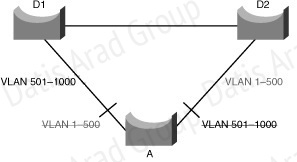
Figure 3-15 illustrates two links and 1000 VLANs. The 1000 VLANs map to two MST instances.
Rather than maintaining 1000 spanning trees, each switch needs to maintain only two spanning
trees, reducing the need for switch resources.
QUESTION NO: 48
Which statement about the use of SDM templates in a Cisco switch is true?
A. SDM templates are used to configure system resources in the switch to optimize support for specific features, depending on how the switch is used in the network.
B. SDM templates are used to create Layer 3 interfaces (switch virtual interfaces) to permit hosts in one VLAN to communicate with hosts in another VLAN.
C. SDM templates are used to configure ACLs that protect networks and specific hosts from unnecessary or unwanted traffic.
D. SDM templates are used to configure a set of ACLs that allows the users to manage the flow of traffic handled by the route processor.
E. SDM templates are configured by accessing the switch using the web interface.
Answer: A
Explanation:
You can use SDM templates to configure system resources in the switch to optimize support for specific features, depending on how the switch is used in the network. You can select a template to provide maximum system usage for some functions; for example, use the default template to balance resources, and use access template to obtain maximum ACL usage. To allocate hardware resources for different usages, the switch SDM templates prioritize system resources to optimize support for certain features.
QUESTION NO: 49
Which SDM template disables routing and supports the maximum number of unicast MAC addresses?
A. VLAN
B. access
C. default
D. routing
Answer: A
Explanation:
To allocate ternary content addressable memory (TCAM) resources for different usages, the switch SDM templates prioritize system resources to optimize support for certain features. You can select SDM templates to optimize these features:
• Access—The access template maximizes system resources for access control lists (ACLs) to accommodate a large number of ACLs.
• Default—The default template gives balance to all functions.
• Routing—The routing template maximizes system resources for IPv4 unicast routing, typically required for a router or aggregator in the center of a network.
• VLANs—The VLAN template disables routing and supports the maximum number of unicast MAC addresses. It would typically be selected for a Layer 2 switch.
QUESTION NO: 50
Which SDM template is the most appropriate for a Layer 2 switch that provides connectivity to a large number of clients?
A. VLAN
B. default
C. access
D. routing
Answer: A
Explanation:
To allocate ternary content addressable memory (TCAM) resources for different usages, the switch SDM templates prioritize system resources to optimize support for certain features. You can select SDM templates to optimize these features:
• Access—The access template maximizes system resources for access control lists (ACLs) to accommodate a large number of ACLs.
• Default—The default template gives balance to all functions.
• Routing—The routing template maximizes system resources for IPv4 unicast routing, typically required for a router or aggregator in the center of a network.
• VLANs—The VLAN template disables routing and supports the maximum number of unicast MAC addresses (clients). It would typically be selected for a Layer 2 switch.
QUESTION NO: 51
In a Cisco switch, what is the default period of time after which a MAC address ages out and is discarded?
A. 100 seconds
B. 180 seconds
C. 300 seconds
D. 600 seconds
Answer: C
Explanation:
To configure the aging time for all MAC addresses, perform this task:
Command
Purpose
Step 1
switch#configure terminal
Enters configuration mode.
Step 2
switch(config)#mac-address-table aging-timeseconds[vlanvlan_id]
Specifies the time before an entry ages out and is discarded from the MAC address table. The range is from 0 to 1000000;the default is 300 seconds. Entering the value 0 disables the MAC aging. If a VLAN is not specified, the aging specification applies to all VLANs.
QUESTION NO: 52
If a network engineer applies the command mac-address-table notification mac-move on a Cisco switch port, when is a syslog message generated?
A. A MAC address or host moves between different switch ports.
B. A new MAC address is added to the content-addressable memory.
C. A new MAC address is removed from the content-addressable memory.
D. More than 64 MAC addresses are added to the content-addressable memory.
Answer: A
Explanation:
mac-address-table notification mac-move
To enable MAC-move notification, use the mac-address-table notification mac-move command in global configuration mode. To disable MAC-move notification, use thenoform of this command.
mac-address-table notification mac-move[counter[syslog]]
no mac-address-table notification mac-move[counter[syslog]]
Syntax Description
counter
(Optional) Specifies the MAC-move counter feature.
syslog
(Optional) Specifies the syslogging facility when the MAC-move notification detects the first
instance of the MAC move.
Usage Guidelines
MAC-move notification generates a syslog message whenever a MAC address or host moves between different switch ports.
QUESTION NO: 53
Which option is a possible cause for an errdisabled interface?
A. routing loop
B. cable unplugged
C. STP loop guard
D. security violation
Answer: D
Explanation:
QUESTION NO: 54
What is the default value for the errdisable recovery interval in a Cisco switch?
A. 30 seconds
B. 100 seconds
C. 300 seconds
D. 600 seconds
Answer: C
Explanation:
After you fix the root problem, the ports are still disabled if you have not configured errdisable recovery on the switch. In this case, you must reenable the ports manually. Issue theshutdown command and then theno shutdowninterface mode command on the associated interface in order to manually reenable the ports.
The errdisable recovery command allows you to choose the type of errors that automatically reenable the ports after a specified amount of time. Theshow errdisable recoverycommand shows the default error-disable recovery state for all the possible conditions.
QUESTION NO: 55
Which statement about LLDP-MED is true?
A. LLDP-MED is an extension to LLDP that operates between endpoint devices and network devices.
B. LLDP-MED is an extension to LLDP that operates only between network devices.
C. LLDP-MED is an extension to LLDP that operates only between endpoint devices.
D. LLDP-MED is an extension to LLDP that operates between routers that run BGP.
Answer: A
Explanation:
LLDP for Media Endpoint Devices (LLDP-MED) is an extension to LLDP that operates between endpoint devices such as IP phones and network devices such as switches. It specifically provides support for voice over IP (VoIP) applications and provides additional TLVs for capabilities discovery, network policy, Power over Ethernet, and inventory management.
QUESTION NO: 56
Which statement about Cisco devices learning about each other through Cisco Discovery Protocol is true?
A. Each device sends periodic advertisements to multicast address 01:00:0C:CC:CC:CC.
B. Each device broadcasts periodic advertisements to all of its neighbors.
C. Each device sends periodic advertisements to a central device that builds the network topology.
D. Each device sends periodic advertisements to all IP addresses in its ARP table.
Answer: A
Explanation:
Cisco devices send periodic CDP announcements to the multicast destination address 01-00-0ccc- cc-cc, out each connected network interface. These multicast packets may be received by Cisco switches and other networking devices that support CDP into their connected network interface.
QUESTION NO: 57
Which option lists the information that is contained in a Cisco Discovery Protocol advertisement?
A. native VLAN IDs, port-duplex, hardware platform
B. native VLAN IDs, port-duplex, memory errors
C. native VLAN IDs, memory errors, hardware platform
D. port-duplex, hardware platform, memory errors
Answer: A
Explanation:
QUESTION NO: 58
Which option describes a limitation of LLDP?
A. LLDP cannot provide information about VTP.
B. LLDP does not support TLVs.
C. LLDP can discover only Windows servers.
D. LLDP can discover up to two devices per port.
Answer: A
Explanation:
QUESTION NO: 59
Which statement about the UDLD protocol is true?
A. UDLD is a Cisco-proprietary Layer 2 protocol that enables devices to monitor the physical status of links and detect unidirectional failures.
B. UDLD is a Cisco-proprietary Layer 2 protocol that enables devices to advertise their identity, capabilities, and neighbors on a local area network.
C. UDLD is a standardized Layer 2 protocol that enables devices to monitor the physical status of links and detect unidirectional failures.
D. UDLD is a standardized Layer 2 protocol that enables devices to advertise their identity, capabilities, and neighbors on a local area network.
Answer: A
Explanation:
The Cisco-proprietary UDLD protocol monitors the physical configuration of the links between devices and ports that support UDLD. UDLD detects the existence of unidirectional links. When a unidirectional link is detected, UDLD puts the affected port into the errdisabled state and alerts the user.
QUESTION NO: 60
Which option lists the modes that are available for configuring UDLD on a Cisco switch?
A. normal and aggressive
B. active and aggressive
C. normal and active
D. normal and passive
E. normal and standby
Answer: A
Explanation:
The Cisco-proprietary UDLD protocol monitors the physical configuration of the links between devices and ports that support UDLD. UDLD detects the existence of unidirectional links. When a unidirectional link is detected, UDLD puts the affected port into the errdisabled state and alerts the user. UDLD can operate in either normal or aggressive mode.